Cloud Security Posture Management (CSPM) vs traditional security measures
With the development of cloud technologies, it became obvious that traditional security measures do not work. The new environment has different risks and challenges and thus requires different approaches. In this article, we compare Cloud security posture Management (CSPM) with traditional security measures.
Overview of Traditional Security Measures
When talking about traditional security architecture we imply the security of on-premises IT systems. With the rapid development of cloud technologies, many businesses decided to resign on-prem making it obsolete.
Let’s take a quick look at the traditional security architecture:
- Inner network
- Security perimeter
- Protected data center
The inner network is the system of on-premise machines that the company uses for its operations and data storage. In certain cases, data would be stored in a protected data center – also on-prem.
The security perimeter is the layer of devices and programs like firewalls that protect the inner network from the outer network, i.e., the Internet.
Data transmission within the network can also be gated. However, this practice has been used only by large organizations with hundreds of users.
The key idea of traditional security architecture is securing access to the system and that every device within the inner network is a trusted device.
What is Cloud Security Posture Management (CSPM)?
Cloud security posture management (CSPM) is a new approach to security architecture that was developed to meet the needs of the cloud environment.
Now, the cloud system is very different from the on-prem system. First of all, a user needs to be physically present in the office to be able to access the traditional on-prem solution. Later on, the organizations that still have this type of system introduced the capacity of remote users to access their on-prem solutions using layers of protection such as VPN and firewalls. This calls for a different cloud security.
When it comes to cloud solutions, a user only needs to have credentials and in some cases second verification device (e.g., a mobile phone). With that, they can access the cloud from any point in the world.
Furthermore, many cloud environments are also accessed by third-party OAuth applications. Many of these apps go unaccounted for due to the inherent lack of visibility within these environments.
Another problem with cloud environments is file-sharing functionality. File sharing provides so many benefits to the company operation-wise, like the opportunity to collaborate on the document and the reduction of back-and-forth sending of the new document versions. However, it also creates risks, i.e., incorrect sharing and the exposure of sensitive data to unauthorized people.
These factors make cloud systems very different from on-prem systems. That’s why traditional security architecture isn’t efficient against multiple different threats.
Cloud security posture management (CSPM) is a category of security solutions that were built to take into account the specifics of the cloud and its security needs.
CSPM focuses on:
- Control of sharing
- Monitoring user behavior
- Detecting misconfigurations
- Ransomware protection
- Control of risky applications
Cloud Security Posture Management (CSPM) vs Traditional Security Measures
Which one is better: CSPM or traditional security architecture? We’d say both are good for their respective environments.
Below we summarize the difference between CSPM and traditional security architecture.
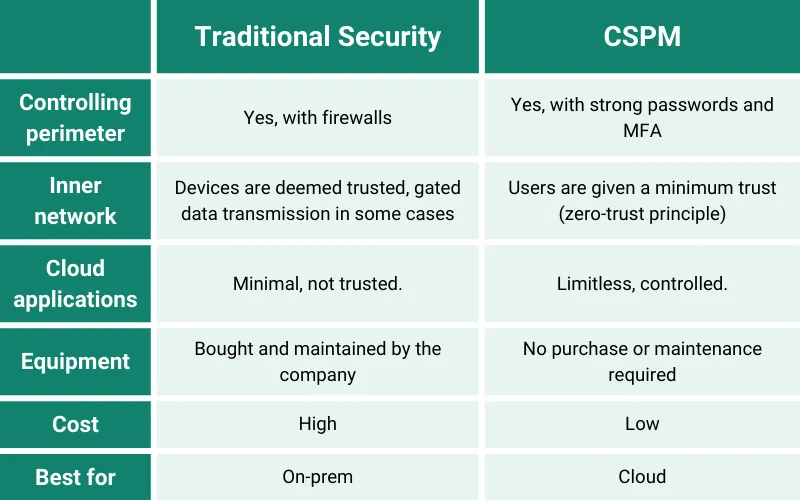
Since the majority of companies use hybrid cloud and on-prem environments, we highly recommend applying both approaches.
FAQ
What are the main benefits of using CSPM over traditional security?
The main benefit of CSPM over traditional security is that it’s specifically designed for the cloud and should be used for cloud solutions.
Can CSPM and traditional security measures be used together?
Yes, CSPM and traditional security measures can be used together in companies that use both on-prem and cloud systems.
How does the cost of implementing CSPM compare to maintaining traditional security measures?
The cost of implementing CSPM is lower than traditional security measures as on-prem security also requires special equipment.
What factors should a company consider when deciding between CSPM and traditional security?
The main factor is whether their system is cloud or on-prem.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Top 12 Slack Security Best Practices In 2024
Slack might feel like the digital version of your office break room with quick chats,...
Backup Microsoft: Securing Critical Business Data Across Microsoft ...
We all know Microsoft is a behemoth with all types of critical products used by...
Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security Web browsers are not just passive...