Accelerating Ransomware Threat Response for MSPs
- MSPs: what to do if you or your customers are hit with Ransomware
- Recent guidance from CISA-FBI on Ransomware Protection
- Ransomware threat response: best practices before, not after
- 1. Securing the MSP infrastructure
- 2. Securing the customer infrastructure
- 3. Protect cloud Software-as-a-Service (SaaS) environments
Managed Service Providers face multiple cybersecurity threats that can affect their customers as well. Cloud ransomware is one of the biggest threats to MSPs. In the second part of our guide, we’ll discuss an actionable ransomware threat response for managed service providers.
MSPs: what to do if you or your customers are hit with Ransomware
In the first part of our MSPs Ransomware Protection Guide, we looked at why and how MSPs need to protect themselves and their customers. Improving their cybersecurity posture is a critical part of defending their infrastructure core and customer environments.
What if an MSP or an MSP customer has been hit with ransomware? What steps need to be taken to contain the ransomware attack, prevent further tampering with the environment by hackers, and preventing future malicious access? Let’s look at what MSPs can do if they or their customers are hit with ransomware.
Recent guidance from CISA-FBI on Ransomware Protection
With the recent attack on the Kaseya VSA software used by MSPs worldwide, the Cybersecurity and Infrastructure Security Agency (CISA), in conjunction with the FBI, has released guidance for MSPs and their customers affected by the attack. While the guidance, in part, is focused on the Kaseya attack, it provides good general guidance in handling ransomware attacks for MSPs and customers alike.
You can read the specific guidance from the CISA-FBI alert here: CISA-FBI Guidance for MSPs and their Customers Affected by the Kaseya VSA Supply-Chain Ransomware Attack. Let’s look at some of the specific guidance given by the CISA-FBI alert and see what we can glean from the directive for securing MSPs and customers after an attack.
In a ransomware attack affecting MSPs, there are two parts to securing the environments involved. These Ransomware Protection best practices include:
- Securing the MSP infrastructure
- Securing MSP customer infrastructure
For MSPs:
- Download specific detection tools
- Enforce multi-factor authentication across the board
- Enforce minimal network communication
- Use VPNs and segmented networks for access to compromised RMM software
For Customers:
- Validate and protect backups
- Manually patch all systems with the latest security updates
- Enforce multi-factor authentication across the board
- Audit privileged network accounts and enforce least privilege access
Ransomware threat response: best practices before, not after
You may note many of the recommendations may seem strange as steps recommended after an attack. It is true. Most will look at the recommendations from CISA-FBI and recognize these need to be implemented before an attack. While this is true, even after a breach, there is no point in looking at things that should have been in place. MSPs and customers must immediately take action to implement the best practices and remediations as soon as possible. It is better late than never. After a cyber breach event, minutes and seconds count to contain and counteract the actions of cybercriminals.
1. Securing the MSP infrastructure
When it comes to an attack on an MSP, once the MSP is infected with ransomware, such as in a Remote Monitoring and Management (RMM) solution like Kaseya, it provides the pivot point for attackers to infect the entire customer base. In the case of a supply chain attack affecting a management solution like Kaseya, attackers can deliver malicious “updates” or other code once they have a foothold in the RMM solution. Let’s now detail the specific guidance from the CISA-FBI recommendations.
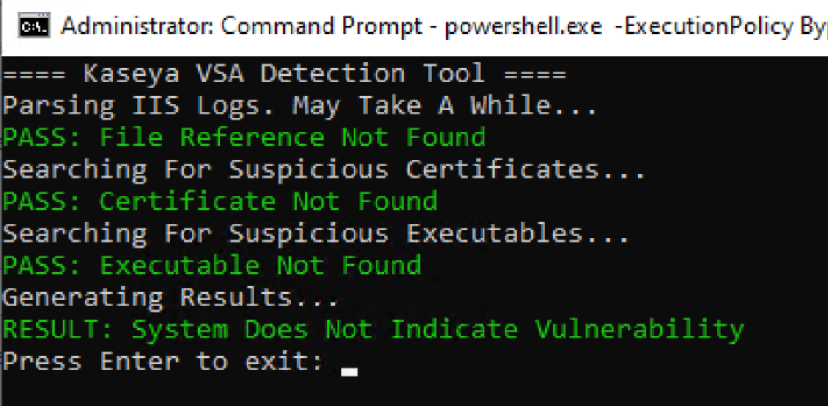
1. Download specific detection tools
In a specific breach event, as was the case in the Kasey VSA ransomware attack, the vendor or other third-party cybersecurity vendor may release specific detection and remediation tools to detect if the environment is compromised. These tools are often needed initially to ensure the imminent threat is removed from the environment.
