What is SaaS Security?
Rapid cloud adoption and extensive use of SaaS applications enabled companies to boost their performance. However, this has blurred the security perimeter, increased the attack surface, and created multiple vulnerabilities for cybercriminals to exploit. In this article, we will discuss SaaS security, its major challenges, and best practices.
What is SaaS Security
With most companies operating in the cloud, it is hard to imagine efficient business operations without SaaS solutions. Project management applications, cloud office suites, customer relationship management, and SEO tools are just a few categories of SaaS applications used by thousands of businesses on a daily basis.
SaaS security is a body of tools and practices that enables your IT team to gain visibility and control over SaaS applications.
Why SaaS Security Matters
On average, a large enterprise uses 976 authorized SaaS apps. Meanwhile, 80% of employees admit to using at least one unauthorized application.
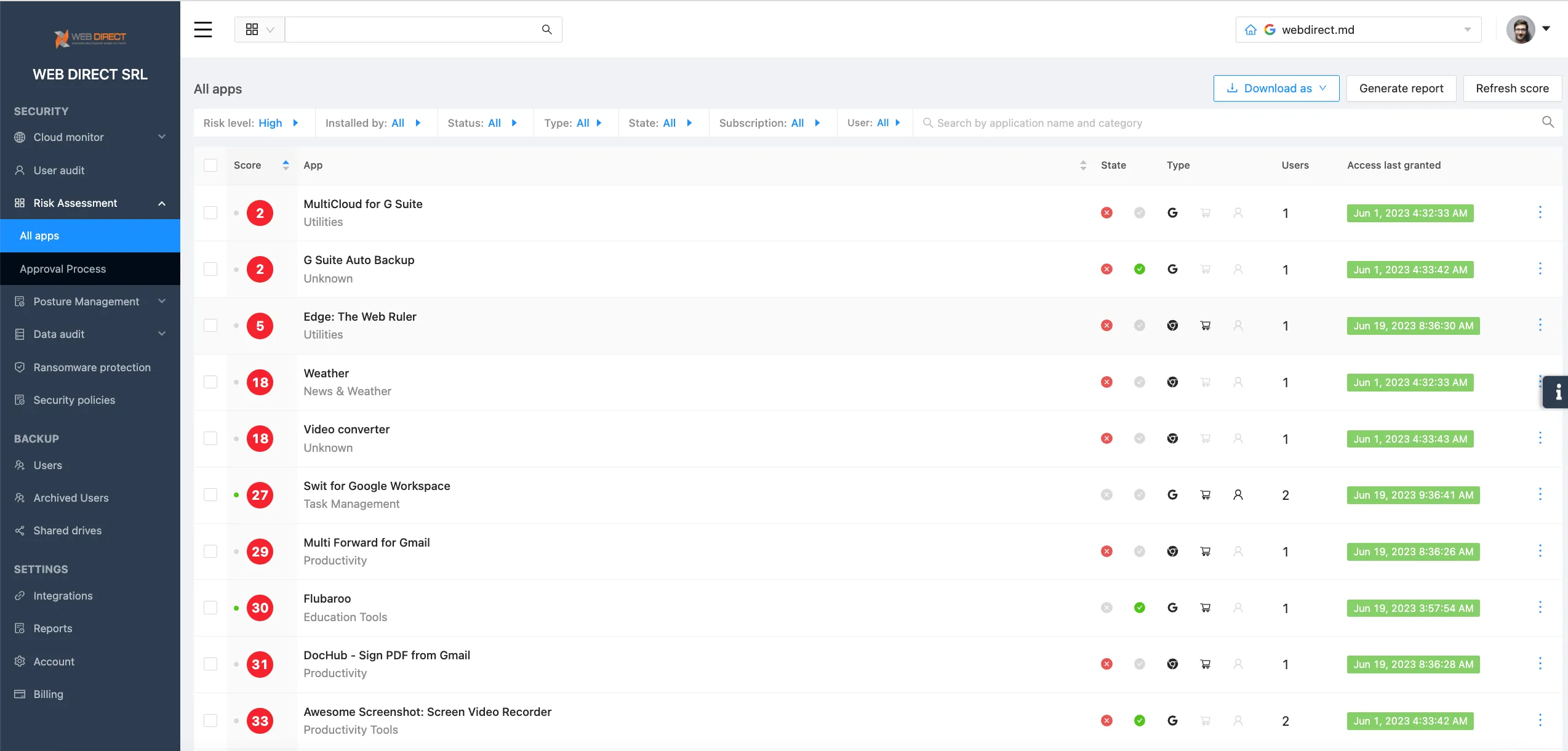
All these tools have some level of access to your cloud data. The access can vary from as little as knowing your user’s email, name, and avatar, to editing your sensitive information. At the same time, OAuth sign-in makes it extremely easy for your employees to enable such access without the approval of your IT security team.
