HIPAA Compliance Guide for Google Workspace Administrators
- 1. HIPAA Privacy Rule
- 2. HIPAA Security Rule
- 3. HIPAA Unique Identifiers Rule
- 4. HIPAA Transactions and Code Set Rule
- 5. HIPAA Enforcement Rule
- Which Google Workspace plan can be HIPAA compliant?
- What legal agreements do you need to sign with Google?
- Importance of Signing a Business Associate Agreement
- How is the BAA signed with Google?
- Does technical support from Google help you make your Google Workspace HIPAA compliant?
- Is Google Drive HIPAA compliant
- Is Google Meet HIPAA Compliant
- Is Google Docs HIPAA Compliant?
- Is Google Chat HIPAA Compliant?
- Is Google Voice HIPAA Compliant?
- Is Google Hangouts Compliant?
- Are there Google services that are not permitted for PHI use?
- Google Drive (including Docs, Sheets, Slides, and Forms)
- SaaS Security Spotlight
- Configuration settings for Google Workspace
- Gmail
- Google Workspace Gmail and HIPAA compliance
- TLS and S/MIME Gmail encryption
- S/MIME (Secure/Multipurpose Internet Mail Extensions)
- Google Calendar
- Google Keep
- Google Keep Features
- Google Sites
- Google Cloud Search
- Vault
- Enable two-factor authentication
- With Google Workspace there are several different ways the two-factor verification can be validated
- Monitor Account Activity
- Enable role-based access (RBAC)
- Control third-party apps, systems, or databases
- HIPAA Training within Google Workspace
- 1. Google Workspace Ransomware Protection
- 2. Backups of your data
- 3. App and browser extension risk assessment
As your business moves into the cloud, compliance regulations must be your top priority. An extremely important compliance regulation today is the Health Insurance Portability and Accountability Act (HIPAA). What is HIPAA? If you fall under HIPAA compliance and use Google Workspace, is Google Workspace HIPAA compliant? What about Google Workspace services like Gmail, Calendar, Keep, Hangouts, Vault, and others?
What is the Health Insurance Portability and Accountability Act (HIPAA)?
The main stated purpose of Health Insurance Portability and Accountability (HIPAA) is to protect health care coverage for individuals who lose or change jobs. However, HIPAA Title II, part of the Administrative Simplification, defines how electronically protected health information (PHI) should be protected and secured.
HIPAA includes the following five main directives:
1. HIPAA Privacy Rule
The HIPAA Privacy Rule establishes national standards to protect individuals’ medical records and other personal health information and applies to health plans, healthcare clearinghouses, and healthcare providers that conduct certain healthcare transactions electronically. The Rule requires appropriate safeguards to protect the privacy of personal health information and sets limits and conditions on the uses and disclosures that may be made of such information without patient authorization. The Rule also gives patients rights over their health information, including rights to examine and obtain a copy of their health records and to request corrections.
2. HIPAA Security Rule
The HIPAA Security Rule establishes national standards to protect individuals’ electronic personal health information that is created, received, used, or maintained by a covered entity. The Security Rule requires appropriate administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and security of electronically protected health information.
3. HIPAA Unique Identifiers Rule
HIPAA requires that healthcare providers have standard national numbers that identify them on standard transactions. The National Provider Identifier (NPI) is a unique identification number for covered healthcare providers. Covered healthcare providers and all health plans and healthcare clearinghouses use the NPIs in the administrative transactions adopted under HIPAA. The NPI is a 10-position, intelligence-free numeric identifier (10-digit number). This means that the numbers do not carry other information about healthcare providers, such as the state in which they live or their medical specialty. More information on the National Provider Identifier Standard.
4. HIPAA Transactions and Code Set Rule
The HIPAA transactions and code set standards are rules to standardize the electronic exchange of patient-identifiable, health-related information. They are based on electronic data interchange (EDI) standards, which allow the electronic exchange of information from computer to computer without human involvement. They outline standards for code sets. It is based on the following: International Classification of Diseases, 9th Edition, Current Procedural Terminology, HCFA Common Procedure Coding System, HCFA Common Procedure Coding System (HCPCS), Code on Dental Procedures, and Nomenclature 2nd Edition, and National Drug Codes.
5. HIPAA Enforcement Rule
The HIPAA Enforcement Rule relates to compliance and investigations, as well as penalties for non-compliance.
The official resource for HIPAA standards and information is the hhs.gov site. You will want to reference this resource to fine-tune your understanding and implementation of HIPAA throughout your environment, including in cloud environments like Google Workspace.
Are you migrating your data to the cloud? If you have decided that Google Workspace is the SaaS environment that makes the most sense for your business, is it compliant with HIPAA regulations?

Google’s official statement is that it is compliant with HIPAA and is compatible with this important compliance framework for protected health information (PHI). It is important to note that Google Workspace Security is noted as HIPAA compliant as long as certain requirements are met.
These include the following:
- You use a paid Google Workspace version
- You signed a Business Associate Agreement (BAA) with Google
- Your Google Workspace is configured correctly to support HIPAA compliance
Which Google Workspace plan can be HIPAA compliant?
