Data Leak Prevention (DLP) Best Practices for Cloud Applications
Data leak is a crucial area of attention for an organization’s overall cybersecurity posture. They are both dangerous and costly for organizations – how? How can businesses protect themselves from a data leak disaster? What are the DLP best practices? Organizations today produce, keep, and process massive amounts of data. As a result, most companies today have critical data vital to the business, and at least a subset of the data most businesses house is sensitive data. For example, sensitive data may include personally identifiable information (PII) data or credit card numbers (CCNs). A data leak can happen unintentionally at the hands of internal employees or misconfigured cloud infrastructure. Ransomware gangs are increasingly using the threat of intentional data leaks to pressure businesses into paying the ransoms demanded.
Data Leak – Dangerous and Costly
A full-on data leak or data breach can lead to high costs for businesses. The costs include financial costs directly related to a data breach, such as ransomware ransoms demanded. In addition, other costs include legal fallout, regulatory fines, and costly damage to brand reputation and customer confidence. The financial damage, including tangible costs and those that are not perceived, can lead to substantial damage to an extent the company never recovers.
The IBM Cost of a Data Breach Report 2021 noted the following costs and statistics associated with data breach events:
- 38% of the total breach costs was a result of lost business
- $180 – Cost per record containing personally identifiable information (PII) data
- 287 days – the average number of days to identify and contain a data breach
- $1.07 million – Cost difference when remote work is involved as a factor in the breach
- $4.62 million – Average total cost of a ransomware breach
- $4.24 million – Global average total cost of a data breach
- $5.12 million – Average total cost of a data breach when businesses have extensive cloud migration.
- $9.23 million – The healthcare industry retains the highest average cost of a data breach.
The costs listed above are not insignificant and certainly should cause businesses to pay close attention to the danger of data breaches, including cloud environments. As shown in the report, cloud migration increases the cost of a data breach. Often this is a result of the lack of visibility and data leak protection in cloud environments.
Data leak protection required by today’s regulatory compliance
As part of the increasingly stringent regulatory compliance requirements, businesses must implement measures to protect against data leaks, especially when sensitive personal information is involved.
Note the following guidelines documented in Art. 25 – GDPR Data protection by design and by default:
1)…the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organizational measures, such as pseudonymization, which are designed to implement data-protection principles, such as data minimization, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects.
2) The controller shall implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed. 2That obligation applies to the amount of personal data collected, the extent of their processing, the period of their storage and their accessibility. 3In particular, such measures shall ensure that by default personal data are not made accessible without the individual’s intervention to an indefinite number of natural persons.
GDPR and many other compliance regulation requirements mandate that companies put in place the technical safeguards needed to protect personal information from data leaks. If found negligent in proper data leak safeguards, GDPR fines are extensive and allow the EU’s Data Protection Authorities to issue fines of up to €20 million ($24.1 million) or 4% of annual global turnover (whichever is higher). Regulatory fines alone help impress upon businesses the need for protecting confidential and sensitive data from leaking into the wrong hands.
Cloud SaaS data leak – how it happens
Organizations are increasingly using cloud SaaS environments such as Google Workspace and Microsoft 365 to house business-critical data. In these environments, data leaks can quickly happen. How? Cloud SaaS data leaks generally happen in the following ways:
- Shared data by end-users
- Leaky cloud applications
- Ransomware
1. Shared data by end-users
Cloud SaaS environments make data sharing extremely easy. By default, with a few simple clicks, end-users can share data with others inside the organization or with external users outside the organization. Unfortunately, accidentally or intentionally sharing sensitive data can easily lead to a data leak event costing businesses millions.
2. Leaky cloud applications
Cloud applications found in cloud SaaS environment marketplaces allow businesses to add missing or needed features or capabilities in their cloud SaaS environment. For example, the application marketplaces found in Google Workspace and Microsoft 365 contain thousands of cloud apps with robust features. However, there is a danger of data leaking into the wrong hands if a cloud application is either not written with security in mind or is all-out malicious, leaking or stealing data intentionally.
3. Ransomware
In addition, attackers are now combining ransomware with the threat of data leaks. New ransomware variants threaten to release sensitive data to the Internet to increase pressure on businesses to pay the ransoms demanded. Unfortunately, this strategy often pays off for ransomware gangs.
Ransomware will increasingly target cloud environments beyond 2021 as more organizations leverage cloud SaaS environments to house business-critical data. As a result, businesses must close the gap on data leaks to strengthen their overall cybersecurity posture.
