MSPs Ransomware Protection Guide: Keeping Clients Protected
- Why and How MSPs Must Enhance their cybersecurity posture to Defend customers from Ransomware Attacks
- Ransomware – a modern plague. Are you keeping your clients protected?
- MSPs are a natural target of attackers
- Ransomware Protection Guide: how MSPs can enhance their cybersecurity posture
- SpinOne – Helping MSPs with cybersecurity posture
- Wrapping Up
Managed Service Providers frequently become targets of ransomware. The consequences of this event can be devastating for both MSPs and their clients. Learn how to defend against this type of cyberattack in our Ransomware Protection Guide for MSPs.
Why and How MSPs Must Enhance their cybersecurity posture to Defend customers from Ransomware Attacks
Small to medium-sized businesses that may not have in-house expertise often turn to the technical services and solutions provided by a Managed Service Provider (MSP). SMBs can leverage MSPs for the technical execution, management, and hosting of technology solutions used by the organization. MSPs can provide a wealth of services and benefits to businesses today who want to shift the burden of managing their technology infrastructure to an MSP.
However, SMBs and MSPs alike do well to note the wide range of cybersecurity threats that currently risk business-critical data. MSPs can be a treasure-trove target for attackers looking for the most extensive “blast radius” possible with ransomware and other types of attacks. This post will explain why and how MSPs must enhance their cybersecurity posture to defend customers from ransomware attacks.
Why businesses turn to Managed Service Providers (MSPs)
Especially in the SMB and mid-sized business sector, many organizations may simply not have the IT staff or expertise needed to care for all the company’s technology needs. With this being the case, many businesses turn to a Managed Service Provider (MSP) to take care of their technology infrastructure, service, support, cloud, and other technical needs.
Managed Service Providers today offer a wide range of value-added services for customers. MSPs allow many SMB companies to operate with a larger enterprise organization’s technical efficiency and prowess without internal on-staff employees.
When an outside company is involved in taking care of the business-critical systems of an organization, there are certainly cybersecurity concerns that can arise, especially with the current plague of ransomware that is rampant.
Ransomware – a modern plague. Are you keeping your clients protected?
Arguably, no word strikes fear in most organizations today, including MSPs, like ransomware. As such, ransomware has maneuvered into the top spot of cybersecurity threats that risk business-critical data. It is because ransomware is quick, easy, and attackers find it highly effective in achieving the end goal of getting a ransom payout. Ransomware generally catches businesses off guard, locking up business-critical data so that critical systems, business processes, and core operations often cannot function in the meantime. Is it a pervasive problem?
Ransomware is growing and attacking MSPs
Ransomware is becoming the new pandemic for digital data. It is increasing in terms of the number of attacks and sophistication with which it strikes. According to Cybersecurity Ventures, ransomware will attack a business every 11 seconds by the end of 2021. In addition, the costs of ransomware attacks are projected to be $20 billion. These figures represent a 57X increase since 2015. Furthermore, it shows just how effective and successful ransomware attacks have become.
More figures to consider:
- There was an 800% surge in ransomware in 2020
- In 2020, 73% of all Ransomware attacks were successful, with a lack of effective defensive measures
- In 2020, businesses were the primary target of ransomware attacks, with costs in the tens of millions of dollars
Specifically in regards to Managed Service Providers (MSPs)
- An attack perpetrated by REvil, aka Sodinokibi ransomware gang, against Managed Service Providers (MSPs) and their clients was discovered on July 2
- Some of the victims have reportedly been compromised through a popular MSP software which led to encryption of their customers. The total number of encrypted businesses could run into thousands.
- A California-based MSP, Synoptek, suffered a Sodinokibi ransomware attack – It disrupted operations for many of its clients. The company reportedly paid a ransom demand in a bid to restore operations as quickly as possible.
- An attack compromising the Kaseya VSA platform used by MSPs was recently hit with a supply chain attack timed to hit over the July 4 holiday. The culprit in the attack was REvil, the ransomware-as-a-service group thought to be behind the JBS attack.