To ensure HIPAA compliance when using Google Workspace, your organization’s chosen Google Workspace plan must be a paid plan. This means that any of the free Google Workspace offerings are not allowed as options if you must align with HIPAA regulations.
Google has historically scanned content for advertising purposes. While it has stopped doing this circa 2017, there is nothing to prevent Google from doing this again in the future with a free Google Workspace plan.
With the paid version, to be compliant with HIPAA, Google does not scan content for advertising purposes. Are there differences or features in terms of HIPAA compliance between the paid Google Workspace plans? Yes.
What legal agreements do you need to sign with Google?
As mentioned above, you need to sign a Business Associate Agreement (BAA) with Google to be HIPAA compliant. What is the BAA and what role does it play in HIPAA compliance?
In the world of HIPAA, the regulation only applies to covered entities which include health care providers, plans, clearinghouses, and others. However, if these covered entities use the services of another person or business, these are considered to be business associates of the covered entities.
If your organization uses a third party that will interact with PHI, you need to sign a Business Associate Agreement with them. If Google Workspace will be hosting or transmitting information that may contain PHI data, the BAA needs to be signed with Google.
Importance of Signing a Business Associate Agreement
Signing a Business Associate Agreement is crucial for HIPAA compliance. It legally ensures that any third-party vendor – Google Workspace – agrees to use PHI for only explicitly defined purposes and safeguard it according to HIPAA standards. The BAA outlines the responsibilities of both parties regarding the use, disclosure, and protection of PHI, reducing the risk of data breaches and non-compliance penalties. Without a BAA, healthcare organizations and their business associates are exposed to significant legal and financial risks if a breach occurs, as they may be held liable for HIPAA non-compliance. In essence, a BAA is a fundamental component of maintaining HIPAA compliance and protecting patient privacy.
How is the BAA signed with Google?
Google makes the process to review and accept the Business Associate Agreement fairly easily. To sign the HIPAA Business Associate Agreement for Google Workspace, you sign in to your paid Google Workspace account as an administrator and opt into the HIPAA BAA. As outlined in the official Google Workspace Admin help, to do this:
- Sign in to the Google Workspace Admin console
- Click Company Profile
- Click Show More> Legal & Compliance
- In the Security and Privacy Additional Terms next to HIPAA Business Associate Amendment, click Review and Accept.
- Answer the three questions presented and if you are confirmed as a HIPAA-covered entity, click I accept to accept the HIPAA BAA.
Does technical support from Google help you make your Google Workspace HIPAA compliant?
Does Google technical support deal with HIPAA-related issues? No. It is important to understand the technical support provided by Google is not part of the included HIPAA-compliant services they provide. With that being said, you do not need to disclose PHI to Google with technical support cases.
Learn about other frameworks: ISO 27001, SOC 2, and NIST.
How to achieve HIPAA compliance in Google Workspace
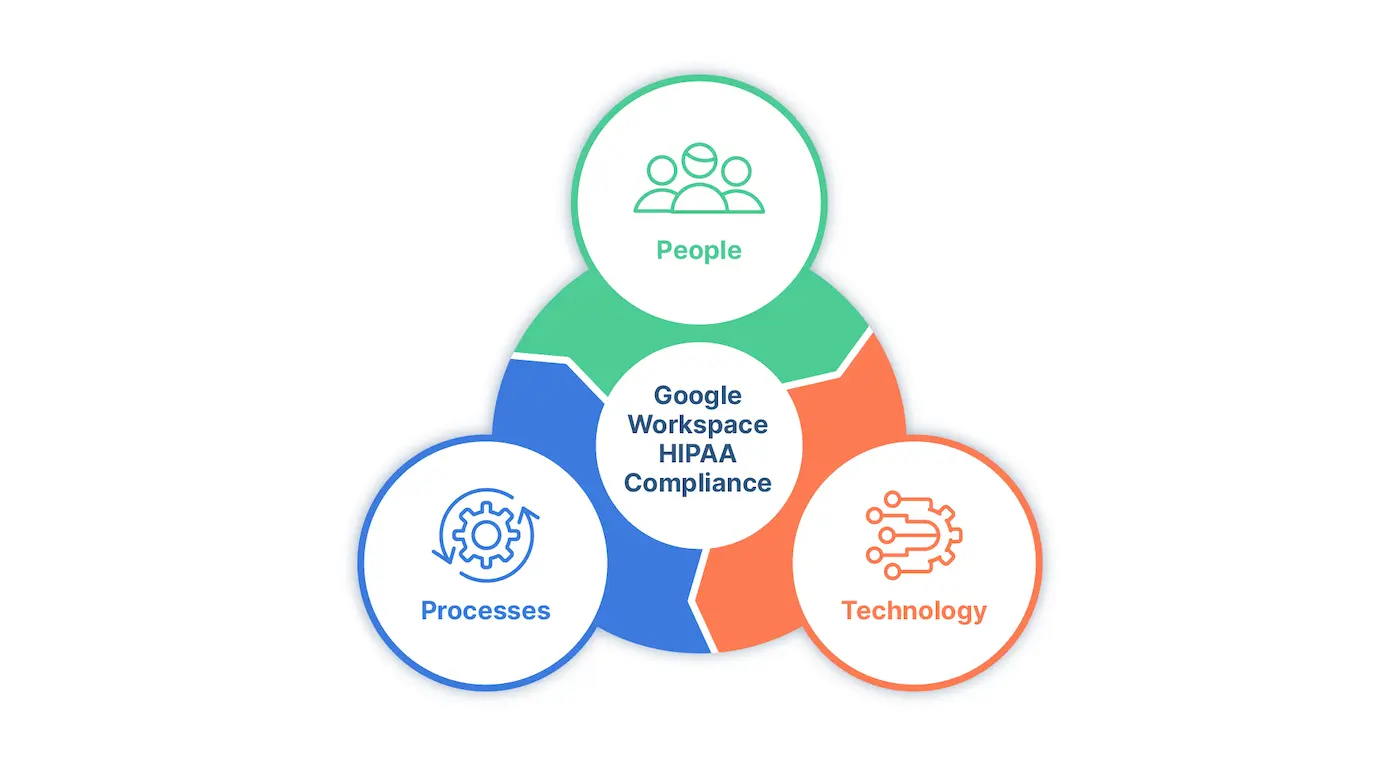
After you have signed the Business Associate Agreement (BAA), you have to configure Google Workspace to comply with HIPAA requirements. When considering how to make Google Workspace HIPAA compliant, it is important to note that Google Workspace services must be used and configured in such a way that it satisfies HIPAA requirements.
