Social Engineering: Definition, Examples, Types of Attacks and How to Prevent Them
Social engineering has become one of the most efficient attack vectors for cybercriminals. This article unpacks its types, techniques, and stages and provides the best methods to minimize the associated risks.
What is social engineering?
The term ‘social engineering’ is used in IT security and political science. In both fields, it means influencing the minds of humans to control them. People subject to social engineering are seen as justifiable targets of instrumentalization and manipulation.
In IT security, social engineering is a body of psychological manipulation methods to induce a specific target’s behavior.
Usually, it is a part of a ‘larger’ criminal scheme. The purpose of this crime is to obtain access to data that can be used to obtain money or achieve other goals. Social engineering attacks can happen both online and offline, the former bearing fewer risks for attackers.
For this article, we will differentiate between three terms:
- The target of social engineering attacks is the person that is being manipulated.
- The ‘victim’ is the entity (a person or organization they work at) harmed by the crime.
- The ‘victim by proxy’ is any third-party entity (person or organization) that was harmed as a result of the cybercrime.
Sometimes the victim and the target are the same person. For example, social engineers pretend to be an employee of a target bank and obtain the target’s credentials. Then they steal money from the target’s account. This happens mostly in cybercrime incidents against individuals.
In more complex schemes, the victim is usually an organization, and the target is its employee. For example, a double extortion ransomware attack uses social engineering against an employee to infect the IT environments of a company. In this case, the ‘target by proxy’ is a client of the company whose data was stolen by criminals and sold on the Dark Web.
Note this article’s scope is social engineering as an IT security phenomenon with a focus on cybercrime against organizations.
What are the origins of social engineering?
Social engineering uses deceit and manipulation on the one hand and trust and human weaknesses on the other. All these behaviors and psychological characteristics, along with our need for control, are the basics of human nature and possibly come from the deception techniques of other species. For example, some apes are capable of consciously lying.
Various ancient mythologies and religions told stories about social engineering as a warning against gullibility. The Trojan Horse and Eve eating the Apple are the most known examples in the West. Interestingly, Ancient Greeks praised lying and even created sophistry.
The more recent examples of social engineering include:
- The sale of the Eiffel Tower for metal scraps in 1925.
- The stealing of $10M from Security Pacific National Bank over the phone in the 1970s.
- 419 scam: cybercriminals request a target to make a small payment in return for a future share in a larger amount of money. The scam first started via regular mail and then turned to more modern technologies like email.
How has technology changed social engineering attacks?
The development of technology has facilitated social engineering attacks in the following ways:
1. Attacks became safer for criminals because technology provides anonymity. When a criminal doesn’t engage with their victim or target directly, there’s no that their face will be remembered and recognized or recorded on a security camera. Also, there’s no chance of leaving behind fingerprints, DNA, or other clues.
Payments using cryptocurrency also enable social engineers to remain in the shadows.
2. Technology enables criminals to target people all over the world. It enables them to act in countries with no or gray legislation on cybercrime and remain unpunished. Government-funded advanced persistent threat actors are even protected by their respective countries.
3. Technologies like deep fake enable criminals to impersonate various people successfully, e.g., in CEO fraud.
The Risks of Social Engineering Attacks
A single successful social engineering attack can have a severe impact on an organization. Here are some of the most widely spread:
1. Financial loss
A cyber attack can cause substantial financial losses, including loss of revenue due to the halt of operations, additional costs for incident response, and ransom payments to cyber criminals. In the case of industrial espionage, the company can suffer from the actions its competitors take after obtaining sensitive information.
2. Reputational loss
A cyber security incident negatively impacts the reputation of a company leading to the loss of potential and existing clients.
3. Downtime
After a security breach, an organization’s operations are suspended for some time. For example, a ransomware attack makes it impossible for people to work with the company’s data as it has been encrypted.
4. Legal implications
The quantity of laws and regulations governing IT security and data protection has been steadily growing over the past three decades. The government can additionally punish the victim of a social engineering attack for not taking necessary actions for data protection.
Victims by proxy of an attack can also sue the victim of an attack.