As a result, cloud solutions blur the boundaries between the secure internal environment and the dangerous external network full of malicious actors and cyber threats.
That is why any business that uses cloud SaaS solutions needs security practices and tools that treat the major SaaS security threats and risks.
Challenges of attaining SaaS security
One of the major challenges of SaaS security is securing access to data. In the on-prem security architecture, the IT department created a closed internal network that could only be accessed from the office and secure devices.
SaaS solutions live in the cloud. Anyone from anywhere can access them and the corporate data stored in them, provided they have credentials. Identifying account hijacking is extremely difficult, and some hackers can spend days within cloud environments undetected.
The lack of visibility is another great challenge. As mentioned above, employees tend to ignore corporate security policies. And unless a company has a solution that makes it impossible to bypass these policies, employees use unauthorized SaaS applications.
Furthermore, up to 89% of businesses use a multi-cloud approach making it even more difficult to attain visibility on SaaS applications.
Another common challenge is the cybersecurity talent gap. This line of work is stressful. Meanwhile, the number of real and potential threats is constantly increasing. Many people leave the profession due to constant stress.
Finally, there’s a skill gap in the existing specialists. As cloud environments are rapidly evolving, it is hard to keep up with the new developments.
The SaaS security tools can help address these challenges by closing security gaps, mitigating the workload, and providing necessary visibility into SaaS apps.
5 SaaS Security Threats to Watch Out For
Learn about SaaS Risks that threaten your data security.
Misconfigurations
Configuring complex SaaS environments like Microsoft 365 or Google Workspace is prone to human error. Misconfigurations provide entry points for malicious actors. They also enable your users mistakenly delete or leak sensitive information.
Ransomware
Modern cloud ransomware disguises itself as a legitimate SaaS application. It is hard for a regular employee to identify a malicious application. That’s why ransomware attacks are increasing year over year.
Zero-day attacks
Hackers are constantly looking for vulnerabilities in non-malicious applications to exploit and exfiltrate the data of their users. When they achieve this goal, they conduct a zero-day attack. It is hard to assess the risks of all the applications that a company uses on a regular basis. And it’s almost impossible to detect and stop the attack without specific security tools.
Non-compliance
Many countries have regulations on where and how corporate data must be stored. Using unauthorized SaaS applications can break these regulations and be subject to legal fines or a lawsuit. Additionally, a company can be fined for not preventing a cyber accident.
Identity Access Management
Managing access of users to SaaS applications containing sensitive data can be hard for remote and hybrid work environments. Additionally, credential theft enables hackers to infiltrate cloud environments under the disguise of legitimate users.
Best Practices for SaaS Security
Implement security policies for SaaS
Start with creating company-wide security policies for SaaS applications that match your level of risk. These policies should take into account compliance requirements, threats to business operations, and the risks to data security. They also need to be balanced against the operational needs of your company.
Now, you need to implement security policies across all clouds and SaaS applications. Keep in mind that sending them over to your employees is not enough. You need to implement them within the apps you use. You might see that the existing controls are not enough to complete this task. Search for SaaS security solutions that will provide you with additional tools to impose security policies.
Take Shadow IT under control
You need to detect and map all the Shadow IT applications that your employees using. Major SaaS environments like Microsoft 365 and Google Workspace have functionality that enables you to see which SaaS apps have OAuth access to your data. What they lack, however, is the ability to assess risk and control access. You might need a third-party tool to do it.
Assess Application Risks
Identify the application risk criteria. Take into account legal aspects, risks to business operations, and security risks. Now you are ready to assess each of the SaaS applications that have access to your sensitive data. You can automate this process by using SaaS security tools.