An important methodology when it comes to ensuring your Google Workspace environment is HIPAA compliant comes down to the People, Processes, and Technology triangle. It will generally be a mix of all three to ensure that end users are trained to use technology systems including Google Workspace in such a way that aligns with HIPAA requirements, and the processes and technology keeping PHI secure.
What core services are PHI-compliant?
Google lists certain core services within HIPAA Included Functionality that your organization can use in conjunction with PHI. Additionally, there may be services on the list below that require certain features or functionality either to be used or not used for PHI purposes as listed. What core services are PHI compliant? As of today, these services include:
- Gmail,
- Calendar,
- Google Drive (including Docs, Sheets, Forms)
- Gemini for Google Workspace (not including access to Gemini via gemini.google.com or mobile applications),
- Apps Script,
- Google Keep,
- Sites,
- Jamboard,
- Google Chat,
- Google Meet,
- Google Voice (managed users only),
- Google Cloud Search,
- Cloud Identity Management,
- Google Groups,
- Google Tasks,
- Vault (if applicable)
- AppSheet.
Is Google Drive HIPAA compliant
Google Drive can be HIPAA compliant if configured correctly, but compliance is not automatic. Organizations must sign a Business Associate Agreement with Google, which is required by HIPAA when handling PHI. The importance of signing BAA is written above in the text.
Additionally, administrators must implement and enforce proper security measures within Google Drive to support compliance with the Technical Safeguards of the Security Rule. In this regard, Google Drive must be properly configured to include (but are not limited to):
- access controls,
- automatic logoff capabilities,
- audit and event logs,
- integrity controls,
- data backups,
- data encrypt data at rest and in transit.
Google Drive offers features like two-step verification and proper Identity and Access Management (IAM), which help maintain compliance. However, these features may fall short of addressing modern threats to sensitive data and systems. Furthermore, not all Google Workspace plans have these capabilities. To fill this gap and address HIPAA Technical Safeguards sufficiently, businesses can utilize services like SpinOne. It automatically backs up your Google Drive data to ensure it can be recovered, protects it from ransomware, and audits data behavior to ensure security and compliance. Request a free DEMO to experience more capabilities.
The final stage of making Google Drive HIPAA compliant is ensuring ongoing employee training to use the service securely. Some of the common things users should learn about a compliant Google Drive use are not sharing PHI in Docs, Sheets, and Forms, not sharing passwords and other information that can compromise sensitive healthcare data.
Remember, HIPAA compliance depends on a set of tools and the organization’s adherence to HIPAA standards.
Is Google Meet HIPAA Compliant
Google Meet can be HIPAA compliant, but it requires additional steps and configuration beyond just using the basic Google Meet video conferencing service. Here are a few key points about Google Meet and HIPAA compliance:
- Google offers a HIPAA-compliant version of G Suite called G Suite Covered Services that is designed to support HIPAA compliance when properly configured.
- For video conferencing, Google requires using the Google Meet video meet.google.com with G Suite’s HIPAA-compliant support enabled and configured correctly.
- Simply using the free, consumer version of Google Meet is not sufficient for HIPAA compliance because it lacks controls like audit logging, data encryption, and business associate agreements required for PHI.
- Covered entities must sign a HIPAA business associate agreement (BAA) with Google, enable appropriate G Suite services, and follow Google’s implementation guides for HIPAA compliance.
- Google Meet needs to be used with other HIPAA security safeguards like access controls, unique staff identities, and PHI handling policies.
Is Google Docs HIPAA Compliant?