5. Impact on employees’ wellbeing
Crime causes distress in employees and impacts their performance. Some people even leave the organization after it has fallen victim to crime.
6. Termination of business
The impact of social engineering attacks can deteriorate organizations to the point when they terminate their operations. For example, in 2022, Lincoln College shut down after 157 years of work.
7. Impact on the dependants of an organization
Clients and partners of victims of social engineering attacks often become victims by proxy. It is especially severe in the case of hospitals, critical infrastructure, or service providers. For example, a ransomware attack on CommonSpirit, the electronic record system, wreaked havoc in many hospitals across the US.
How Social Engineering Works
Learn how criminals plan and carry out social engineering attacks, what techniques they use, and what weaknesses they exploit.
Stages of social engineering attacks
Usually, a social engineering attack has five stages:
Planning
Cybercriminals must devise the attack, choose the type of social engineering, and find tools to carry it out.
Gather intel
At this stage, cyber criminals mostly use OSINT (open source intelligence) techniques to learn about their targets and victims.
The company’s official website, LinkedIn and other social networking platforms, and employee review websites like Glassdoor are valuable sources of such information.
You can easily learn the address of the company’s offices, the names of the employees, their roles and contact information, and even some internal problems like high employee turnover or bosses that are not used to hearing ‘no.’
This valuable data can be used against your business. This stage can be elaborate, like CEO fraud or spear phishing, or minimal for less personalized attacks.
Establish Contact with the target
At this stage, a criminal contacts one or multiple targets via the chosen medium (email, phone, or in person). The social engineer tries to establish trust and rapport using multiple techniques and to collect the necessary information.
Attack the system
Once the target has given away the information, social engineers begin the penetration of the protected system. It can be a ransomware attack, a login into an account with attempts to steal documents, or transferring money from the victim’s account.
End of the contact
Cybercriminals might choose to end the contact with their target in a way that a target doesn’t suspect foul play. In this case, such a person will not react immediately and take necessary actions (like changing the password, calling a bank, or reporting the attack to the police).
What weakness does social engineering exploit?
Social engineering attacks exploit multiple weaknesses in humans and systems.
The general human weaknesses
First, there are situational weaknesses like work stress or personal issues. Second, certain human physiology and psychological traits make people more susceptible to social engineers:
- selective visual attention with a focus, margin, and fringe
- cognitive biases (e.g., normalcy bias)
- fear of mistake
- overconfidence and vanity
- greed
- curiosity
- gullibility
- lack of responsibility.
The business weaknesses
Some institutional problems make employees more susceptible to social engineering attacks. For example:
- High levels of stress
- Poor planning
- Work overload
- Toxic corporate culture
- Talent gap
For example, a fake email with a credential request from a manager that is excessively judgemental can cause stress in a target. As a result, they might omit the red flags of a social engineering attack. Unfortunately, many businesses turn a blind eye to these issues.
Lack of security awareness training
Security awareness training can significantly increase the ability of employees to spot social engineering attacks. Companies should never underestimate its impact.
Learn more about Cybersecurity Awareness.
IT system weaknesses
Companies that rely solely on human vigilance are likely to fall victim to social engineering attacks. Human error is inevitable in the long run. That’s why your business needs data protection tools that can play the role of the last layer of defense.
Techniques used in social engineering attacks
To exploit the weaknesses of humans, social engineers put extra pressure on the targets by applying the following techniques:
- Urgency (for example, in spear phishing or CEO fraud, the criminal might say that some information must be provided ASAP).
- Scare tactics (for example, the target is forced to believe that their account has been hacked, and they need to do certain actions like clicking the button in the phishing email to reclaim it).
- Authority and conformity (for example, cybercriminals might impersonate governments or law enforcement organizations to create trust and readiness to comply).
- Social connections (it’s not necessary to be friends with a target, sometimes, a brief introduction or referring to a mutual ‘acquaintance’ is enough to establish trust).
- FOMO or other types of scarcity.
More than one technique can be used. For example, spear phishing attacks often use authority and urgency.
