New Office 365 Risk Assessment feature in SpinOne
Seemingly safe environment, Office 365 might bear hidden risks. One of the key sources is OAuth cloud applications. The current native tools don’t have the functionality to evaluate these apps. That’s why companies need a third-party solution. In this article, we would talk about Office 365 risk assessment, the new data protection feature of the SpinOne platform.
Cloud Software-as-a-Service environments have gained tremendous popularity, especially over the past two years, as businesses have accelerated their migrations to the cloud. Cloud SaaS offers outstanding features and capabilities, allowing companies to move forward in an agile, flexible, and modern way to provide remote and in-house workers with current productivity, communication, and collaboration tools. However, along with the robust features of modern cloud SaaS, companies must think about the cybersecurity and compliance risks with cloud SaaS applications.
Third-party cloud SaaS apps – powerful but can introduce risk
One of the compelling features of cloud Software-as-a-Service (SaaS) environments is the vast catalog of third-party apps that can integrate with the cloud SaaS environment. It means that businesses can extend and add features to their cloud SaaS environment with only a few clicks and a credit card, in the case of paid apps. You can think of it as an ala carte approach to picking your cloud apps that are right for your business needs and use cases.
Below is a look at the Microsoft 365 AppSource, a catalog of thousands of cloud SaaS apps offered in Microsoft 365. Organizations have access to all types of third-party applications across various categories, including Analytics, Collaboration, Content Management, CRM, Customer Service, File Managers, Finance, Human Resources, IT & Management Tools, Learning & Training, Marketing, News & Weather, Operations & Supply Chain, Productivity, Project Management, and many others.
Microsoft 365 AppSource third-party cloud apps catalog
If a feature or function is not included natively in Microsoft 365, organizations will likely find a third-party application that contains the features needed. In fact, most software vendors have cloud SaaS apps that integrate with the major cloud SaaS solutions on the market, such as Google Workspace and Microsoft 365.
While there is no questioning the added business value for your cloud SaaS environment, the ease of installing and integrating cloud SaaS apps in cloud SaaS environments introduces cybersecurity risks. Attackers can use malicious cloud SaaS apps and OAuth authorization theft to introduce malicious code into your environment, stealing or encrypting business-critical data.
In addition, there is the risk of compliance violations as data may be accessed or viewed in a way that violates compliance framework requirements (e.g., ISO 27001). Therefore, aligning with regulatory compliance regulations is extremely important, and gross negligence can be costly. For example, a GDPR violation with gross negligence can lead to a €20 million fine or 4% of worldwide annual revenue, whichever is more.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
The threat of malicious third-party cloud SaaS apps
With the massive cloud SaaS adoption, attackers are now shifting a large portion of their focus to compromising data and services in the cloud, including SaaS. You may wonder how criminals can get an organization to install a malicious third-party cloud SaaS app. Attackers often use phishing emails to entice end-users to click a link to “install” a malicious app masquerading as a legitimate application or update. Unfortunately, cybercriminals have become adept at crafting emails with the appearance of legitimacy. These can fool even technically savvy end-users.
Phishing emails go hand-in-hand with malicious cloud apps
Note the following statistics concerning phishing attacks:
- 83% of organizations experienced a successful email-based phishing attack in 2021
- 86% of organizations faced bulk phishing attacks last year
- 79% of organizations saw spearphishing attacks
- Over 90% of targeted attacks start with email
After an attacker coaxes an end-user into clicking a link in a phishing email, the attacker is after a special login known as an OAuth authorization token. What is OAuth? The OAuth authorization protocol allows third-party apps and other software to access resources on our behalf without knowing our password. Most have seen OAuth prompts without realizing it. An OAuth token is granted when applications prompt for permissions requests and access privileges in cloud environments. For example, they may look like the following permissions request in Microsoft 365:
Permissions request for a Microsoft 365 cloud SaaS application
The problem with OAuth permissions requests is that end-users rarely scrutinize them. Due to the mobile device era leading into cloud SaaS, users generally grant the permissions requested by apps, regardless of the permissions level. As a result, it provides an attacker easy access to an OAuth token on behalf of the user, with all the user’s permissions granting the request.
Additionally, while multi-factor authentication is undoubtedly a recommended cybersecurity best practice, OAuth tokens bypass it, making them even more dangerous when they fall into the wrong hands. An attacker with an OAuth token in your environment has access to the resources without a multi-factor prompt until the token is manually revoked.
The danger of OAuth authorization falling into the wrong hands helps to emphasize the need for organizations to scrutinize third-party apps installed in the cloud SaaS environment.
Shadow IT
Another huge risk with cloud SaaS applications is Shadow IT. Shadow IT includes end-users using software or applications not sanctioned by IT. As a result, the ease of installing third-party applications from a cloud SaaS marketplace is a double-edged sword. By default, users can install any third-party app from the marketplace.
This ability can lead to departments or users simply supplying a credit card and integrating a third-party app into the SaaS environment without visibility or permission from IT. It also means the proper cybersecurity or compliance scrutiny has not been given to the app. Even if the app is legitimate, it could unexpectedly grant access to sensitive data. Or, it may have a low reputation for risky application behavior.
Businesses must be able to control and limit the ability of users in the environment to install any application from the marketplace, as this places business-critical data at risk of data leak and compliance violations.
