Cloud Ransomware Disaster Recovery Plan for SMBs
In this guide for SMBs, we explain in detail how to create a cloud ransomware disaster recovery plan. It focuses on the ransomware incidents that occur in cloud environments like Google Workspace and Microsoft Office 365.
Cloud Ransomware and SMBs
Many small and medium businesses aren’t prepared for a ransomware attack and do not have an actionable recovery plan. There are several reasons for it.
First, it is due to the cybersecurity budget limitations and talent gap. The truth is a company doesn’t need a large budget or a big cybersecurity team to prepare a plan for cloud ransomware attack recovery.
Second, many businesses think that Google Workspace and Microsoft Office 365 are safe environments. Unfortunately, they do not understand that cloud ransomware is disguised as a secure app. As a result, in most cases, ransomware gains access to these environments as a result of a user mistake (like in phishing).
Third, it is due to the belief that cybercriminals are only interested in large corporations. This belief is not backed up by the actual data, however. We’ve seen a dramatic increase in ransomware attacks on SMBs in the past years, from 6,300 per day in 2019 to 31,000 in 2021.
Attackers understood that large corporations have better cybersecurity to protect their data. Meanwhile, small and medium businesses are an easier target. Furthermore, many of these companies actually partner with larger organizations and can be used as an entry point to hit bigger targets.
Summing up, we believe a recovery plan is essential and doable for SMBs.
Cloud Ransomware Disaster Recovery Plan for SMBs
There is no one-size-fits-all step-by-step guide on the actions a business should take in case of a cloud ransomware attack. We suggest thinking of your plan as a flexible algorithm that has several scenarios depending on the impact the ransomware has.
Think about the following elements:
- Make a list of essential activities
- Identify the affected and unaffected business operations
- Assign the people in charge of recovery
- Analysis of risks and business impact
- How to stop ransomware
- How to recover the data
- Is backup good for cloud ransomware disaster recovery?
- RTO, RPO, and RTA
- What to do in case of double extortion?
- Should we pay a ransom?
Let’s take a closer look at each of them.
Make a list of essential activities
When ransomware hits, the victim company is in havoc. You need to understand what steps should be done in this case.
- Stopping the attack
- Restoring data
- Negotiating with the criminals
- Managing legal issues
- Informing the employees about the incident and giving further instructions
- Getting business processes back to normal
- Analysis of the actual impact on business
Write this list down. When you form a team for ransomware recovery, you will outline the steps within each of these items with the respective person in charge.
Identify the affected and unaffected business operations
Think about three things:
- Which business operations can easily continue without access to your Google Workspace or Microsoft Office 365? For example, the production team in certain cases doesn’t need access to these tools.
- Which processes can be temporarily carried out without this access? For example, certain people on the marketing team can work without GW for some time.
- Which operations will be completely frozen? For example, a financial team completely depends on the spreadsheets and data in them.
Talk to heads of departments about preserving the operations during a ransomware impact.
Team in charge
When a cyber incident occurs every minute counts. You wouldn’t want to waste it figuring out what should be done and who should be doing it.
Define people who would be responsible for dealing with a ransomware incident in advance. Assign employees in charge of the tasks that you outlined previously. Discuss what they should do in case of a ransomware attack. Ask about their opinion on the subject. Outline step-by-step activities with them so that they knew exactly what to do.
In addition to creating the team, you need to make sure that managers know what their departments should do in case of ransomware.
Analysis of risks and business impact
You’ll need to analyze the risks and business impact twice: first as an estimation, then as an analysis of actual losses.
Risks are the outcomes of an incident that your business might face. These include but aren’t limited to the following:
- Data loss
- Downtime
- Ransom payment
- Legal fines or lawsuits
Business impact is all the possible consequences of the actualization of the risks for the business.
- Revenue losses
- Client losses
- Reputational losses
- Legal outcomes
How to stop ransomware
To stop cloud ransomware, you need to understand how it works. Cloud ransomware is a malicious application. Getting into your cloud environment like Google Workspace or Microsoft Office 365 requires one of your users to grant it OAuth access.
In most cases, cybercriminals use phishing and disguise ransomware making it look like a legitimate application.
That is why to stop an attack, you need to identify the point of access to your cloud environment and then revoke this access. Keep in mind that this procedure will not decrypt the files.
How to recover the data
Most modern ransomware strains encrypt all the previous versions of your documents. That is why a backup is essential. Keep in mind, however, that backups connect to the cloud via APIs. Both Google Workspace backup and MSO 365 backup have limitations on the number of APIs per minute.
That’s why the more data you have in your cloud environment, the more time you’ll need to recover it.
Here are some tips on how to tackle this problem:
- identify which data should be recovered in the first place, and which data in the last;
- prohibit the employees from using their work cloud drives to store personal data;
- encourage your workers to clean their drives from unnecessary files from time to time.
RTO, RPO, RPA, and RTA
RTO, RPO, RPA, and RTA should be important parts of your cloud ransomware disaster recovery plan.
RTO is the recovery time objective. It is the amount of time your business can spend with its data inaccessible without any significant damage to it.