Social engineering attack example
John is an accountant at ABC company producing packaging. One day he receives an email from his boss requesting to transfer a large payment urgently. He’s been very stressed at home because his daughter was sick.
Additionally, John had a falling out with his boss. These stressing factors make him inattentive, and he doesn’t notice that the boss’s name in the email address is misspelled.
What are the different types of social engineering attacks?
There are many types of social engineering attacks. Some complex crime schemes involve using multiple types at the same time.
Phishing
Phishing attacks are one of the most popular types of social engineering. It uses electronic mail technology to establish contact with a target.
Phishing emails mimic regular messages from a credible sender. Social engineers impersonate banks, SaaS collab tools (like Microsoft 365 or Google Workspace), popular platforms (like Facebook), or even people. The messages have minimal personalization, like the name of a recipient. In some cases, they can even use the standard ‘Dear Sir/Madam.’
Usually, phishing emails request the check of sensitive information, for example, a CVV code of a bank card or credentials.
Once the target has shared the sensitive information, criminals use it to obtain access to money or the IT system and proceed with the crime.
Spear phishing
Spear phishing attacks are similar, only the level of personalization is much higher. That’s why the OSINT stage of these attacks takes much more time.
Usually, spear phishing is carried out against high-profile companies or organizations. The emails might mimic coworkers, partners, or clients.
Whaling CEO fraud
Whaling and CEO fraud are a subtype of spear phishing emails. Cybercriminals impersonate the C-level or the CEO of a company demanding employees to provide some valuable information or complete transfers. This type of attack might even include the Deep Fake.
SMiShing and Vishing
SMSiShing Vishing is similar to phishing attacks. Only the message is sent via text (SMS) or voice mail (hence the V in the name).
Tailgating
A technique used to get into the otherwise secured company office. The criminals follow the authorized personnel to the office. Often, they would start a conversation with a target during lunch or smoking outside the building. They can pretend to forget their card in the office or be an intern.
Baiting
Once in the office, a cybercriminal can leave a piece of hardware (usually a USB flash) with installed malware in a visible place. The expectation is that an employee takes the bait and connects it to their computer, infecting it.
Cybercriminals can even write something enticing on the hardware (e.g., next year’s promotion candidates) to make it harder to resist the temptation.
Quid pro quo
For many people, it is hard to say no to a person who is prosocial to them. For example, a cybercriminal helps an employee in a cafe and then asks to deliver something to the office for them.
A criminal can make a call or send an email with an offer to help (e.g., arrange an interview with a newspaper for PR purposes). Then they would ask questions that can seem legitimate and secure. Meanwhile, the criminal will use the answers for the attack.
Pretexting
This is a complex social engineering scheme in which the criminal investigates the victim and the target and then creates a pretext to get in contact with the target.
Scareware or Rogue
This attack includes fake malware to make the target believe they’ve been infected and pay for tools that can destroy this software.
Ransomware attack
A ransomware attack is a malware attack that often uses phishing emails to infect IT systems. It decrypts the files on a PC or in cloud offices like Google Workspace or Microsoft 365. Unlike scareware, the infection is real, and decryption is only possible with a special key.
Learn more about Cloud Ransomware.
Diversion Theft
Tricking the delivery service into dropping the goods at the wrong address, where the criminals will be able to get them.
Social Media
It is spear phishing carried out exclusively via social networking websites. Often it uses a honeytrap technique when a target sees an avatar photo of a person who meets current beauty standards.
How to Protect Your Organization from Social Engineering Attacks?
This section reviews several ways to protect your organization from social engineering attacks. Using just one of them often proves to be insufficient. That’s why we recommend using them as a system of tools.
Red flags of social engineering
Every person should know and remember the red flags of social engineering.
