Microsoft Office 365 Ransomware Protection for Enterprises
Microsoft Office 365 environment is seemingly secure. However, your data is still vulnerable to certain cyber incidents, such as ransomware, human errors, and man-in-the-middle attack. In this guide for enterprises, we’ll discuss the best practices of Microsoft Office 365 ransomware protection.
Like a mutating virus as part of a pandemic, ransomware continues to evolve, gaining new capabilities and features and becoming more ominous. Many businesses are well underway in migrations to cloud environments to house their business-critical environments. Many organizations feel they are leaving the plague of ransomware behind when they migrate their critical data to the cloud. However, as we will see, cloud environments, in general, are also susceptible to ransomware attacks. What about Microsoft 365? Microsoft 365 cloud email, storage, and Microsoft Teams have seen a massive uptick in adoption. How can businesses protect their M365 environments?
Ransomware 2.0 and 3.0
Ransomware has evolved from the early days of ransomware attacks that perform simple file encryption of a victim’s computer. Attackers have now organized themselves into ransomware gangs or groups that function as actual businesses with marketing departments, developers, feature requests, etc. It is mind-boggling to think how far ransomware has evolved and the organization in place between attackers and ransomware groups.
One of the trends we have seen in the past few years is that ransomware groups have shifted focus away from individual PC users and focused their attention on large organizations. They realize that one successful attack on a large enterprise can yield payouts in the millions. Unfortunately, this tactic has proven to be successful many times over.
In recent times we saw ransomware attacks such as the attack on Colonial Pipeline in early May 2021, leading to a $4.4 million payday for attackers. While authorities recovered much of the ransom payment later, the attack showed disastrous consequences on critical infrastructure services, leading to fuel shortages for weeks.
A few short weeks later, on May 30th, the world’s largest meat company by sales, JBS, was hit by a ransomware attack, crippling its operations. JBS decided to pay the attackers $11 million in ransom payment, leading to disruption in products provided by JBS. These are just two examples of high-profile ransomware attacks that have led to disruptions, millions in damages, and a lost sense of confidence in defending against these types of attacks.
Aside from the change in tactics, attackers have also changed the technical capabilities of ransomware variants. New ransomware variants have capabilities that extend beyond the expected encryption behavior. Attackers are now employing what has been called double extortion. With the new double extortion tactics, ransomware 2.0, attackers are extorting businesses twice. First, they demand the usual ransom to unlock encrypted data locked with ransomware encryption. Then, they require payment to prevent confidential business information from being intentionally leaked to the Internet.
Double extortion techniques are proving highly effective. Why? With ransomware 1.0 and the encryption threat, businesses got wise to the fact they needed to have good backups to restore their data in the event of a ransomware attack. However, as attackers saw more organizations prepared to circumvent the threat of traditional ransomware, the new technique was born to threaten leaking data to the Internet.
The threat of exfiltrating data and intentionally leaking it to the Internet is a threat that backups cannot prevent. Data protected with enterprise backups does not prevent attackers who have invaded a corporate network from stealing or copying large amounts of data to their own server. Even if businesses can recover from the encryption aspect of a ransomware attack, they can still suffer untold damage from confidential files leaked to the Internet, exposing customers, trade secrets, financial information, and other highly sensitive information.
What is the cost of a data breach event? To highlight the financial repercussions of a data leak, note the following figures from the IBM Cost of a Data Breach Report 2021:
- The average total cost of a data breach increased by nearly 10% year over year
- The total cost of a breach in 2020-2021 was the largest single-year cost increase in the last seven years
- Data breach costs rose from $3.86 million to $4.24 million
- Healthcare organizations experienced the highest average cost of a data breach for the eleventh year in a row
- Healthcare data breach costs increased from an average total cost of $7.13 million in 2020 to $9.23 million in 2021, a 29.5% increase.
- Lost business resulted in 38% of the total cost of a data breach, at an average of $1.59 million
- The cost per record of personally identifiable information was $180
The traditional approach of only protecting against ransomware using backups is no longer effective in protecting organizations from the cost of a data breach that exposes information. Recovering data is only part of the problem. Preventing attackers from leaking large amounts of data is a second aspect that businesses must consider.
The alarming trend in ransomware is it continues to grow and adapt to compromise data wherever it may be found, including leaking and exfiltrating data. It includes cloud environments. Ransomware 3.0 will be “anything goes” and incorporate a mix and match of any techniques and breach tactics that allow attackers to keep the upper hand against businesses today.
