SaaS Application Security: How to Protect Google Workspace & Office 365 from Malicious Apps

In this guide, we discuss the essentials of SaaS application security. Learn about Google Apps Security & Office 365 Data Security and Risk Assessment.
Cloud Software-as-a-Service (SaaS) environments provide businesses with exciting features and capabilities, allowing them to move with a velocity that can be difficult to achieve with on-premises technologies. Especially over the past two years or so, with the shift to a distributed hybrid workforce, cloud SaaS environments have been the key to maintaining productivity and communication among distributed team members. Also, companies can take advantage of the rich integrations from third-party apps in the cloud SaaS marketplace. However, despite the tremendous benefits of third-party applications, businesses need to consider the security and compliance implications.
Why use third-party cloud SaaS applications?
First, why do organizations use third-party cloud SaaS applications? Google Workspace (formerly G Suite) and Microsoft 365 (formerly Office 365) have application marketplaces that provide organizations access to hundreds of third-party applications. These third-party apps allow businesses to extend, augment, and broaden the features found natively in cloud SaaS environments. Even though hyper-scale providers like Google and Microsoft provide a long list of services and features, organizations may still need missing functionality for their business productivity and communication workflows.
The marketplace apps offered by third-party software companies allow integrating these applications into the native cloud SaaS environment to provide the additional functionality and features needed. Below is an example of the Google Workspace Marketplace. Additionally, businesses can choose from an ala carte offering of software applications to extend the features found in Google Workspace.
Notice the wide range of tools, including:
- Accounting & finance
- Administration & management
- ERP & logistics
- HR & legal
- Marketing & analytics
- Sales & CRM
- Creative tools
- Web development
- Office applications
- Task management
- Communication tools
- Utilities
These are just a few of the categories found in Google Workspace. Microsoft 365 is similar with a wide range of third-party applications companies can use to have everything they need for empowering end-users with tools and applications needed.

Risks of third-party applications
Third-party cloud SaaS apps bring tremendous value to cloud SaaS environments when businesses use them securely. However, third-party applications can introduce enormous risks if not introduced correctly into the cloud SaaS environment. What risks are associated with third-party applications?
Let’s take a look at the following risks associated with third-party applications integrated with cloud SaaS:
- Malicious apps
- Shadow IT
- Data breaches
- Lack of risk assessments
Malicious apps
While Google and Microsoft filter through applications that make their way into the cloud SaaS marketplace, malicious apps can still slip through it. However, a more likely scenario that malicious apps find their way into the enterprise is an attacker leveraging a phishing attack against a cloud SaaS user and masquerading a malicious cloud SaaS app as a legitimate app.
Consider a scenario. A cloud Saas user receives a new email to their cloud email inbox. The email proposes to be from the cloud SaaS vendor directing the user to install a security “upgrade” to their cloud email environment. The user is persuaded to grant the cloud SaaS app permissions it requests. The user may see something similar to the following.
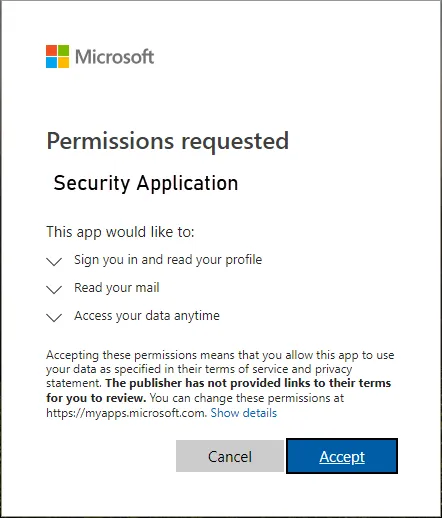
Most cloud SaaS environments like Google Workspace and Microsoft 365 allow users to install any cloud SaaS app. To protect Google Workspace and Microsoft 365 from malicious apps, organizations must maintain visibility to cloud SaaS applications and control which apps are installed in the SaaS environment.
The permissions request is an OAuth permissions request where the application is requesting an OAuth token, a specialized authorization token so the application can access the environment without your password. In this case, it is essential to realize that the malicious cloud SaaS application does not have to exist in a properly sanctioned marketplace from a hyperscaler. Attackers can externally host malicious code that can integrate into cloud SaaS environments. These Software-as-a-Service integrations are specialized applications that can communicate with cloud SaaS APIs. They simply need the OAuth token to have permission to perform malicious operations in the environment.
Most cloud SaaS environments like Google Workspace and Microsoft 365 allow users to install any cloud SaaS app. To protect Google Workspace and Microsoft 365 from malicious apps, organizations must maintain visibility to cloud SaaS applications and control which apps are installed in the SaaS environment.
Shadow IT
Another danger coming from third-party cloud SaaS apps is Shadow IT. Shadow IT in the context of cloud SaaS apps is any cloud application used by an end-user to perform work-related tasks without the knowledge or approval of your in-house IT team. It is a dangerous notion for businesses today tasked with stringent compliance and SaaS data security requirements.