Red flags in personal communication:
- the rapid decrease in the distance (a person you just met behaves as if you’re good acquaintances), attempts to penetrate your boundaries
- increased charm
- emotional manipulation (fear, urgency, guilt)
- an internal feeling of confusion
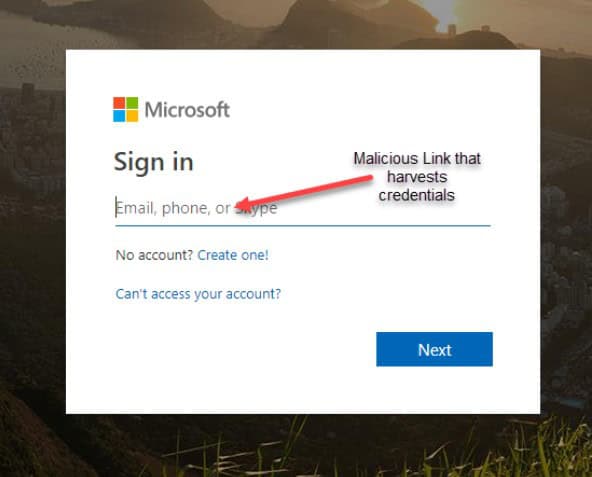
Red flags of phishing emails:
- the name of the sender in the email is miswritten, especially if it is a long name (e.g., anastatsia@spin.ai instead of Anastasia)
- the domain is miswritten (e.g., john@spiin.ai)
- the unusual top-level domain (e.g., john@spin.io instead of .ai)
- an unusual style of email if you know the sender (e.g., your colleague always uses cheers at the end of the letter)
- unusual time of an email
- emotional manipulation (fear, urgency, greed)
- request to provide sensitive information
- call to click on a link
- unusual URL of the link (too long, misspelling at any level of a domain, e.g., gooogle.com)
- Grammatical mistakes*
* It was a significant sign in the past. However, with the popularisation of spellcheckers and the ability of criminals to learn from their mistakes, fewer phishing emails have this red flag.
Security awareness training