- Accenture on Wednesday, August 11, 2021, was hit by a LockBit ransomware attack, and despite saying it had contained the breach before the deadline for its confidential information was released, saw the limited release of some of its confidential information.
- Goldstein said the Accenture breach is yet another call to action for every company to review their security technology posture and procedures. “If a $45 billion company like Accenture is vulnerable then everyone is vulnerable,” he said.
The ransomware threat is increasing: danger of supply chain attacks
A supply chain attack has gained traction and notoriety among the community, especially following the attack on SolarWinds. Sophisticated and experienced hackers are increasingly using supply chain attacks. In a supply chain attack, hackers place malicious code or components into an otherwise trusted piece of software or hardware.
Trusted vendors often do not undergo the scrutiny by SecOps or IT admins, as do smaller pieces of software and hardware. Since the product or solution comes from a respected and well-known vendor, it is assumed the risk or threat is low. However, this type of thinking plays into the hands of attackers. When attackers can compromise a well-known vendor at the source, the software or hardware is distributed from the trusted vendor with malicious code or embedded hardware.
The supply chain attack lends itself to Managed Service Providers (MSPs) since these often use third-party MSP management tools or other solutions to manage customer infrastructure and accounts. As a result, an MSP compromised either by a supply chain attack or a ground-zero ransomware attack can easily be responsible for compromising all the customer environments they can access.
MSPs are a natural target of attackers
It leads to MSPs being a natural target of attackers. They know that a single well-placed attack on an MSP can capture the MSP’s data and all companies whose infrastructure assets they manage. Attackers also know MSPs will be responsible for restoring multiple sets of data for numerous companies. Given this fact, MSPs will likely feel pressured to pay the ransom demanded to regain access to their data and their customer’s data.
In the case of software, a well-placed compromise can quickly reach hundreds if not thousands of customers in a short time via updates or other synchronization processes with the vendor. This scenario played out seamlessly for Russian hackers involved in the massive supply chain breach of SolarWinds. SolarWinds is a common name in the space of network monitoring and other network management tools. One of their tools, known as the Orion IT Management tool, was implanted with malicious code, allowing it to reach an estimated 18,000 networks of customers who use the Orion product worldwide.
Early in July 2021, threat actors executed ransomware attacks leveraging a vulnerability in the software of Kaseya VSA on-premises products against MSPs and their downstream customer base. Kaseya is an enterprise solutions developer that supplies management software to MSPs and enterprise clients. It is a believed an authentication bypass vulnerability in the Kaseya VSA web interface allowed attackers to carry out the breach. Ransomware was pushed to clients, including MSP customers, as a fake management agent update. However, the management agent update was instead REvil ransomware.
The recent attacks on SolarWinds and Kaseya underscore how important it is for MSPs to enhance their cybersecurity posture to defend customers from ransomware attacks. So what can MSPs do to protect themselves and their customers effectively?
Ransomware Protection Guide: how MSPs can enhance their cybersecurity posture
There are several recommendations for Managed Service Providers to help them bolster their cybersecurity posture and, by extension, protect their customers. What are these? Let’s detail the following:
- Use least privilege access to customer environments
- Patch systems regularly
- Use two-factor authentication across all systems
- Implement ransomware protection for cloud SaaS environments
- Ensure proper backups
1. Use least privilege access to customer environments
The damage inflicted by ransomware is amplified when permissions and network access to resources are beyond what is needed. As a result, organizations, including MSPs and the customers they manage, must adopt a least-privilege approach to managing their networks, data, and infrastructure.
The least-privilege model means the access and permissions granted are no more than what is absolutely required. Access to customer resources by MSP resources should not extend beyond what is needed. Control and access to privileged accounts held by the MSP should be limited and audited regularly.
2. Patch systems regularly
Undoubtedly, organizations that fail to patch regularly open themselves to vulnerabilities that attackers can exploit to infiltrate infrastructure and launch ransomware attacks. However, statistics show that organizations are generally slow to patch critical systems. Patching, while necessary to bolster cybersecurity, is tedious and requires regular maintenance intervals.