The world of cloud Software-as-as-Service (SaaS) has created easy opportunities for Shadow IT to creep into the enterprise. Now, users can install virtually any app they want into their cloud account, especially with default, unfettered access to cloud SaaS marketplaces in Google Workspace and Microsoft 365. Whereas in on-premises environments where IT can control network traffic in and out and software installed on workstations, cloud SaaS environments do not provide the built-in tools for IT to have this type of control.
All a user or a department head needs to do is provide a credit card number for the third-party solution, and a few clicks later are up and running with a third-party app integrated with business-critical data. Some of the apps are even free to use. It is dangerous for enterprise businesses looking to keep data access and security aligned with compliance and their company’s security policies.
In this wide-open cloud SaaS app access model, IT may not have visibility or control over any apps integrated into the environment. As a result, even if an app is not malicious, it may be granted access to sensitive corporate data, increasing the risk of data leakage. As a result, organizations must implement the tools and solutions needed to control and gain visibility to cloud SaaS app usage.
Data breaches
Even legitimate applications, when granted permission to access corporate data, may pose the threat of data breaches. Third-party apps may be inadvertently granted permission to access sensitive data or copy the data from the cloud environment to another external location. This data access may go against compliance requirements and, even worse, lead to unexpected data breaches.
What is the cost of data leaks outside your organization? Note the following statistics from the IBM Cost of a Data Breach Report 2021:
- Data breach costs rose from $3.86 million to $4.24 million in 2020-2021
- Healthcare has the highest cost at $9.23 million in 2021, an increase of 29.5%
- The average cost of a breach in hybrid cloud environments topped $3.61 million
- The average cost of a breach at organizations with 81-100% of employees working remotely was $5.54 million
These costs are not insignificant. When you factor in the often immeasurable cost of lost customer confidence and tarnished brand reputation, the effects of a publicly disclosed data breach can last for years. They may even lead to a business being unable to recover.
Lack of risk assessments
A proper risk assessment allows businesses to understand their cybersecurity posture. Without a proper risk assessment, security vulnerabilities and risks may go unnoticed. They can lead to the disastrous outcomes we have already mentioned, such as malicious software attacks and data breaches.
Many businesses struggle with proper cybersecurity when migrating to cloud environments because traditional tools and processes do not translate in the cloud. In addition, the cloud comes with its own toolset, processes, technologies, and security challenges.
It can be daunting for organizations to perform a proper risk assessment for every single app found in cloud SaaS marketplaces. If done correctly, it may require countless hours for internal security teams to manually perform risk assessments of cloud SaaS apps. Using automated solutions to conduct risk assessments can help ease the burden of properly assessing cloud applications and choose solutions that align with your organization’s security policies.
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
SaaS Application Security: Protect G Suite and Office 365 from Malicious Apps with SpinOne
Attackers are targeting cloud infrastructure and cloud SaaS environments more frequently with malicious applications such as ransomware. Since businesses are storing more critical data in the cloud, and attackers know this, protecting cloud data is crucial.
SpinOne is a next-generation cybersecurity solution protecting cloud SaaS solutions like Google Workspace and Microsoft 365 from malicious apps. It provides automated risk assessment and access management for cloud SaaS apps and browser extensions. As a result, it saves countless hours for SecOps teams providing risk assessments, lowering the risk of zero-day attacks, and bolsters compliance.
Note the following features:
- Application scoring – Spin provides 24/7/365 monitoring and automated risk assessments of cloud SaaS apps, helping to have full visibility of Shadow IT operations
- Access management – It provides the controls and enforcement needed to blocklist risky applications and browser extensions for business-critical data
- Security policies – You can create granular security policies to allow/block apps based on defined criteria and set Microsoft 365 DLP and Google Workspace DLP.
- Zero-day mitigation – Prevent risks of zero-day exploits due to vulnerable or risky applications
- Compliance – You define the compliance posture of your cloud SaaS apps by only allowing apps to be installed that meet your compliance requirements and data governance regulations
- Approval process – Spin provides a built-in approval process allowing end-users to communicate and send requests for approval of application access
- Visibility and monitoring – Spin provides admins with full visibility to app security history, apps used in the organization, and which users are using which apps.
- Alerts and reporting – It allows admins to be alerted and notified of security incidents and allows creating reports for auditing and compliance purposes
SpinOne provides continuous risk assessments for cloud SaaS apps. Even if an app’s risk score is safe at one time, if it starts exhibiting risky behavior, Spin helps to provide visibility to this with the risk assessment automation it provides. In addition, it provides organization-wide policies that allow admins to block cloud SaaS apps that cross the risk score threshold defined by the business.