Security awareness training is essential for a company’s cybersecurity. Remember the following principles that will guarantee its efficiency:
- it should be part of your onboarding process
- it should be regular and permanent (e.g., every six months)
- it should be available for different types of learning (audio, video, text)
- it should encompass penetration tests (e.g., fake attacks).
Data Control tech stack
The data control tech stack helps your IT team monitor your IT environment for possible unauthorized data access and sharing of sensitive information. Solutions like SpinOne SSPM provide a single pane of glass for all these functions:
- AI-based detection of abnormal logins
If your employee falls victim to social engineering and gives up their credentials, your IT team can spot this if they have a tool that detects abnormal logins.
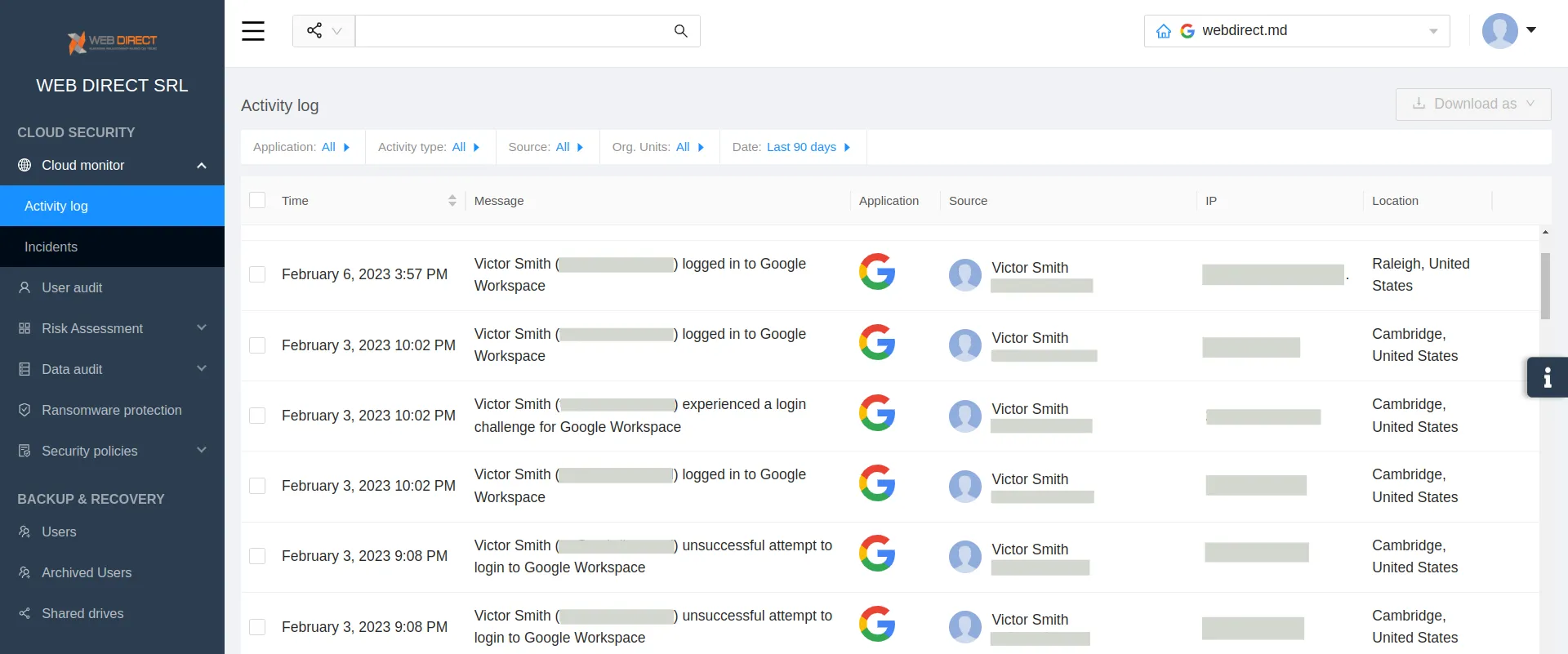
For example, your company operates in the US, and the login has been done in Australia. Or, for example, your employees work within one or two time zones. And you spotted the login in unusual hours (3 AM your time).
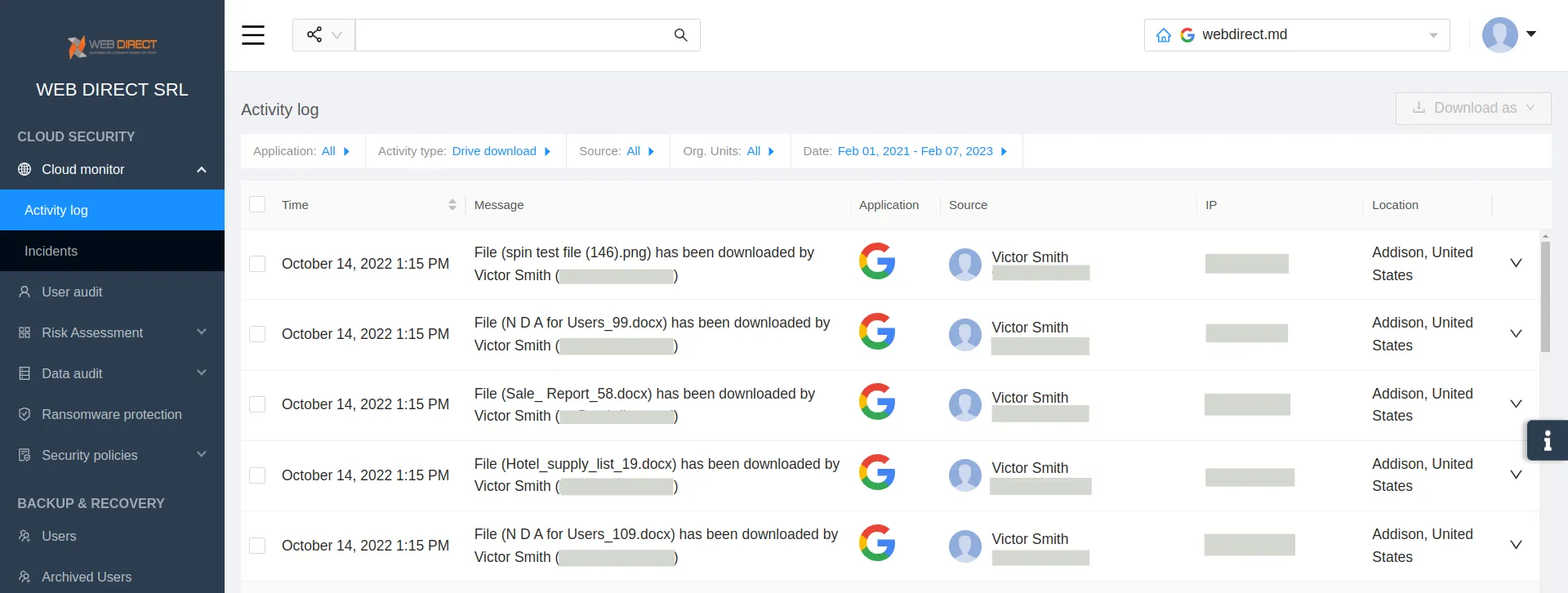
- AI-based monitoring of abnormal data behavior
Another possible sign that your system has been hacked is abnormal data behavior, e.g., the download of a large volume of data at once.