Kasey released a set of VSA detection tools that customers can download from here. As noted in the official documentation for the tools, Kaseya stated the following:
“In response to the July VSA Security Incident, Kaseya has created self-assessment scripts for both the VSA Server and associated Endpoints. Please note that while these scripts do not guarantee protection, they can aid in the assessment and identification of vulnerable or affected machines based upon the current known indicators of compromise or IoCs. Please note that we strongly recommend that you do NOT give your VSA Server internet access while running these scripts. Ensure your VSA remains OFFLINE and associated services are stopped until you receive an official update from Kaseya.”
Running the Kaseya detection tool
If no specific vendor tool is released, organizations can lean on their cybersecurity vendor of choice for guidance, tools, and recommendations. Most likely, businesses will be doing this anyway in addition to any vendor-specific tools.
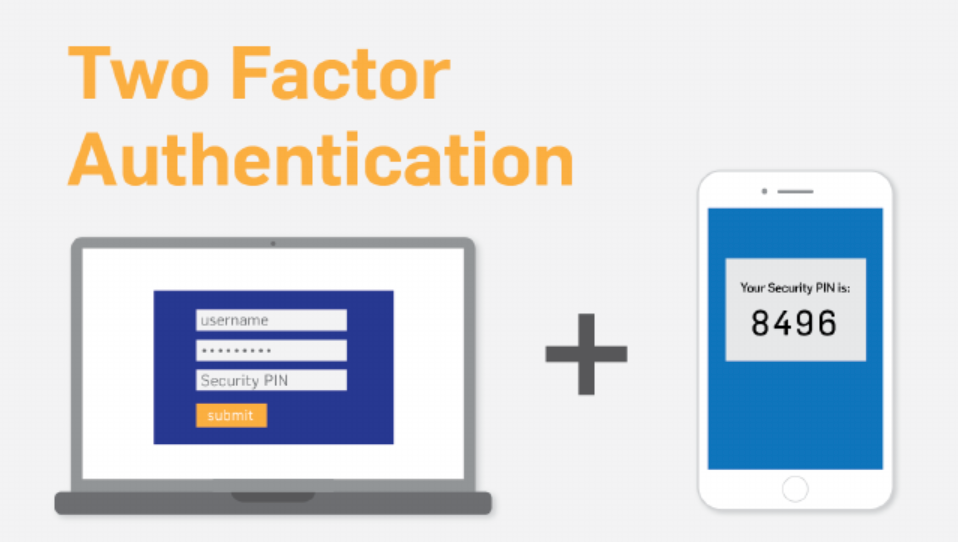
2. Enforce multi-factor authentication across the board
Hopefully, MSPs have already decided to roll out two-factor authentication before any breach attempt. However, if not, two-factor should most definitely be implemented after a breach event as part of the proactive measures organizations should use to regain control of their environment as outlined by CISA-FBI.
All too often, ransomware and data breach events are due to compromised credentials. Even if the environment was not initially infiltrated with compromised credentials, there is a good chance that if attackers have infiltrated the environment, they have most likely harvested credentials for high-level systems.
It can be especially alarming if attackers gain access to an RMM solution like Kaseya, as these often have privileged admin credentials stored for managing subsidiary systems. Therefore, one of the immediate priorities for MSPs who have suffered a breach or ransomware attack is to secure accounts.