Google Docs can potentially be HIPAA compliant, but it requires using the paid G Suite Business edition with the proper configurations and controls enabled. Here are some key points about using Google Docs in a HIPAA-compliant manner:
- Google offers a HIPAA-compliant version of G Suite called G Suite Covered Services that allows using products like Google Docs for handling PHI (protected health information) when configured correctly.
- Covered entities must sign a HIPAA business associate agreement (BAA) with Google before using G Suite for handling PHI.
- Access controls like unique staff login credentials and auditing must be enabled to restrict PHI access only to authorized personnel.
- All sharing of PHI documents must occur only within the controlled G Suite environment, not using consumer Google accounts.
- PHI data must be encrypted in transit and at rest by enabling appropriate G Suite services.
- Covered entities must still maintain HIPAA policies and train your workforce on proper PHI handling within tools like Google Docs.
Is Google Chat HIPAA Compliant?
Google instructs, “Hangouts Chat provides several options for Admins to control sharing PHI. Hangouts Chat can be enabled or disabled for everyone in the domain or selectively enabled for specific organizations. To enable the service for specific organizations, Admins can select the ‘ON for some organizations’ option which displays the Org Units to search and select. Note that cross-domain and external communication is not supported in Hangouts Chat.”
So yes, Google Chat is considered HIPAA compliant.
Is Google Voice HIPAA Compliant?
Google Voice is a VoIP provider that can transmit phone calls through an internet connection. Google Voice is growing in popularity, with many functions such as voicemail, speech-to-text, and text messaging.
In short, yes: the paid version of Google Voice is considered HIPAA compliant. This can be utilized by healthcare organizations concerning PHI without breaching HIPAA regulations. However, the free personal version is not considered compliant and should not be used by healthcare providers related to PHI.
Is Google Hangouts Compliant?
Google Hangouts Meet is Google’s enterprise video conferencing software. Meet is similar to the free personal version of Hangouts: with extra features such as support for up to 250 participants, 100K livestream viewers, and real-time captions.
In short: Yes, Google Hangouts is HIPAA compliant. However, since Google’s BAA only covers the Google Hangouts chat feature, other features (Video Chat, SMS, and VOIP components) are not HIPAA compliant. For video or audio, healthcare organizations can use Hangouts Meet. Always check Google’s compliance page for the latest updates: https://workspace.google.com/terms/2015/1/hipaa_functionality/
Are there Google services that are not permitted for PHI use?
Yes. These include:
- Google Contacts
It is also important to understand that by default Google Workspace users may have access to other Google services that are not permitted for PHI use. These other Google services that are not listed in Google’s Business Associate Agreement (BAA) are not permitted for use with PHI. These include:
- YouTube
- Blogger
- Google Photos
Google has provided a Google Workspace Admin Help guide discussing how you can see the list of additional Google Workspace services as well as how these additional services can be turned off.
From a management perspective, you can manage different users in your organization by creating what is referred to as organizational units in Google Workspace. You can segregate users who interact with PHI from users who do not and adjust the services they are allowed to use based on their organizational unit.
What about the configuration and tweaks needed for specific Google services? Let’s take a look at those.
Google Drive (including Docs, Sheets, Slides, and Forms)
Google Drive provides cloud storage for your organization when using the Google Workspace SaaS service. With Google Drive, there are configuration and administration items that you want to make sure to give attention to for properly safeguarding PHI. This includes a mix of user training as well as technical items that you want to have in place.
SaaS Security Spotlight
Sign up for quarterly insights on SaaS data security and recovery
Email*
- I have reviewed and accept the Privacy Policy and Terms of Use*
Is Google Drive HIPAA compliant?
Users need to be made aware of the following:
- Do not put PHI into the titles of files, folders, or Team Drives
- Do not attempt to share information in an unsanctioned way outside the Google Drive
- Ensure only appropriate personnel have access to PHI stored on Google Drive
The Google Workspace administrator plays an integral part in making sure the Google Drive configuration is sufficient to protect PHI. There are two main technical configuration aspects of making sure that PHI is protected appropriately. This includes configuring visibility and permissions appropriately.
Configuration settings for Google Workspace
The following list of items details configuration settings the Google Workspace administrator will want to enforce with Google Drive to ensure PHI is safeguarded appropriately:
- Google Workspace admins will want to see the visibility level appropriately set for the Google Workspace account.
- Restrict how employees can share information outside the sanctioned Google Workspace domain
- Set this setting to off – “Prevents users from sharing Google Drive files with people outside your organization through invitations, links, and email attachments. Users outside of your organization will not be able to view newly published sites. Also, prevents users from submitting Google Forms that require them to share documents outside your organization”
- Change the default visibility to Private
- Limit and restrict content sharing even within Team Drives
- Restrict having external members as team members
- Restrict who can download, copy, or print files in the Team Drive
- Make use of the file exposure report in Google Workspace
- Disable the installation of third-party apps
Gmail
Gmail is an extremely important part of your Google Workspace core services and you want to make sure you configure it correctly to align with HIPAA requirements. Any time end users can send information and potentially PHI outside your domain, it deserves extra scrutiny.
Google Workspace Gmail provides the controls needed to help ensure that information, as well as attachments, are only sent to the intended, sanctioned recipients. The last thing you want to happen is for PHI to be sent out intentionally or unintentionally, outside your organization.