Industry experts continue to see ransomware and other malicious activities continuing to increase. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion annually by 2025, up from $3 trillion in 2015.
Moving to the cloud does not solve ransomware
Many business leaders have mistakenly assumed that moving to the cloud solves the issue of ransomware. While cloud Software-as-a-Service (SaaS) environments provide many excellent capabilities and advantages to running resources on-premises, attackers have shown that cloud SaaS environments, including Microsoft 365 cloud email and storage, can be easy targets for cloud ransomware.
How can attackers compromise business-critical cloud SaaS environments, including cloud email and storage? The challenge comes with a modern authorization protocol used in most cloud environments today, including Microsoft 365. The protocol is OAuth. Google created the OAuth (Open-Authorization) protocol to solve many challenges of traditional user authentication. For example, with the wide range of third-party integrations and cloud apps available in cloud provider ecosystems such as the Microsoft AppSource marketplace, cloud providers needed a way to grant access to third-party applications without sharing sensitive data, like usernames and passwords.
OAuth authorization requests are the familiar prompts that most of us allow when prompted to grant permissions to apps requesting them. While OAuth itself is a secure protocol, and the process can provide a high level of security for integrating third-party solutions with cloud environments like Microsoft 365, most users blindly accept OAuth permissions prompts without carefully scrutinizing the permissions requested. As a result, when users accept permissions from third-party apps, it poses a security risk for your business.
Consider the consequences if a malicious application gets its hands on an OAuth token. It can use the OAuth token to masquerade as a legitimate user and access any information it has been granted when the initial permissions prompts were accepted. It means a malicious application with an adequate OAuth token can access an account, steal data, encrypt files and emails, and exfiltrate data from your business-critical SaaS environment.
Another dangerous and potentially scary characteristic of OAuth tokens is they also bypass two-factor authentication in cloud SaaS environments. It means users must manually remove them once granted. As a result, an attacker maintains a malicious foothold in the cloud SaaS environment once they possess a valid OAuth token.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
Microsoft Office 365 Ransomware Protection
Narrowing in further, is ransomware in Microsoft 365 environments possible? Yes, it is. Hacker turned security researcher Kevin Mitnick successfully demonstrated how easy it is for ransomware groups to use a combination of phishing emails with requests for OAuth tokens.
In what Mitnick called Ransomcloud, he demonstrated how easy it was to have your business email encrypted after granting OAuth authorization to a malicious ransomware cloud SaaS application. The malicious cloud SaaS application masqueraded as a legitimate app that persuades end-users to grant the permissions requested to their cloud SaaS environment.
A few moments after granting access to the malicious application, users would see their emails encrypted in real-time. After emails are encrypted, the user would receive a readable email describing the terms of the ransom payment, etc. No software is physically installed on the endpoint with the type of attack described. Instead, the malicious cloud SaaS application can communicate with the cloud SaaS APIs using the OAuth token granted by the user.
SpinOne is a solution that helps overcome the challenges of cloud ransomware and other cloud SaaS security risks. It is agentless and provides enterprise-grade protection against cloud ransomware and other cyber threats. At its core, it is driven by artificial intelligence (AI) and machine learning (ML) that provides robust and agile security controls that adapt to threats in real-time and provide automated responses.
The SpinOne solution to fight ransomware in the cloud is unique among competitors. It is the only solution that is built from the group up to seamlessly include Microsoft ransomware protection with domain monitoring, cloud-to-cloud backups, and automated recovery.
