Top New Ransomware Attacks and Threats

Cybersecurity threats that organizations are dealing with today are showing no signs of getting easier or better, for that matter. Cybercriminals are leveraging many new threats and attack vectors to compromise business-critical environments. Ransomware attacks are becoming a mainstay of the cybersecurity threat landscape, and attackers continue to use it to extort ransom demands from businesses worldwide.
Now, in 2022, organizations must stay on high alert for new ransomware attacks and weak security postures that give attackers easy access to critical systems and cloud environments. Let’s look at the top new ransomware attacks and threats to note for 2022.
Trends from 2021 continue in 2022
In a joint release from CISA (Cybersecurity and Infrastructure Security Agency), FBI (Federal Bureau of Investigation), NSA (National Security Agency, ACSC (Australian Cyber Security Centre), and the NCSC-UK (United Kingdom’s National Cyber Security Centre), a recent Cybersecurity Advisory notes the growing threat of ransomware worldwide.
- The advisory detailed the top trends and threats that allow attackers to gain access and launch cyberattacks, including ransomware. These include:
- Increased phishing activity, attacks based on compromised credentials, brute force attacks, and software vulnerabilities
- Ransomware operations are becoming more sophisticated and professional
- Increasing cooperation between ransomware gangs
- New approaches are targeting cloud environments, MSPs, industrial environments, and supply chains
- Ransomware groups are catching organizations off guard by launching attacks on holidays and weekends
As stated in the Cybersecurity Advisory by CISA Director Jen Easterly
“We live at a time when every government, every business, every person must focus on the threat of ransomware and take action to mitigate the risk of becoming a victim. Reducing risk to ransomware is core to CISA’s mission as the nation’s cyber defense agency, and while we have taken strides over the past year to increase awareness of the threat, we know there is more work to be done to build collective resilience. With our NCSC-UK, ACSC, FBI, and NSA partners, we urge organizations to review this advisory, visit stopransomware.gov to take action to strengthen their cybersecurity posture, and report unusual network activity or cyber incidents to government authorities.”
Critical new vulnerabilities such as Apache Log4j
In conjunction with the exponential growth of ransomware, new vulnerabilities are making it easier to compromise business-critical systems. For example, the timing couldn’t be worse for businesses with a new vulnerability that surfaced at the end of 2021. Organizations were alerted to a very dangerous vulnerability discovered with the Apache Log4j library, captured in CVE-2021-44228.
The sheer width and breadth of the Apache Log4j library usage across business-critical software systems are massive. This new and very dangerous vulnerability has left businesses scrambling to discover immediate software workarounds and patches if available.
You can view official Apache Log4j vulnerability guidance from CISA here: Apache Log4j Vulnerability Guidance | CISA
VMware Horizon has been cited as an “out of the gate” favorite among attackers for exploiting the Apache Log4j vulnerability with early attacks targeting organizations with unpatched VMware Horizon servers on the perimeter. Additionally, VMware Horizon has been a popular choice among businesses as a remote work solution during the pandemic, making it a perfect target for the new vulnerability.
Many posts have cited active exploits of the Apache Log4j vulnerability in the wild:
- Log4j flaw: Attackers are targeting Log4Shell vulnerabilities in VMware Horizon servers, says NHS | ZDNet
- Why VMware Horizon became a ‘top choice’ for Log4j attacks | VentureBeat
It helps to underscore the vigilance needed by organizations to new and emerging threats that may be disclosed with short notice and getting remediations in place as quickly as possible. Keeping critical systems patched and updated is also a crucial step.
Ransomware attacks in 2022 – off to a strong start
In 2022, there have been several high-profile ransomware attacks making headlines already. It helps to show the trend from 2021 is continuing and shows no signs of stopping in the future. Take note of the following major ransomware attacks ending out 2021 and leading into2022 so far:
- Crawford County – hit with ransomware sometime over Christmas holiday –
- Weldco-Beales – heavy equipment manufacturer – December 29, 2021 posting of compromise
- Impresa – Portuguese media group – January 1, 2022
- Bernalillo County New Mexico – January 5, 2022 –
- ThalesGroup aerospace – January 1, 2022
- Bay & Bay Transportation – Between December 2021 and January 2022
Crawford County
The Crawford county local government offices were hit with a ransomware attack at some point over the Christmas holidays. The ransomware attack left the government offices and services in disarray. The local MSP, Apprentice Computer solutions, has been reimaging and recovering systems since the attack was discovered early in 2022. As far as has been disclosed, no ransom has been paid in the attack.