What are some of the controls in place that can help to ensure that Gmail messages and attachments containing PHI are not inadvertently sent?
Google Workspace Gmail and HIPAA compliance
Google Workspace Gmail provides powerful email capabilities that can align with HIPAA.
Admins may use the following Google Workspace controls to achieve HIPAA compliance:
- Make sure users only share messages and attachments with the intended recipients
- Create Google DLP (Data Loss Prevention) policies that scan emails for PII/PHI identifiers and act appropriately to prevent transmission or sharing
It’s also important to understand that Google Workspace cloud storage and Gmail work hand-in-hand as employees will most likely be choosing attachments from the Google Drive storage. Having the aforementioned controls in place for Google Drive is necessary to ensure HIPAA compliance. Let’s now look at another important consideration for Gmail message transmission itself – encryption.
TLS and S/MIME Gmail encryption
So, is Gmail HIPAA compliant? For Gmail email to be compliant with HIPAA regulations, it needs to be encrypted. Encrypted communication has long been a way to prevent prying eyes from having visibility to information. Configuring and making use of Google Workspace email encryption with Gmail is an extremely important part of ensuring that protected health information is secured appropriately.
Gmail uses what is known as TLS (Transport Layer Security) encryption. However, it is important to understand that Google can only guarantee the encryption of emails sent within Google’s infrastructure. The encryption of emails sent to other service providers cannot be guaranteed. Without administrative rules to enforce it, if the email server of the sender/recipient does not support TLS encryption, Google will exchange it without TLS encryption.
As you step up into the paid Google Workspace accounts, Google Workspace administrators can create transport rules that disallow any email to be exchanged if TLS isn’t supported. Google does offer a step up from the basic TLS encryption that is provided by default. This is called S/MIME (Secure/Multipurpose Internet Mail Extensions). As mentioned earlier, S/MIME is only available with the paid accounts at the Enterprise plan level. What advantage over TLS does S/MIME bring to the table?
S/MIME (Secure/Multipurpose Internet Mail Extensions)
With S/MIME encryption, the email is encrypted with encryption keys specific to a user so that only that intended user recipient can open the email. This ensures the email stays encrypted and is only readable in transit and at rest with the destination recipient.
S/MIME has some of the same limitations as TLS does such as the requirement for both parties to have email systems that can support the encryption mechanism. In addition, it requires some work to be carried out on the front end by the organizations that you wish to exchange information with. This includes exchanging encryption keys in advance so emails can be encrypted and decrypted properly by both parties.
You can set up compliance and routing rules that require that outgoing messages be signed and encrypted using S/MIME. Using S/MIME routing rules at the Google Workspace organization level ensures that even if end users turn off encryption, the routing rules override this action.
There are third-party solutions that allow for easier implementation and more thorough encryption solutions for your Google Workspace environment. Your organization will need to weigh out the pros and cons of each solution and the costs involved to see which encryption implementation makes sense.
Google Calendar
Sharing calendars between users and teams in Google Workspace is a great way to enhance collaboration and team productivity. However, the Google Workspace Calendar is another service that needs to be configured properly to ensure that PHI is protected accordingly in line with HIPAA rules.
Again, proper end-user sharing processes and technology controls in place can help make sure that PHI is not exposed. Like many of the other core Google Workspace services, the calendars in Google Workspace share all information with everyone in the Google Workspace organization.
End users can set calendar entries to Private for any event related to PHI. Additionally, Google Workspace admins can change the default behavior with visibility and sharing options that can change the default behavior across the entire Google Workspace domain.
Google Keep
Google Keep allows your end-users to take notes and create lists and other items that could contain PHI. With Keep, Google Workspace administrators need to make sure that the Google Drive sharing settings are set to restrict information appropriately. Google Workspace administrators can set the sharing options to either Restrict or Allow sharing outside the organization.
Google Keep Features
With Keep, many of the default sharing settings are in line with HIPAA requirements since Keep by default sets notes to Private regardless of the Drive settings.
Google Sites
The Google Sites service allows easy creation of team sites to share content between team members in Google Workspace. When thinking about PHI, it is important to understand that Google Sites can be visited by members outside of your Google Workspace organization.
According to the main Google Sites page:
Can external visitors access a company site?
Yes. People outside your company can access your site, even without a Google Workspace account. You can also opt to restrict access through sharing settings.
Google Workspace Apps: Google Sites
Google Sites easily allows website creation. Care must be taken to ensure HIPAA compliance.
Since Google’s “bread and butter” is advertising, Google Adsense can be added to Google Sites websites for advertising purposes. This needs to be turned off for sites that contain PHI.
Other considerations to make and change:
- Limit who has access to who can view and edit information on the site
- Do not include text, images, or other content such as calendar information that may contain PHI
- Limit sharing publishing sites externally, perhaps limiting to the internal domain
Google Cloud Search
Google Cloud search offers built-in applications that can be used out-of-the-box. Connectors are made available that can pull in information from other systems such as CRM, Google Workspace documents, and others. Using Google’s patented search technology, information can be found much more efficiently.
