How to Monitor your SaaS Environment – Best Practices
Monitoring your environment, whether on-premises or in the cloud, is the “lifeblood” of cybersecurity. There is no visibility into user activities, potential malicious processes, and other anomalies without adequate monitoring. In addition, weak monitoring capabilities weaken the overall cybersecurity posture of an organization. Arguably, SaaS monitoring is the must-have for your business.
Let’s answer the following questions:
- Why is proper monitoring so crucial to cybersecurity?
- How can weak monitoring lead to data disaster in cloud SaaS?
- How can organizations strengthen cloud SaaS monitoring capabilities?
Why is proper monitoring so crucial to cybersecurity?
We cannot emphasize monitoring capabilities enough. Without proper monitoring, organizations are “flying blind” in their ability to defend and remediate their environment by cyberattacks. In a perfect world, there are no threats, and end-users are 100% secure in the way they carry out tasks, share files, and do other business-critical activities.
Unfortunately, the reality is we live in a world with escalating cyber threats, and employees may either accidentally or intentionally expose businesses to security risks. As a result, properly monitoring both on-premises and cloud environments is required for maintaining a strong cybersecurity posture.
Proper monitoring also allows an organization to understand what “normal” activity is and what actions, tasks, or connections could be abnormal. This ordinary activity is often referred to as a security “baseline” as it shows the state of regular activity. We could liken this to a “fingerprint” that identifies this state of normal activity.
If the fingerprint matches, the state of activity would indicate no active attacks or malicious activity. However, if the activity’s characteristics do not match, these can be triggered and can help quickly pinpoint malicious activity. As a result, proper monitoring helps SecOps determine if a cyberattack is underway, an employee is behaving unscrupulously, user credentials have been compromised, and many other cybersecurity incidents.
To put it simply, cybersecurity without monitoring is like data protection without backups. It won’t produce the desired result, and the outcome will be a very weak cybersecurity stance.
How can weak monitoring lead to data disaster in cloud SaaS?
Cloud SaaS environments are extremely powerful and exponentially growing as organizations expand to the cloud to solve complex business challenges such as remote work, allowing end-users to collaborate and communicate freely. Cloud SaaS environments allow businesses to move rapidly without the barriers to scalability and flexibility with legacy on-premises infrastructure.
With the rapid shift to cloud SaaS solutions, businesses lack visibility to end-user activities, data sharing, cloud applications integrated into the environment, and even malicious activity. Migrating to the cloud can be intimidating for many organizations. Businesses may inadvertently place the entire focus on keeping data intact and accessible as it is migrated to the cloud. As a result, cybersecurity can suffer as companies think about security as an afterthought instead of one of the primary requirements during cloud migration.
Cloud SaaS allows users to easily share data with team members and even those outside the organization. Unfortunately, this ease of sharing data can be an Achilles heel for businesses as data can easily leak from the sanctioned environment with little effort. In addition, many companies lack visibility as to where their data is shared and who is sharing it.
Also, end-users can easily install and integrate cloud applications and browser plugins in the cloud SaaS environment by default. But, again, while this can be a positive feature of cloud SaaS, it can turn into a cybersecurity concern as “shady” or even outright malicious cloud apps can easily be granted permissions to business-critical or even sensitive data.
Companies may have little or no visibility into the behavior of cloud SaaS applications, what reputation they have, or if the application is malicious. Therefore, monitoring both data sharing and cloud application behavior is an absolute necessity for effective cloud SaaS monitoring.
How can organizations strengthen cloud SaaS monitoring capabilities?
Organizations today must bolster their monitoring capabilities to strengthen their cybersecurity posture. Effective cloud SaaS monitoring requires certain key elements, including monitoring the following:
- Data visibility
- End-user activities and system events
- Cloud applications
- Malicious activity
1. Data visibility
Businesses need to have visibility to their data for cloud SaaS environments, especially data sharing and personally identifiable information (PII) data. Maintaining visibility of data sharing helps businesses prevent data leaks and understand potential cybersecurity risks with how data is shared internally and externally.
It includes flagging information that is classified as PII data. Current compliance regulations treat PII data as sensitive data that needs protecting at a high level. Failing to protect sensitive PII data can lead to severe penalties, such as the GDPR fine of €20 million or 4% of a business’s annual global turnover (whichever is higher).
2. End-user activities and system events
Maintaining visibility on end-user activities and system events helps businesses understand the overall baseline of normal end-user activity and generated system events. In addition, this overall visibility to activities helps organizations quickly key in on abnormal activities.
3. Cloud applications
As mentioned earlier, cloud applications are easy to integrate into cloud SaaS environments and help to extend the features and functionality offered. However, organizations must have a solid way to monitor cloud applications and browser plugins integrating into the environment.
Businesses also need to have the ability to control which applications are allowed in the organization and block applications that have undesirable behaviors or are all-out malicious or potentially contain ransomware.