By turning on two-factor authentication, the attacker does not have all the information needed to authenticate, even if they know the password. It is because two-factor authentication requires “two” factors of information to log in – the password and a one-time password presented by a hardware device.
MSPs should also coordinate enabling two-factor authentication for customers as soon as possible.
3. Enforce minimal network communication
We have all seen scenes in movies where a hacker gets into a network. The IT admin runs and “pulls the hard-line” for the Internet connection. In reality, something very similar must happen when a cybersecurity breach happens. All network communication must stop in the short term to allow putting in place very restrictive network communication.
This action helps stop any malicious network traffic due to the breach and allows organizations to access the damage and trust only very specific network communications to get business-critical operations back up and running. Initially, after a breach, there may only be allowed communication with a handful of known trusted IP addresses that can be allowed.
4. Use VPNs and segmented networks for access to compromised RMM software
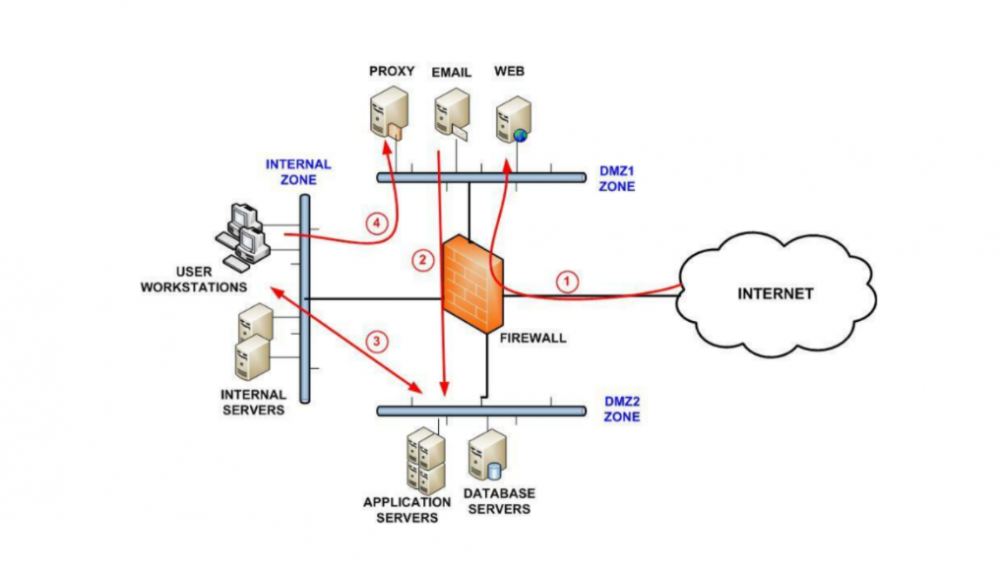
Hackers love infiltrating an environment with a wide-open “flat” network with a single subnet that contains all end-user clients, servers, network devices, RMM solutions, etc. It makes their end goal much easier. After a breach, MSPs that have not correctly designed their network must implement segmented network architecture, isolating or heavily limiting access to affected RMM solutions, critical internal resources, and other business-critical systems.
While isolated, MSPs can scan their RMMs and other solutions to ensure these have not been compromised. Use VPNs when needed to ensure that management traffic is encrypted and secure. Ensure VPNs and other remote access systems are secured with two-factor authentication.
Effectively create zero-trust zones where network traffic is scrutinized, such as below. Micro-segmentation is an even more modern approach, helping to create a zero-trust architecture.
Segmenting networks creates isolated zones for better scrutiny
2. Securing the customer infrastructure
The other side of an attack on an MSP is the customer. As a result, an MSP may have tens or hundreds of customers placed at risk if the MSP is a victim of a cybersecurity breach. The specific guidance from the CISA-FBI for MSP customers is similar to the MSP themselves and provides the necessary steps to ensure customer environments are secure after a breach.