Information-intensive industries like healthcare deal with an overwhelming amount of information. So, Google Cloud Search technology can be extremely helpful for healthcare organizations.
Google Cloud Search brings Google search technology to your organization’s data
To ensure that your organization uses Google Cloud search in line with HIPAA requirements, admins have to control how search history is used and who has search history turned on or off. This can be limited for everyone or it can be turned on or off for specific organizational units (must have Google Workspace Enterprise).
Additionally, part of the shared responsibility model that customers have when using Google Workspace concerning HIPAA is making sure third-party connectors or other connections that allow aggregating data for search indexing are properly secured with appropriate permissions.
Vault
Vault is Google’s eDiscovery and compliance solution for Google Workspace. It is used to retain, hold, search, and export data to support retention and eDiscovery activities. Vault is only included in the Google Workspace enterprise plan. It is an add-on for the other Google Workspace plans if your organization chooses to purchase licenses for your users.
Google does not provide a great deal of information regarding specific settings or configurations of Vault related to HIPAA. In fact, in the recent HIPAA guide from Google, Vault is only briefly mentioned. However, it is included in the services that Google defines as HIPAA compliant.
When Vault is used with the other Google core Google Workspace (formerly Workspace) services that are correctly configured for HIPAA, Vault can be used in a sanctioned way to store PHI.
Important Google Workspace settings for HIPAA compliance
Other Google Workspace configuration changes and Google Workspace admin best practices lend themselves to good overall Google Workspace security. The better your overall security posture across your Google Workspace environment, the easier it is to comply with security standards and regulations including HIPAA.
The following other considerations and best practices can help secure your Google Workspace environment and protect PHI:
- Enable Two-factor authentication
- Monitor account activity
- Enable role-based access
- Control third-party apps, systems, or databases
Let’s briefly consider each of these best practices and see how each helps to secure your Google Workspace environment and align your organization with HIPAA regulations.
Enable two-factor authentication
Enabling two-factor authentication is one of the best ways to drastically increase the data security of your Google Workspace/. Passwords have long been a weak point in most environments. End-users tend to choose weak passwords. This can very quickly place business-critical and sensitive data such as PHI at risk.
With two-factor authentication, it requires users to verify their identity with something they know (their password) as well as something they have such as a physical key or a code that is sent to a device such as a cell phone. It is critically important to protect your Google Workspace administrator accounts with two-factor authentication. If an attacker hijacks a Workspace administrator account, they would have all the “keys to your kingdom” and can do anything they want in your environment.
With Google Workspace there are several different ways the two-factor verification can be validated
These include:
- Security keys
- Google Prompt
- Google Authenticator
- Backup codes
- A text message or a phone call
Enabling two-factor authentication is certainly a recommended best practice to improve the overall security of your Google Workspace environment. When it comes to HIPAA compliance, HHS.gov recommends two-factor authentication for protecting electronic PHI.
Monitor Account Activity
Having visibility of the account activity is a great way to protect and monitor potential security threats in your Google Workspace environment. Google Workspace provides the alert center to provide a place to aggregate events and alerts. This includes account activities and alerts.
The Google Workspace alert center can send out email alerts of many different kinds of alerts about events in the environment. However, the alert center must be configured to send out email notifications. To configure alert center email notifications, follow the documentation found here.
Enable role-based access (RBAC)
To follow best practices for permissions and access in Google Workspace, you want to ensure end users have permissions assigned based on their job role. All too often, end-users have more permissions than they need. Workspace provides administrators the ability to easily view a list of user’s roles and privileges in the Google Admin console.
This is not limited to normal end-users. Users who serve as administrators in the Google Workspace can be assigned the administrator permissions they need. Very few will need the Super Admin role in Google Workspace. Google Workspace provides pre-built administrator roles that allow assigning administrator permissions based on the role the administrator will play in your organization.
Predefined Google Workspace admin roles include the following:
- Super Admin
- Groups Admin
- User Management Admin
- Help Desk Admin
- Services Admin
- Mobile Admin
- Google Voice Admin
- Reseller Admin
You can read more about the permissions and capabilities that each role has in the Google Workspace environment here.
Assigning the roles and permissions to users, especially to the users who will serve as administrators in the Google Workspace environment helps ensure that permissions are scoped appropriately. This is in line with HIPAA requirements and is part of the Administrative Safeguards that need to be put in place as part of the HIPAA security rule.
Control third-party apps, systems, or databases
Cloud Software-as-a-Service environments (SaaS) like Workspace allow customers to extend the native functionality by way of third-party apps found in the marketplace. Despite providing extended functionality, third-party apps can expose PHI data as well as bring other security and data leak threats.
Left unchecked, end users can potentially install third-party apps that gain access to PHI. This can easily happen as end users may simply grant permissions that are requested by a third-party app that either could be malicious or “leaky,” exposing sensitive information like patient data.
Monitoring and controlling third-party apps in Workspace is essential to securing your Workspace environment and ensuring the security of PHI.