According to the Bitdefender 2020 – Business Threat Landscape Report:
“Unpatched vulnerabilities are one of the main reasons for why organizations are breached, according to 60 percent18 of breach victims in 2019, and the lack of visibility into these unpatched vulnerabilities usually leads to breaches. According to the same survey, 62 percent of organizations did not even know they were vulnerable until after the breach, and 52 percent have a manual patching procedure instead of an automated one.”
MSPs must ensure that tools, solutions, and third-party software are continually updated with the latest recommended security patches. Any failure to do this places MSP customers at grave risk for compromise due to vulnerabilities in systems managing customer environments.
If MSPs are administering patch management for customers, they must ensure customer environments are up-to-date as well as a customer ransomware infection can also affect the MSP environment under the right circumstances.
3. Use two-factor authentication across all systems
One of the easy ways inside MSP and customer environments is a breached account. Attackers can breach accounts in many different ways. These breaches can include successful phishing attempts, malicious software installed by an end-user, breached password lists, brute force attacks, password spraying, and many others.
The traditional password is no longer in itself an effective means of security due to the threats mentioned above. Due to this, two-factor authentication is becoming the recommended approach to securing user accounts. It is a form of multi-factor authentication that combines something you know (your password) with something you possess (a hardware device that can generate a one-time password or token).
An attacker who compromises a user account password with two-factor authentication enabled does not have everything they need to authenticate and masquerade as the user. They only have part of the information and authentication “factors” required for successful authentication and authorization.
Due to the likelihood of password compromise, even with complex passwords, MSPs should enable two-factor authentication across the board for internal employees and guide customers through the process of getting two-factor authentication enabled. By doing this, they significantly bolster the cybersecurity posture of their entire landscape of infrastructure, including their customers.
4. Implement ransomware protection for cloud SaaS environments
Many organizations are jumping to the cloud for housing business-critical assets and basic communication and collaboration infrastructure. Cloud SaaS environments like Google Workspace and Microsoft 365 offer extremely powerful services for businesses to use, especially with the tremendous shift to remote work seen over the past year and a half.
One of the value-added services that MSPs offer is managing the migration and long-term management of cloud SaaS environments for customers. Therefore, MSPs need to think about securing customer’s cloud SaaS offerings from ransomware in addition to on-premises infrastructure.
While Google Workspace and Microsoft 365 have native cybersecurity solutions they offer, these fall short when it comes to protecting businesses against ransomware. MSPs need to use third-party solutions to protect customers from ransomware in the cloud effectively.
MSPs who help clients get a handle on ransomware protection in the cloud are at an advantage. They can use this as an opportunity to grow their business with additional value-added services for cloud cybersecurity solutions.
5. Ensure proper backups
A significant component of a good cybersecurity posture in dealing with ransomware is backups. Backups of business-critical data are necessary to allow recovery from a ransomware attack. Following the 3-2-1 backup best practices rule ensures backups are available for recovery, even if multiple copies of your data are encrypted with ransomware.
The 3-2-1 backup best practice rule requires at least (3) copies of critical data are stored on (2) types of media, with at least (1) copy stored offsite. Therefore, MSPs should ensure they have up-to-date backups of all critical data and guide customers in implementing best practice recommendations with backups of their critical data.
Testing backup recovery periodically with on-premises and cloud backups is essential to verify that backups are valid and contain the expected data required. All too often, backups are assumed to be good only to find that the backups are not valid after ransomware has encrypted critical data.
When MSPs choose backup solutions to protect cloud SaaS data for themselves and their customers, they should choose a solution that allows storing the data outside of the cloud environment being protected. This requirement ensures that if there is a cloud outage, both the production and backup data are not affected and inaccessible at the same time.