1. Validate and protect backups
Customer environments managed by an MSP attacked with ransomware, or a data breach should immediately validate and ensure good data backups. There is a chance that if the breach is in its early stages, all customer environments may not have been affected. However, immediately taking backups of all critical data can serve as a restore point if the breach progresses through customer environments.
Customers must follow backup best practices to ensure good copies of data are persistent and stored in multiple locations. The 3-2-1 backup best practice methodology allows creating backups of critical data and storing these in such a way they are protected from ransomware and other threats.
“Air-gapping” backups from the production network prevent attackers who have production network access from reaching backups stored in another network. Air-gapped networks have no reachable route from the compromised network environment.
2. Manually patch all systems with the latest security updates
Commonly, hackers will exploit known vulnerabilities that are unpatched in MSP or customer systems. To add to this, MSPs may use RMM systems to patch customer software and solutions. The same system used to patch other systems may be at the heart of the compromise, as in the recent attack on the Kaseya VSA.
Customers should manually patch to the current versions of all business-critical systems to ensure known vulnerabilities and security bugs are patched. In addition, any guidance offered by vendors at the time of an attack due to a known vulnerability is a great place to start. For example, if a zero-day vulnerability is behind the attack, emergency out-of-band patches may need to be applied for remediation.
3. Enforce multi-factor authentication across the board
As is the case with the MSP, multi-factor authentication is an absolute necessity for customers associated with an attack on their MSP. If multi-factor authentication is not already in place, it should be enabled as quickly as possible to add extra protection for user accounts. As mentioned earlier, a cybersecurity breach generally leads to account compromise as part of the fallout.
It should resonate with MSPs and customers alike that if multi-factor authentication is not used now, it should be on the priority list to get enabled. It exponentially bolsters account security. Privileged accounts should be the first to have two-factor authentication enabled, with standard user accounts following as soon as possible.
4. Audit privileged network accounts and enforce least privilege access
Aside from it being a standard best practice, auditing privileged network accounts are essential. Even if privileged accounts are not initially compromised, monitoring their use, access, systems they access, and other key metrics is crucial for ensuring these are not compromised at a later date.
Enforcing least privilege access means that user accounts only have the permissions and rights to business-critical resources that are necessary. Unfortunately, it is all too common for user accounts to have overprovisioned permissions. Hackers love organizations, including MSPs, who use overprovisioned accounts to provide high levels of access. It makes compromising environments effortless.
3. Protect cloud Software-as-a-Service (SaaS) environments
An area not explicitly addressed by the CISA-FBI recommendations is cloud SaaS. Many MSP-managed organizations today have migrated or are in the process of migrating many on-premises services to the cloud. Cloud Software-as-a-Service offerings like Google Workspace and Microsoft 365 have seen tremendous growth. The trend towards cloud migration is showing no signs of slowing down.
Organizations see the advantages of using cloud SaaS platforms for effective communication, collaboration, and file access from anywhere. However, MSPs and customers alike need to protect their cloud SaaS environments from ransomware. It can easily affect business-critical data in the cloud, including cloud email, file storage, and other services. Unfortunately, native ransomware cybersecurity solutions are lacking in the cloud from either Google or Microsoft. While cybersecurity solutions exist as part of the cloud giant’s offerings, they fall short of proactively stopping a ransomware attack.
SpinOne provides AI-based, proactive ransomware protection that does not sit around and wait to respond to a ransomware attack. Instead, it proactively goes after a ransomware attack in your cloud SaaS environment. It uses the following approach:
- SpinOne continually scans the cloud SaaS environment for the signs of a ransomware infection
- If an attack is detected, Spin blocks the source IP of the malicious process attempting to encrypt data
- Any files that have been affected are restored automatically
- Administrators are alerted to the ransomware attack and automated actions
SpinOne allows MSPs and customers to protect their cloud SaaS environments from ransomware in a proactive manner, preventing mass amounts of cloud data from being encrypted. It decreases the downtime due to the attack by over 90%.
Learn more about SpinOne’s Ransomware Protection module and the other features that allow MSPs and customers to protect and secure their cloud data here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...