Automated Office 365 Risk Assessment with SpinOne
Manually performing a risk analysis of every application in the Microsoft 365 AppSource would be tedious and infeasible. In addition, application risks may change over time. An app that is safe today may be risky tomorrow based on its behavior.
SpinOne has announced the release of Risk Assessment App for Office 365. This brand-new offering provides IT admins with robust features and functionality to protect Office 365 environments from risky third-party apps. With SpinOne Risk Assessment for Office 365, businesses have a truly automated solution that performs the heavy-lifting by automatically assessing and scoring the thousands of apps available in the Microsoft AppSource marketplace.
SpinOne Risk Assessment for Office 365 features
The new Risk Assessment for Office 365 with SpinOne provides the ultimate visibility to cloud SaaS applications integrated with your environment. In addition, it provides a platform for automated risk assessments of thousands of Office 365 applications. Finally, it provides valuable security and compliance insights as well as various remediation methods to resolve issues with cloud SaaS applications integrated with the environment, including the following:
- It provides a list of all applications with access to business-critical or sensitive SaaS data
- It allows IT admins to see which SaaS users have access to the application in the environment
- You can gain insights into the app’s usage, including when the Office 365 cloud SaaS app was last accessed and when the OAuth token was last refreshed
- You can perform a comprehensive assessment of over twenty different categories, including factors related to possible business, security, or compliance risks for a particular application
- It allows understanding the full scope of permissions the cloud SaaS application requests upon installation
- Allow or Block specific cloud SaaS apps granularly, including for everyone in the organization or certain users/security groups
- You can view the users with access to the application
- It allows providing feedback on a specific cloud SaaS app’s risk assessment score
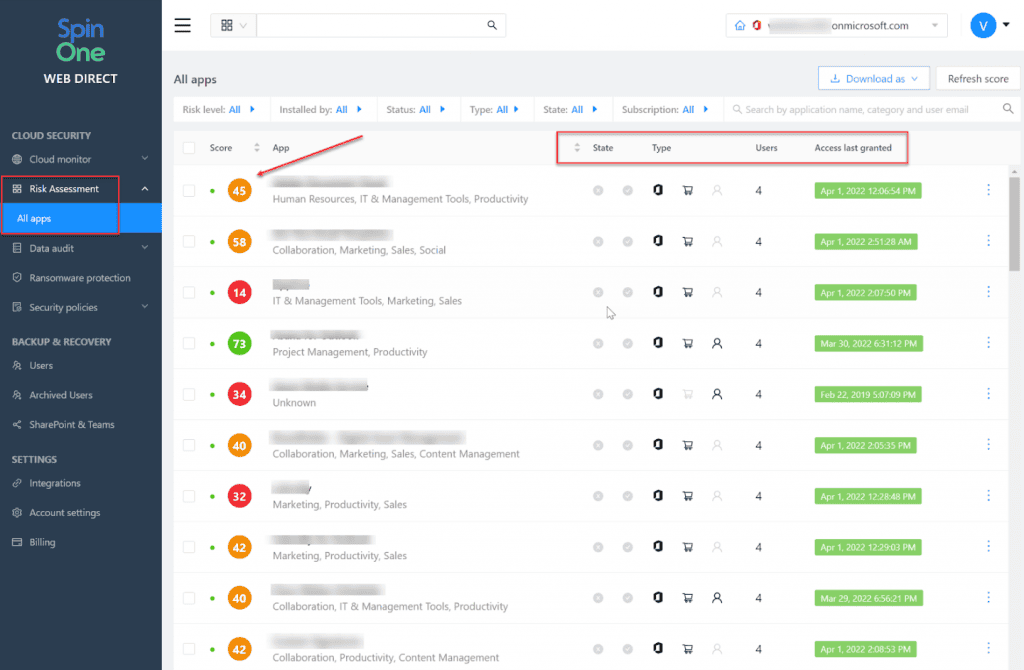
Below, the Risk Assessment feature in SpinOne for Office 365 allows quickly seeing the risk score for cloud SaaS applications and the following:
- Status – A green circle indicates the application is currently active and has access to data. A gray circle indicates inactive apps.
- Score – The risk score associated with the application resulting from the assessment. The higher the score, the fewer risks it can impose.
- Name & Category – The Office 365 name along with the category, if detected
- State – The state notes if the application has been sent to the Allowlist/Blocklist classifications.
- Type – The type section is broken down into three sections. First, it will show whether the app is an Office Service Principal App vs. an Office Teams App. The other two sections will display whether the app is installed from the official Microsoft marketplace (https://appsource.microsoft.com/en-cy/home) and will show if an administrator has installed the application for everyone in the organization.
- Users – View how many users have access to the application
- Access last granted – Metrics as to when the OAuth token between users and the app was last refreshed
- Settings – Allows extracting the list of all apps to a local device, or refreshing all apps in your organization
SpinOne Risk Assessment for Office 365
Using the new Risk Assessment for SpinOne provides organizations with a powerful tool to take control of third-party apps in Office 365. Without automation, businesses simply can’t keep up with the sheer number and variety of Microsoft 365 AppSource marketplace apps. With the SpinOne Risk Assessment for Office 365, the risk assessment is continuous and automated, allowing businesses to perform effective automated risk assessments to enhance their cybersecurity and compliance posture. Learn more about the new SpinOne automated Risk Assessment for Office 365 here: SpinOne for Microsoft Office 365
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...