SpinOne – Helping MSPs with cybersecurity posture
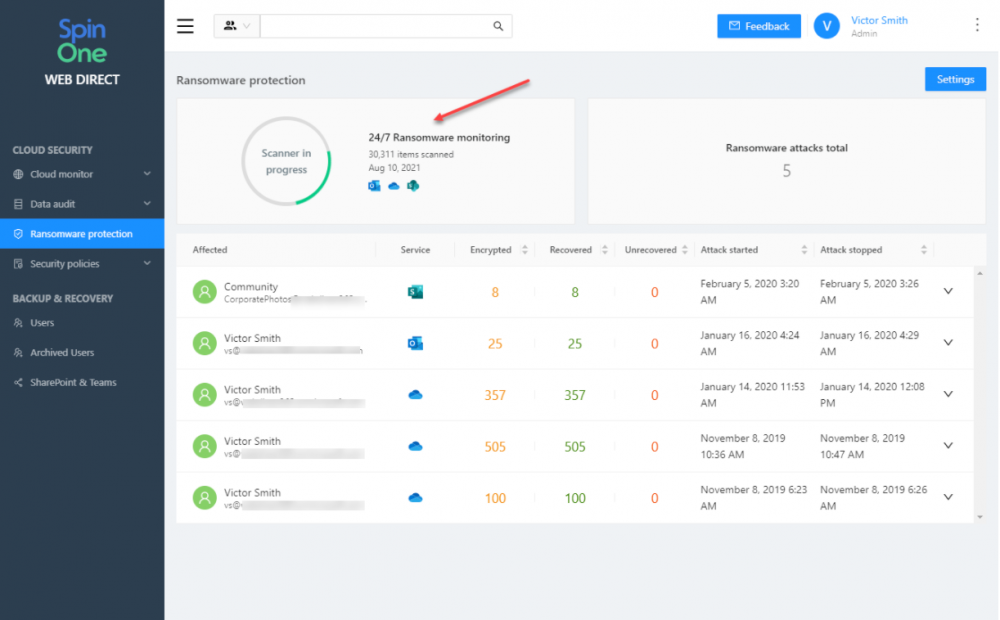
MSPs today are challenged with more cybersecurity risks for themselves and customers than ever before. Ransomware is on the top of the list for threats targeting MSPs and customers. As a result, they need the right technology tools to combat ransomware, both on-premises, and the cloud. SpinOne is an AI-driven cloud SaaS Security Posture Management tool that effectively helps businesses secure their data in cloud SaaS environments. It offers a holistic cybersecurity platform that allows businesses to protect the data in the environment and secure the data proactively.
SpinOne’s Ransomware Protection uses artificial intelligence (AI) and machine learning (ML) to:
- Quickly identify a ransomware infection in progress in the cloud SaaS environment
- Forcibly block access from the malicious process
- Restore any affected files automatically
- Notify and alert IT admins of the attack and operations
SpinOne provides AI-assisted proactive ransomware protection
SpinOne helps MSPs provide value-added cybersecurity services for customer cloud SaaS environments housed in either Google Workspace and Microsoft 365 and also protecting their own cloud SaaS data. In addition to the ransomware protection features, SpinOne:
- Dramatically reduces downtime and recovery costs with high-level of automation for SecOps
- Reduces risk and prevents ransomware by identifying risky OAuth Apps & Browser Extensions with automated Risk Assessment
- Improves compliance and local regulations for Access Management
The modern approach to proactive ransomware protection is superior to the native cybersecurity protection found in either Google Workspace or Microsoft 365. The next-generation features provided by Spin allow MSPs to protect themselves and customers against modern ransomware variants in the cloud.
Wrapping Up
Modern ransomware variants are a tremendous threat to businesses and their data, both on-premises and in the cloud. Hackers target managed Service Providers (MSPs) as they can be the gateway to hundreds, if not thousands of businesses in a successful attack. As a result, MSPs must bolster their cybersecurity posture to deal with the threat of ransomware for their customers effectively.
SpinOne provides a robust solution that can help MSPs not only deal with ransomware effectively but provide value-added services to customers. Protecting against the threat of ransomware is on the top of the cybersecurity priority list across the board. As a result, MSPs must prioritize enhancing their cybersecurity posture with the processes and technologies needed to do this effectively.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...