Workspace provides some native functionality to control which third-party and domain-owned apps can access sensitive Google Workspace services. Access to Google Workspace services are provided via OAuth 2.0. The basic app access control allows organizations to:
- Restrict or leave unrestricted access by third-party apps to Google Workspace
- Whitelist apps so they can access restricted Google Workspace data
- Trust domain-owned apps
For even better control, keep reading to see how third-party application risk can be managed with SpinOne. Request a free DEMO to learn more capabilities.
Find Out if Slack is HIPAA Compliant?
How do you make sure your staff doesn’t accidentally cause a HIPAA breach?
The worst thing that can happen to PHI is a data breach. Breached PHI can mean the worst for a healthcare organization, including fines, tarnished reputation, and potential repercussions that can last for years.
HIPAA violations can lead to fines ranging from $100 to $50,000 per violation (or per record) depending on the perceived negligence that is found within your organization at the time of the HIPAA violation. Your organization must do its due diligence to put the measures in place to ensure that PHI is protected properly.
As mentioned, this is usually a combination of people, processes, and technology to ensure that PHI is protected adequately. How do you put all the information presented thus far together in a way that allows you to make sure that your staff doesn’t accidentally cause a HIPAA breach?
HIPAA is a very complex and delicate law that requires a lot of planning, training, and technology solutions to allow employees to be productive and at the same time ensure that PHI is protected in line with the standards set forth by HIPAA.
To summarize the people, processes, and technology that are needed to make sure your staff doesn’t accidentally cause a HIPAA breach, consider the following:
- End-user training – End-user training for HIPAA is absolutely required. End-users need to be aware of all the aspects of how they need to interact with protected health information properly and the role they play in keeping this data safe.
- Proper configuration of Google Workspace services – Paid versions of Google Workspace can be HIPAA compliant. However, it requires that all services used by your organization be configured correctly and restricted in certain ways to protect health information data.
- Two-step verification – Two-step verification provides greatly enhanced security for end-users, including administrators. It combines something you know (your password) with something you have (a code delivered via device, text, call, app, and other means).
- OAuth 2.0 and third-party apps control – OAuth 2.0 is a mechanism that cloud service providers, including Google, are using to allow end-users to easily integrate and grant applications with Google Workspace data without disclosing their password. However, this can present security concerns as “leaky” or outright malicious apps can be integrated into the Google Workspace environment with just a few clicks on an end-user device.
- Information rights management (IRM) – With IRM, you can disable actions that are risky to PHI such as downloading, printing, and copying from Google Workspace.
- Proper monitoring, auditing, and alerting – Monitoring, auditing, and alerting are key administrative security tasks that help Workspace admins keep on top of potential security events in Workspace. To bring your organization in line with HIPAA privacy and security controls, these are essential activities. Setting Google DLP rules and acquiring data loss prevention software can help you automate these tasks and perform them more efficiently.
- Email security and advanced protection – Email is often the gateway to security breaches or malware attacks. Taking the proper steps to secure Gmail allows your organization to ensure data is protected between the sender/receiver, as well as malware and other types of malicious email such as phishing attacks, are filtered and minimized as much as possible.
- Encryption – Encrypting data makes certain that sensitive data is unreadable outside of sanctioned users. Make sure that information is encrypted both in-flight and at rest will guarantee that PHI data is protected from prying eyes or those outside of the business associate agreement.
- Mobile device management (MDM) – If you have mobile devices that are tied into the Google Workspace environment, using Google Workspace’s MDM solution allows enforcing policies, encrypting data, and remotely wiping or locking stolen or lost devices.
- Backup Google Workspace – Backing up your Google Workspace environment containing protected health information (PHI) is critical to protecting PHI and other business-critical data from data loss. Google Workspace is limited in what it can natively provide in terms of proper backups of your data. Your organization will want to bolster the data protection of Google Workspace with a capable third-party solution that can protect your data across all Google Workspace services.
Outside of the above, your organization will want to have a bullet-proof process that includes the technical processes needed to ensure that all access to PHI and other business-critical data is immediately terminated if an employee leaves the company.
By effective training of your end-users, putting processes in place to help provide the “guard rails” for daily business activities involving PHI, and having the technology solutions in place, will help to greatly minimize the risk that any staff will accidentally cause data breaches.
Let’s take a look at a technology solution that can help bolster your organization’s efforts to ensure that protected health information is secured appropriately and effectively.
HIPAA Training within Google Workspace
Regular employee training on HIPAA compliance tailored specifically for Google Workspace is imperative for organizations using this productivity tool. As healthcare data is sensitive, staff must understand how to handle it securely within this platform. Special attention should be paid to secure document sharing, proper use of Gmail and Google Drive, and maintaining audit trails. Google Workspace offers tools that support compliance, but misuse and misconfiguration can lead to HIPAA non-compliance. Regular HIPAA training on Google Workspace use ensures employees are familiar with the latest security features and best practices to prevent accidental HIPAA violations.
How to make Google Workspace HIPAA compliant with SpinOne
While Google Workspace has many great built-in technology capabilities and features to help secure your Google Workspace environment and align with HIPAA regulations, it can fall short in protecting PHI. Google Workspace native security solutions fall short in the following functionalities:
- Ransomware protection
- Data backups
- Third-party apps risk management
- Data Loss Prevention
- Automated responses
- Security Posture Management
These SpinOne features help address several HIPAA requirements including:
§ 164.308(a)(1) Risk Management: Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level
§ 164.308(a)(1) Information System Activity Review: Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.