- Data sharing control
A subtle way to get access to the data without being spotted is quickly changing its sharing settings. For example, a cybercriminal finds sensitive information and shares it with a third party.
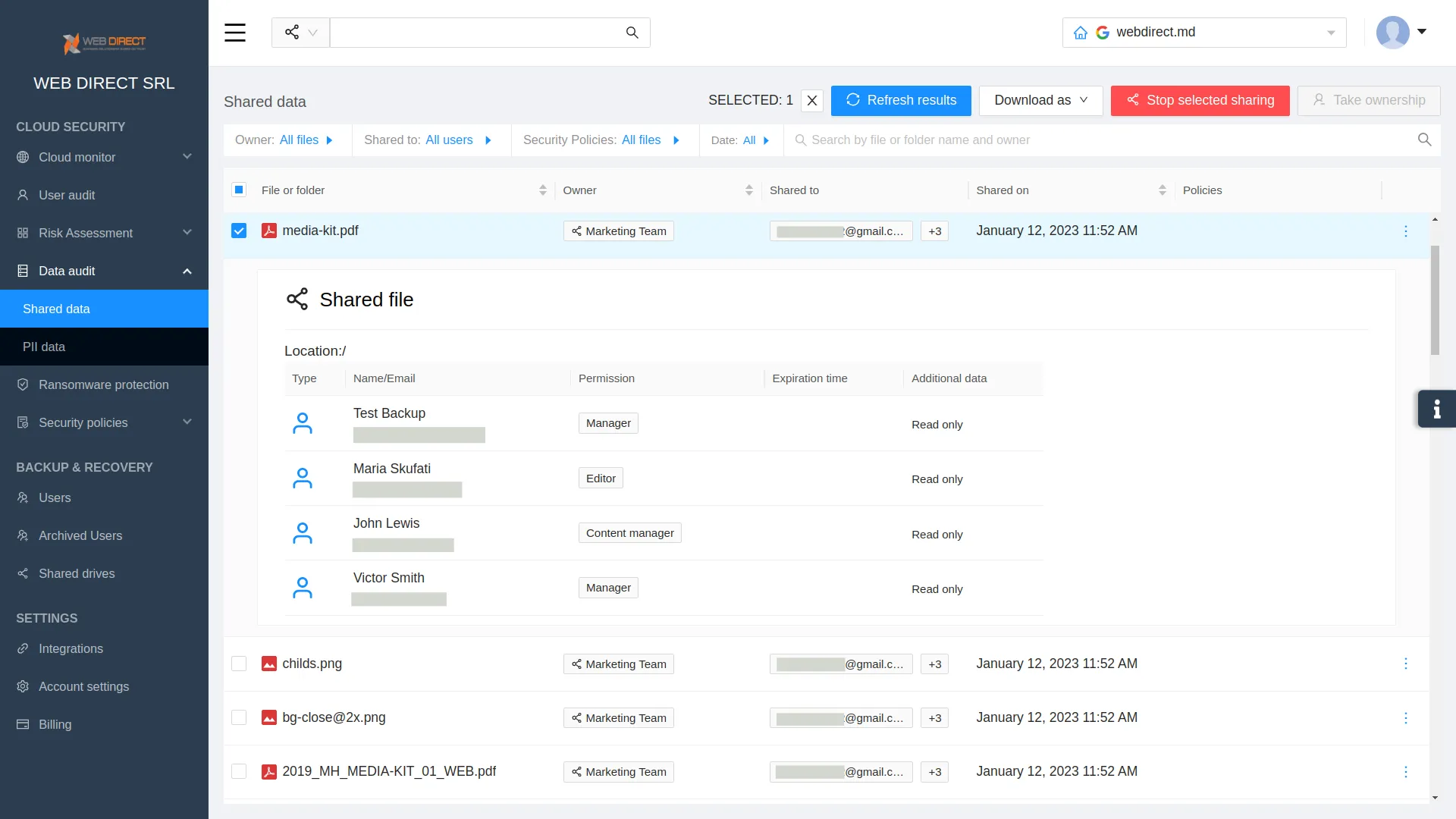
To fix it, you need a tool able to detect the unwanted sharing settings and enable you to change them to the preferable ones.