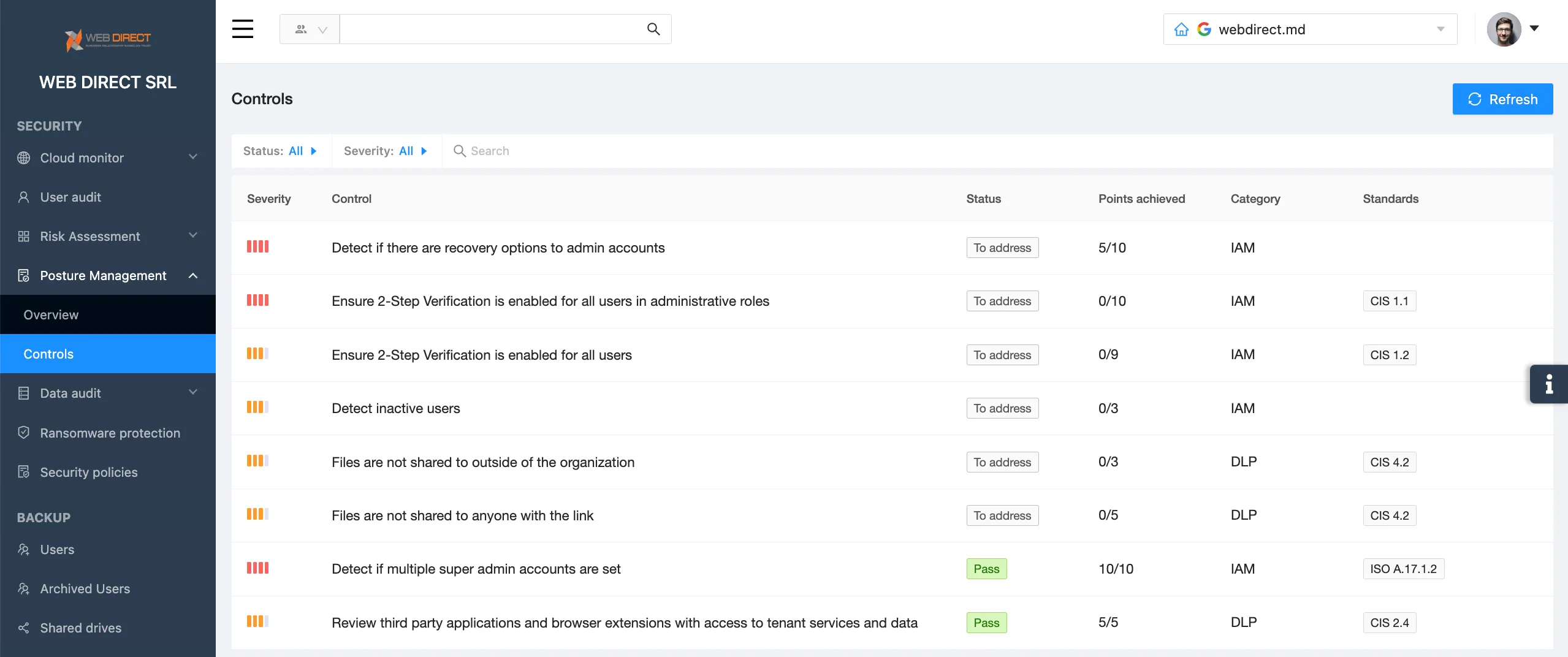
Make misconfigurations visible
Check your cloud environments for misconfigurations on a regular basis. Make sure they match your current security policies. To decrease the volume of work, you can use SSPM tools that will discover misconfigurations within seconds and will help you to configure your SaaS properly.
SaaS Security FAQ
What is SaaS?
SaaS stands for software as a service. It is any type of cloud software catered to clients on a subscription basis.
What are SaaS examples?
Collaboration office suites: Google Workspace and Microsoft 365. CRM: Salesforce, Hubspot. CMS: WordPress, Joomla. SaaS Security: SpinOne.
Is SaaS more secure than on-premise?
It depends. SaaS can provide better security from certain types of cyber attacks, like DDoS. It is much more secure when it comes to natural disasters. However, there are multiple security vulnerabilities that hackers exploit on a regular basis. As a rule of thumb, your IT security team has limited control over the security of many SaaS applications that your employees use on a regular basis.
It depends. SaaS can provide better security from certain types of cyber attacks, like DDoS. It is much more secure when it comes to natural disasters. However, there are multiple security vulnerabilities that hackers exploit on a regular basis. As a rule of thumb, your IT security team has limited control over the security of many SaaS applications that your employees use on a regular basis.
Who Is Responsible For SaaS Security?
Many SaaS solutions have a shared responsibility model. While app developers take care of the security of your data from external threats, it is your responsibility to control your users and configure security correctly.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