4. Malicious activity
Any malicious activity must be treated with the highest level of cybersecurity attention and response. Businesses need solutions to respond to malicious activity, such as a ransomware attack, proactively. In the case of ransomware, each minute counts.
With modern ransomware threatening data leaks, stopping an attack as soon as possible helps ensure business-critical data isn’t leaked to the outside world. Businesses need to look at cybersecurity automation to stop ransomware and limit the scope of its damage quickly.
Modern cybersecurity monitoring for cloud SaaS with SpinOne
Native cloud cybersecurity tools can be disjointed and subscription-dependent as to their features and capabilities. When it comes to cybersecurity, organizations need a single-pane-of-glass interface that provides a unified view of their organization, activities, threats, risks, etc. SpinOne delivers robust data protection and data security for cloud SaaS environments. It enables businesses to have a single view of their data, compliance concerns, data sharing, PII information, and immediate data threats, such as ransomware.
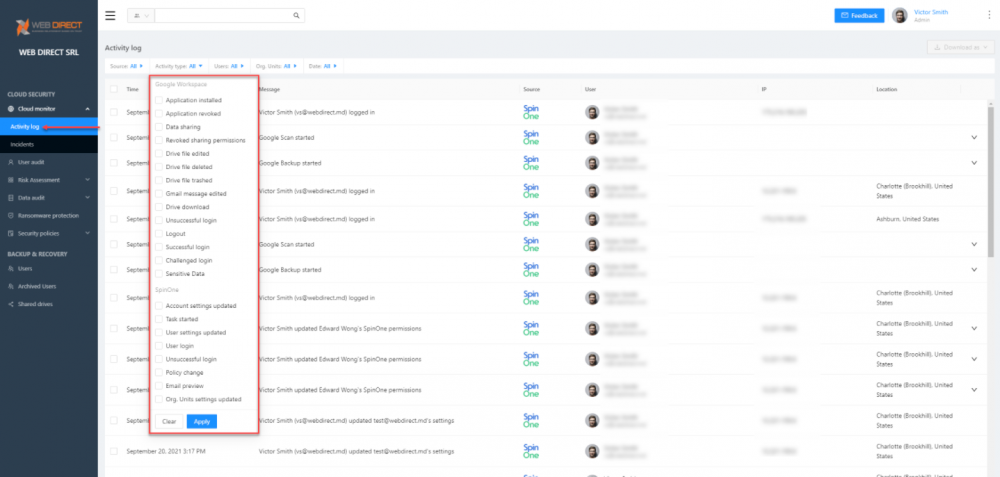
Cloud Monitor
SpinOne Cloud Monitor is a single view of both cloud SaaS activities and SpinOne events. This view provides a single-pane-of-glass view for monitoring activities happening in your cloud SaaS environment.
SpinOne cloud monitor dashboard
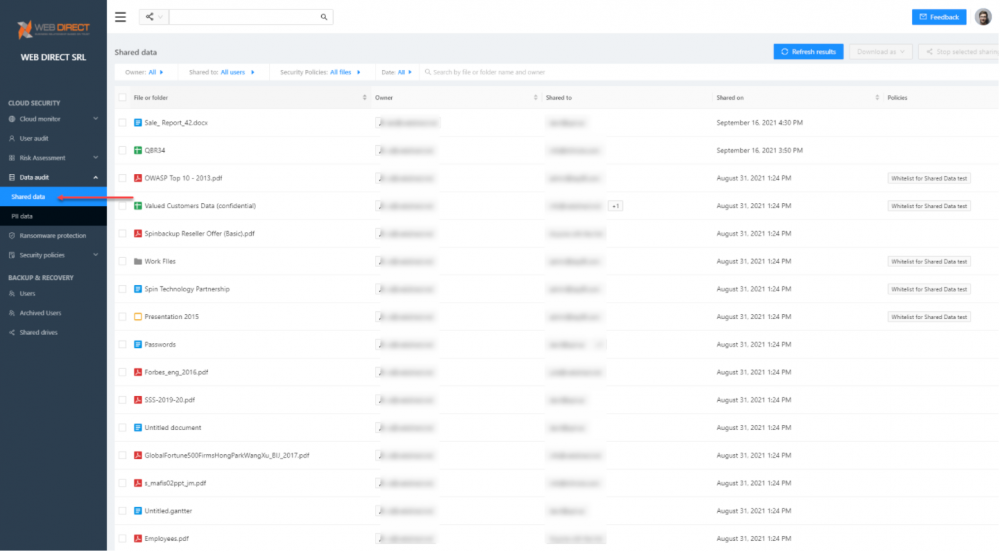
SaaS Data Audit
The SpinOne SaaS Data Audit dashboard allows monitoring data shared in the organization to internal and external users. It enables IT admins and SecOps teams to secure cloud SaaS environments and have the necessary visibility to prevent data leaks.