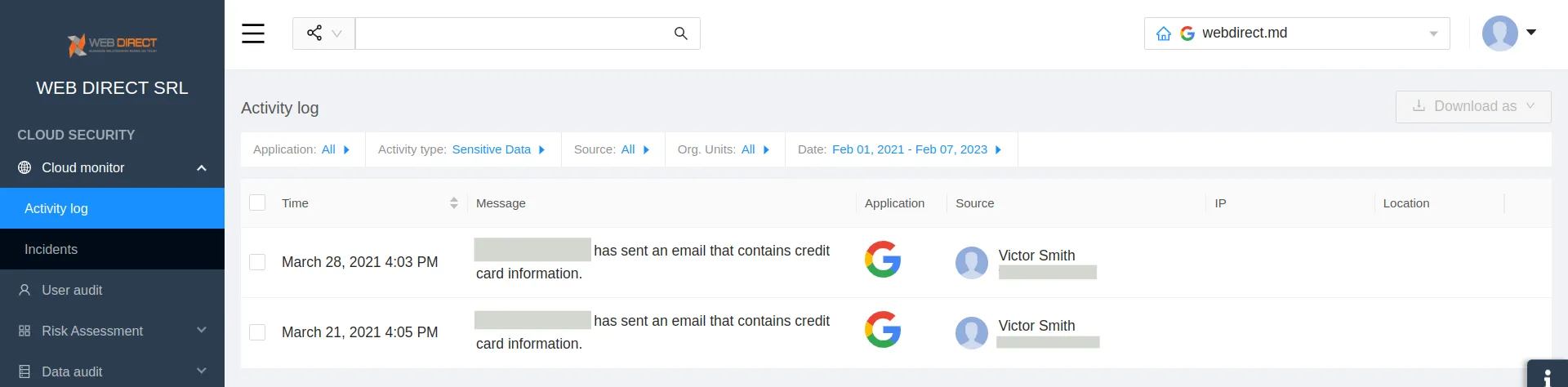
- Detecting emails with PII
Often the targets of social engineering will send PII upon the request of cyber criminals.
Ransomware Protection
Some ransomware protection tools have proven to be efficient in battling not only ransomware but also its most unwanted outcome – downtime. However, you need to be careful when choosing this type of solution.
Most ransomware protection tools would wait till the end of a ransomware attack and then restore data from the backup. When it comes to cloud ransomware and large corporations, the recovery from backup can take weeks and even months.
Cloud collab environments like Google Workspace and Microsoft 365 have API limitations that will make the recovery process exceptionally long.
That’s why you need tools that detect ransomware attacks early on. immediately terminate it and start the recovery process.
Solutions like SpinOne can reduce downtime by up to 99%: from a month to several hours.
Protect your data from social engineering with SpinOne
SpinOne is a SaaS Security Posture Management Platform that can help organizations protect their data stored in cloud environments of Google Workspace and Microsoft 365.
SpinOne is an AI-based application able to detect ransomware and unauthorized access to your cloud data. It can become the last layer of defense for your company in case of a phishing attack.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