RPO is the recovery point objective. It defines the maximal acceptable age of the data backup. In other words, how much data can you lose without damaging your business?
RTA is the recovery actual time. It is the actual time that your business will spend recovering your data.
RPA is the recovery point actual. It measures how much data you will actually lose to a cyber incident.
What to do in case of double extortion?
Double extortion is a relatively new feature of the recent ransomware strains. It enables the attackers to steal your data prior to encrypting it.
The goal is to use it as an additional pressure in the ransom negotiations. In some cases, depending on the quality of extorted data, cybercriminals can choose to use the stolen information for future cyber attacks or sell it on the Dark Web to other cybercriminals. It is often the case of service providers who keep the data of larger clients.
You cannot impact the double extortion unless you have ransomware protection that is capable of stopping the attack in the very beginning.
Should we pay a ransom?
The answer to this question heavily depends on multiple factors. Will you be able to identify the entry point of ransomware fast? Do you have a backup? How frequent is it? How much time will the recovery take? Is there double extortion?
You should also remember that decryption keys in possession of cyber criminals are often of low quality and might fail to recover all the encrypted data.
Stop ransomware and recover within hours with SpinRDR
To prevent ransomware incidents and minimize RTA and downtime, you can use SpinRDR ransomware protection.
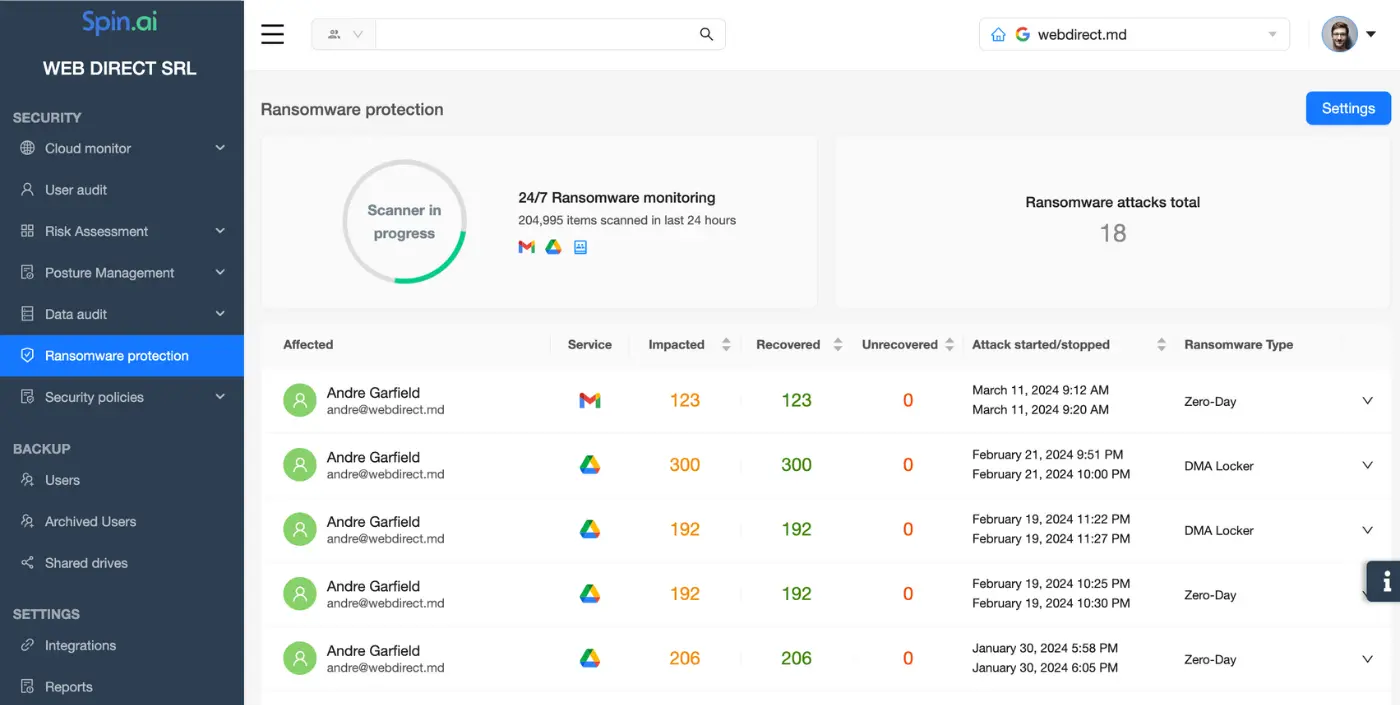
This tool is created specifically for Microsoft Office 365 and Google Workspace. It consists of backup and AI that monitors your cloud environment 24/7. Here’s how it works:
- AI uses APIs to monitor data behavior in your cloud.
- It detects ransomware within minutes after the onset of the attack.
- The AI identifies the entry point for ransomware and revokes access immediately.
- Then it recovers the files that have been encrypted from the backup.
Learn more about SpinRDR ransomware protection for Google Workspace and SpinOne ransomware protection for Microsoft Office 365.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