See relevant information for data sharing such as:
- File or folder
- Owner
- Shared to
- Shared on
- Policies
SpinOne Data audit dashboard
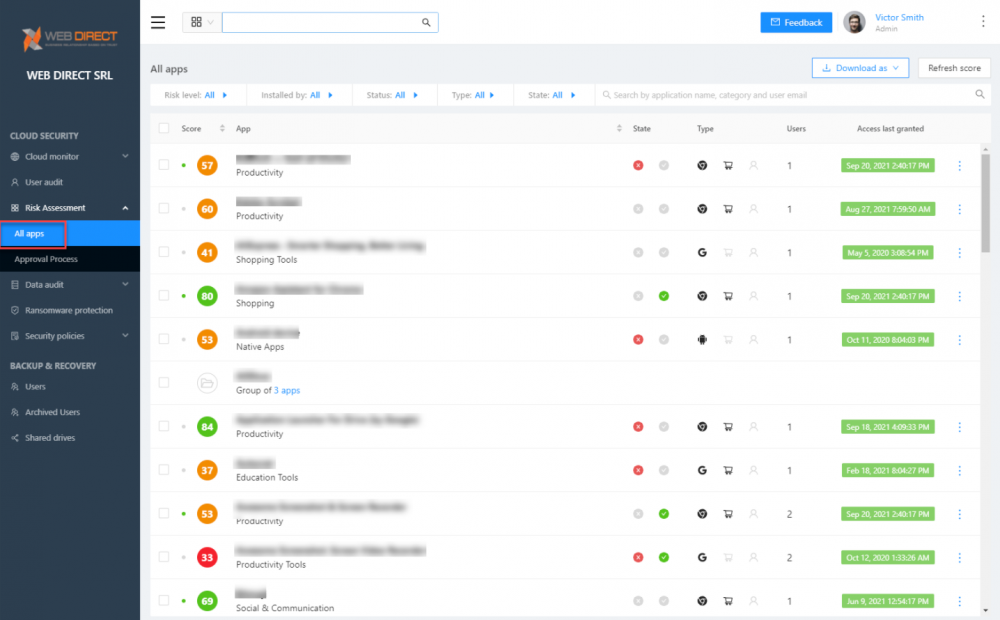
Cloud Applications
Robust cloud applications allow businesses to extend native cloud SaaS features and capabilities. However, they can introduce cybersecurity risks to your data. SpinOne provides an automated risk assessment and control module for cloud applications. It allows monitoring cloud app reputation, behavior, and activities. It also allows businesses to have the tools to block or allow specific cloud apps effectively.
SpinOne Risk assessment dashboard
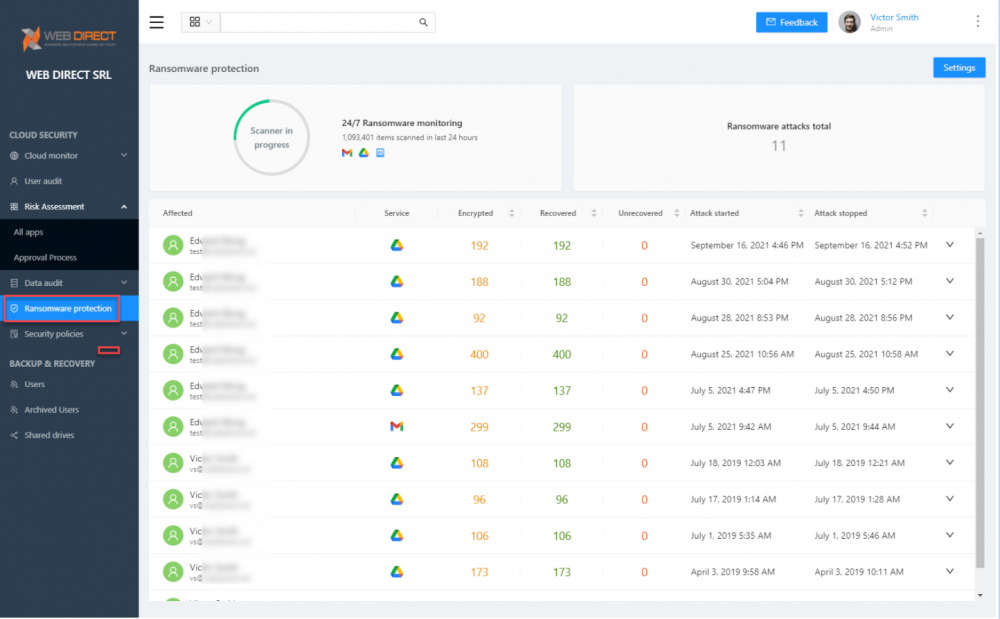
SaaS Ransomware protection
With SpinOne, you get industry-leading SaaS ransomware protection driven by powerful artificial intelligence (AI) and machine learning (ML) technology. In addition, SpinOne provides automated responses to ransomware attacks. When ransomware attacks your SaaS environment:
- SpinOne continuously scans for signs of ransomware
- Once detected, it blocks ransomware at the network level
- Files are automatically scanned
- Any affected files are automatically restored (configurable)
- IT admins are alerted
SpinOne SaaS ransomware protection
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....