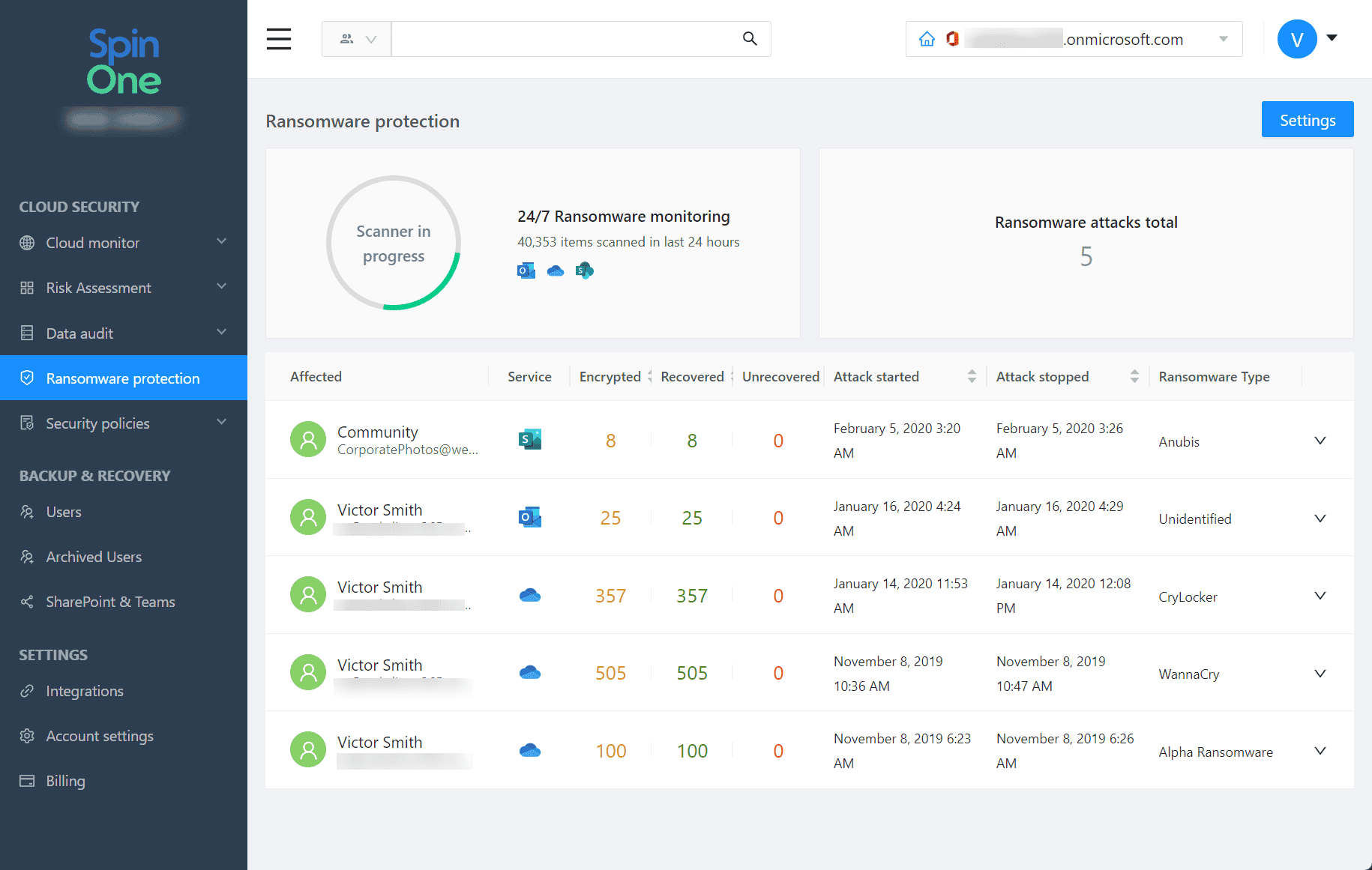
SpinOne is uniquely positioned to help protect businesses from the threat of double extortion in their cloud environments since it provides a way to recover data and stops malicious processes in their tracks before data can be leaked and encrypted. Note the following ways SpinOne Ransomware Protection helps to protect your Microsoft 365 environment:
- It monitors cloud SaaS environments for signs of ransomware 24/7/365
- When ransomware is detected, SpinOne blocks the ransomware source
- It automatically isolates assets affected by the ransomware attack
- Files are automatically restored to the latest backed-up version
- IT admins are immediately notified of incidents in real-time
- SpinOne provides granular SaaS security policy orchestration
Spin also:
- Reduces possible downtime from 21 days to 2 hours
- Helps reduce SaaS security management effort
- Reduces SaaS security management cost by 80%
- Provides integrated ransomware detection, cloud backup, and restore
The SpinOne Ransomware Protection module requires little configuration and starts protecting your environment immediately after being enabled. In addition, it allows IT admins to create domain-level policies to control ransomware protection in their Microsoft 365 organization.
In addition to the Ransomware Protection module, SpinOne provides a very powerful way to control with cloud SaaS apps users are allowed to install in the organization. Not only does this help to protect against malicious applications, but it also helps to protect your environment from Shadow IT operations by users, which is a tremendous concern in cloud SaaS environments. Learn more about how SpinOne can protect your business from the threat of malicious cloud SaaS apps, ransomware, Shadow IT, and many other threats here: Cloud Ransomware Protection for SaaS Data
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...