§ 164.308(a)(4) Access Authorization: Implement policies and procedures for granting access to electronically protected health information, for example, through access to a workstation, transaction, program, process, or other mechanism.
§ 164.308 (a)(5) Protection from Malicious Software: Procedures for guarding against, detecting, and reporting malicious software.
§ 164.308(a)(6) Response and Reporting: Identify and respond to suspected or known security incidents; mitigate, to the extent practicable, harmful effects of security incidents that are known to the covered entity; and document security incidents and their outcomes
§ 164.308(a)(7) Data Backup Plan: Establish and implement procedures to create and maintain retrievable exact copies of electronic protected health information.
§ 164.308(a)(7) Disaster Recovery Plan: Establish (and implement as needed) procedures to restore any loss of data.
§ 164.312(c)(1) Integrity: Implement policies and procedures to protect electronic protected health information from improper alteration or destruction.
| HIPAA Standard | SpinOne Feature | Description |
| § 164.308(a)(1) Risk Management | SaaS Security Posture Management | SpinOne’s SSPM conducts automated risk assessments of third-party applications and extensions and enables administrators to create risk-based security policies on the third-party applications use. |
| § 164.308(a)(1) Information System Activity Review | Data Leak Prevention & Data Loss Protection | SpinOne Data Audit functionality enables customers to review and analyze various critical security events within the domain such as abnormal logins or sensitive data sent over email. |
| § 164.308(a)(4) Access Authorization | Data Leak Prevention & Data Loss Protection | SpinOne Data Audit functionality enables customers to review files and folders for unauthorized access. |
| § 164.308 (a)(5) Protection from Malicious Software | Ransomware Detection & Response | SpinOne Ransomware Protection automatically identifies and blocks the source of a malicious attack, terminates the encryption process, and runs granular recovery of lost files from the last successfully backed up version. |
| § 164.308(a)(6) Response and Reporting | Ransomware Detection & Response | SpinOne Ransomware Protection automatically identifies and blocks the source of a malicious attack, terminates the encryption process, and runs granular recovery of lost files from the last successfully backed up version. |
| § 164.308(a)(7) Data Backup Plan | Backup and Recovery | SpinOne Backup and Restore solution creates exact copies of data and securely stores those backups in an encrypted format. |
| § 164.312(c)(1) Integrity | Ransomware Detection & Response | SpinOne Ransomware Protection automatically identifies and blocks the source of a malicious attack, terminates the encryption process, and runs granular recovery of lost files from the last successfully backed up version. |
Let’s take a look at how SpinOne allows us to meet HIPAA compliance requirements in Google Workspace much more easily and boost Google Workspace cyber security.
1. Google Workspace Ransomware Protection
Ransomware is one of the biggest threats to your organization’s data, both on-premises and in cloud SaaS environments such as Google Workspace. Modern ransomware can hold your cloud data hostage and new variants are even releasing sensitive data as part of the threat and leverage for a ransom payment.
SpinOne allows effectively countering ransomware in the cloud with a seamless, automated solution that requires no administrator interaction.
SpinOne’s automated ransomware protection provides automatic responses to ransomware infections. This includes:
- SpinOne’s AI-powered solution automatically detects the ransomware infection underway using effective file-behavior analysis
- It automatically blocks the attack source in real-time
- SpinOne automatically identifies the files that have been infected/encrypted with ransomware
- It automatically recovers damaged files from the latest good backup of your Workspace environment taken with Spinbackup
Imagine as a Google Workspace administrator, waking up to a notification that Spin detected a ransomware infection, blocked it, and completely remediated the effects of the ransomware, all without requiring a single interaction by Google Workspace administrators.
2. Backups of your data
Part of the shared responsibility model that Google maintains with Workspace customers is that customers are responsible for protecting their data. There is no official backup solution provided by Google that allows for enterprise-grade backups of your Workspace data, including PHI.
According to HHS.gov, being able to SLAs can include provisions that address such HIPAA concerns as…
- Back-up and data recovery (e.g., as necessary to be able to respond to a ransomware attack or other emergency).
- Automatic backups 1-3x daily
- Encrypted backups both in-flight and at-rest
- Deletion and version control
- Fast search
- Analytics and reports
3. App and browser extension risk assessment
With SpinOne, you get a total apps risk assessment that helps to identify applications that are risky to your data and which applications have read, write, and delete permissions to your sensitive data. This also helps to reduce the risk of shadow IT applications being installed by end-users that bypass organizational policies and other best practices.
SpinOne full visibility and control to over 380,000 Apps and Browser Extensions assessed by our AI-algorithms. This allows your organization to have a completely automated auditing and risk assessment platform for any application that end users attempt to integrate with the Workspace environment containing PHI information.
SpinOne contains;
- Application whitelisting and blacklisting
- Custom security policies
- Visibility to app permissions granted in Workspace
- The business risk level of Workspace apps
Request a free DEMO to learn more.

Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