Weldco-Beales
Weldco Beales is a Canadian heavy equipment manufacturer that was one of several companies listed as compromised by a new ransomware group known as Karakuurt. The post was made on December 29, 2021, on the Karakurt group’s website. It is still yet to be determined if Karakurt exfiltrated data. Weldco-Beales is still trying to determine if the ransomware group copied any data.
Impresa
Over the New Year’s holiday, Impresa, a Portuguese media company, was attacked by a lesser-known ransomware gang called Lapsus$. The ransomware group took over Impresa websites, posting ransom notes, and even claimed to have gained control over Impresa’s Amazon Web Services account. In addition, Lapsus$ is said to have exfiltrated over 50 terabytes of company data from Impresa. No ransom payment amount has been disclosed from either side.
Bernalillo County New Mexico
Bernalillo County New Mexico government offices discovered a ransomware attack on January 5, 2022. The attack impacted services for the more than 675,000 residents of Bernalillo County, including part of Albuquerque.
County offices were still dealing with the fallout of the attack more than two weeks after, with key services provided by the county still down.
Thales Group aerospace
Thales Group is a French multinational company that designs and builds electrical systems and services for aerospace, defense, transportation, and security markets. On January 17, 2022, the ransomware group known as LockBit 2.0 announced data leaked from the Thales Group. The company officially appeared on the LockBit 2.0 website on January 1, 2022. It appears the ransom demanded was around $1 million, which is fairly modest considering the size and sector in which the Thales Group operates. It may mean the data was not extremely important.
Bay & Bay Transportation
Bay & Bay Transportation is a company numbered in an alarming statistic – companies hit twice by ransomware in just a few short years. Bay & Bay Transportation was first hit by a devastating SamSam ransomware attack in 2018 that led to the business paying the ransom demanded.
The second attack is thought to have started around December 1, 2021. Even though the Conti ransomware variant spread more pervasively than the first attack in 2018, the company had better tools in place to deal with the second attack. In the second go-around, the company did not pay the ransom, and it had restored over 90% of services in just a day.
The second ransomware attack is thought to have exploited a known vulnerability in Exchange Server, allowing attackers to gain a foothold in the environment.
- Minnesota trucking company hit in 2nd ransomware attack – FreightWaves Conti ransomware. Compromised through a vulnerability in Exchange Server
Ransomware-as-a-Service (RaaS) and Initial Access Broker (IABs)
The trend in 2022 shows these attacks are growing more prevalent and getting easier for even novice cybercriminals. Why? The Ransomware-as-a-Service (RaaS) offering on the dark web allows attackers to consume Ransomware “as-a-Service,” without knowing how to develop, manage, and collect payments from ransomware on their own. In addition, ransomware groups who run the RaaS offerings collect a percentage of the ransom payments for their services.
Initial Access Brokers (IABs) commoditize network access to victims’ networks by selling access credentials on the dark web. The higher the permissions and system access level, the more costly the credentials. Attackers can use IAB credentials to gain access to a victim organization quickly and then launch a ransomware attack using the RaaS service.
These two offerings on the dark web have undoubtedly accelerated the sheer volume of ransomware attacks and their success rates across the board. Due to RaaS and IABs, ransomware has arguably become the most dangerous threat to modern businesses today.
Cloud is in the crosshairs
As mentioned earlier, the joint Cybersecurity Advisory outlined several threats to watch for in 2022. Of those, it noted, “ransomware groups are having an increasing impact thanks to approaches targeting the cloud, managed service providers, industrial processes and the software supply chain.” As a result, cloud environments are in the crosshairs of attackers.
Ransomware groups realize many organizations are increasingly hosting their business-critical data and services in cloud environments. Therefore, it stands to reason that attackers are focusing more on compromising cloud infrastructure. As demonstrated by the Impresa attack, ransomware groups can easily discover and go after cloud service accounts such as Amazon AWS and cloud Software-as-a-Service (SaaS) environments, such as Google Workspace and Microsoft 365.