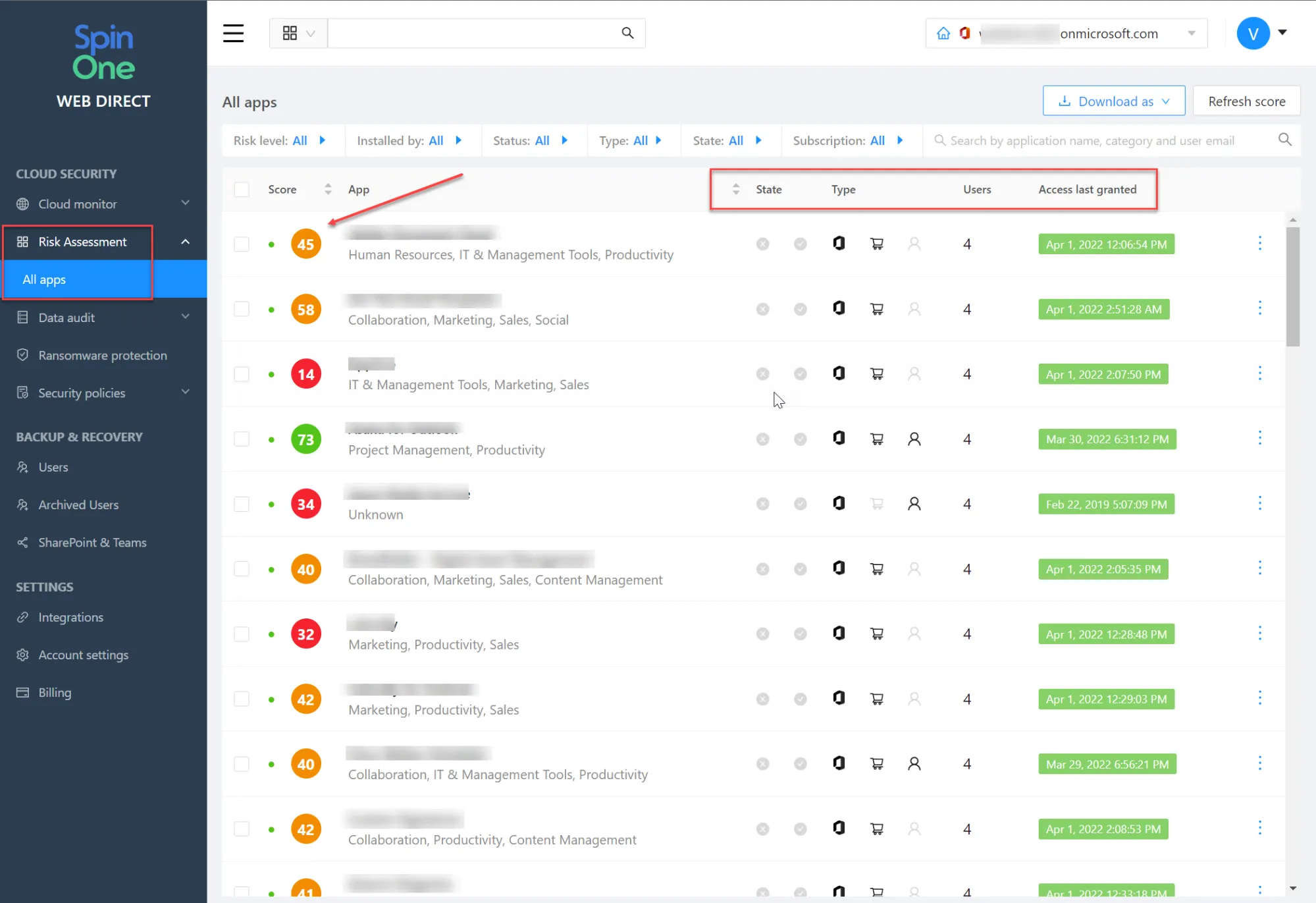
Protect cloud SaaS apps from malicious apps FAQs
What are cloud SaaS apps?
These are third-party applications available for installation in cloud SaaS environments. These allow extending the native features built into cloud SaaS environments and integrating specific software functionality the business needs for productivity, collaboration, and other purposes.
Can cloud SaaS apps have ransomware?
Yes, they can. Attackers can prey on end-users by masquerading malicious apps as legitimate applications safe for installation. Once they persuade a user to grant an OAuth token, the app has unfettered access to the environment with the user’s permission
How do you protect against malicious cloud SaaS apps?
Protecting against malicious cloud SaaS apps requires having the visibility and control needed to enforce which apps can be installed in the environment and which cannot. SpinOne provides a solution that provides automated risk assessments and scoring based on app behavior. Businesses can then use the automated risk assessment score to build robust security policies to define which apps can be installed in the environment.
What is a risk assessment?
A risk assessment is a formal discovery process where organizations analyze risks associated with business continuity. This process includes discovering vulnerabilities and the potential and likelihood of a cyberattack. It also includes discovering the risk associated with third-party services and applications used by the business to determine the security of these solutions.
Wrapping Up
Cloud Software-as-a-Service (SaaS) applications allow businesses to take advantage of all the cloud offers for productivity, collaboration, and communication. However, despite the benefits and capabilities of third-party cloud SaaS apps, businesses must perform proper risk assessments of any software integrated into their cloud environments. Having the right visibility and controls over which apps users can install helps prevent compromise from phishing attacks and OAuth credential abuse, leading to compromised SaaS environments or ransomware infections. The SpinOne automated risk assessment is an excellent example of a next-generation tool that organizations can use to protect their valuable cloud data from leaks or compromise.
To learn more about SpinOne’s automated risk assessment, take a look at the following article Google Workspace Apps Security | Google App Security Tool (spin.ai)
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...