Businesses must be vigilant to provide mission-critical backups and cybersecurity for their cloud infrastructure, including cloud SaaS environments.
Ransomware protection for cloud SaaS environments with SpinOne
Many organizations have migrated to or are in the process of migrating data to cloud SaaS environments without a clear-cut solution for providing mission-critical backups or cybersecurity protection. Some may even mistakenly assume that data stored in cloud SaaS environments is immune to ransomware and other threats.
Unfortunately, this is a risky assumption primarily based on misconceptions about how data is protected in the cloud and whose responsibility it is to protect the data and secure it. Ransomware can and does affect cloud SaaS data. The shared responsibility model places the burden of protecting and securing cloud SaaS data in the hands of the customer. At the end of the day, if your cloud data is encrypted by ransomware, you are ultimately responsible for recovery.
SpinOne provides cloud ransomware protection that is automated, agentless and is cloud-native. It provides a unique AI-driven solution that gives organizations the security controls needed to discover, adapt, and evolve to meet the challenge of stopping ransomware, taking the possible downtime SLAs from 21 days to 2 hours, and reducing management costs by as much as 90%.
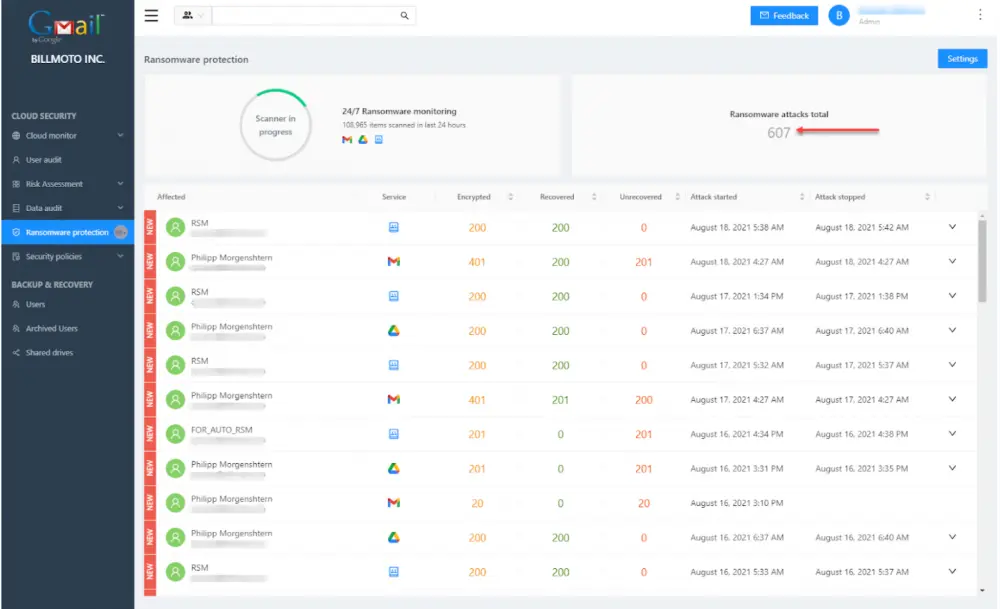
Note the following features:
- Designed from the ground up for cybersecurity in the cloud
- Provides AI-driven ransomware protection using domain monitoring, cloud-to-cloud backups, and automated recovery features
- Seamless and intuitive dashboard
- Provides SecOps teams with the tools to monitor, detect, and stop ransomware
- Offers unique, fully automated ransomware recovery capabilities
The fully automated ransomware recovery process includes the following:
- SpinOne ransomware protection monitors cloud SaaS environments for signs of ransomware 24/7/365
- If ransomware is detected, SpinOne blocks the ransomware network source
- It automatically isolates resources affected by the ransomware attack
- It automatically restores affected files to the latest backed up version
- It immediately notifies IT admins of ransomware events in real-time
- SpinOne provides granular SaaS security policy orchestration
With SpinOne ransomware protection and cloud-to-cloud backups, organizations can meet the needs of cybersecurity posture management in cloud SaaS environments and protect their critical data from attack. Learn more about SpinOne ransomware protection here: Cloud Ransomware Protection for SaaS Data- spin.ai
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