Improve DLP (Data Leak Prevention) with SpinOne
SpinOne’s robust data leak visibility and controls allow businesses to protect against data leaking out of the sanctioned boundaries of the cloud SaaS environment. The platform adheres to the Google Workspace DLP best practices to protect SaaS cloud data from leaks. Using SpinOne, organizations have clear visibility of where data is shared, who shared it, when it was shared, and to whom it was shared.
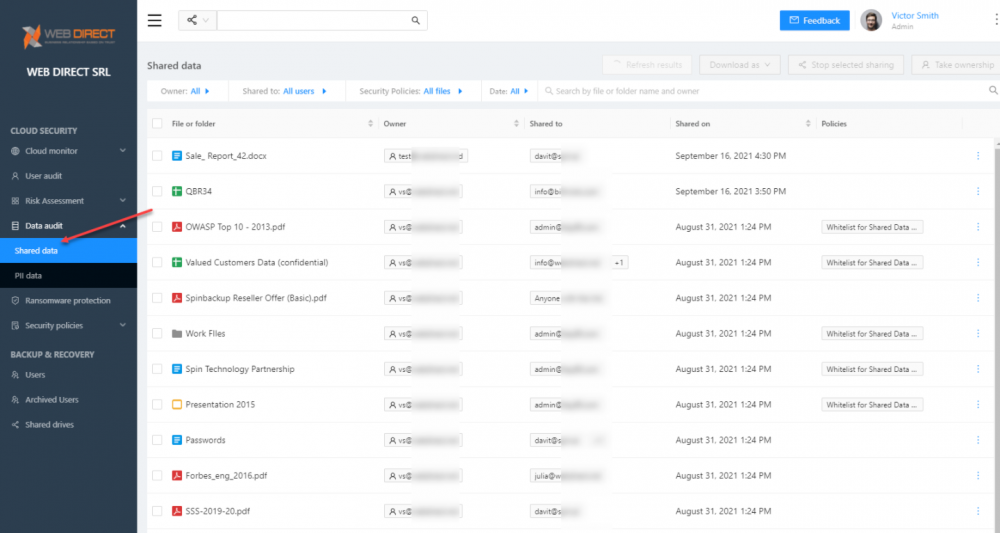
Using SpinOne’s Data audit dashboard, IT admins have quick visibility into data shared organization-wide.
The shared data dashboard provides visibility to data-sharing information
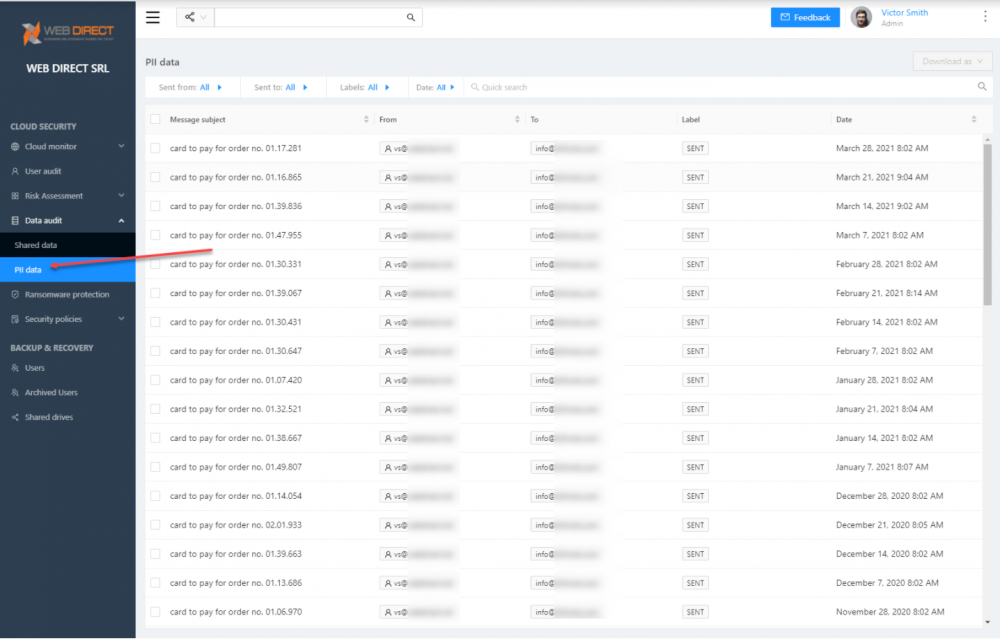
What about data specifically containing PII information? As part of the Data audit module, the PII dashboard allows quickly seeing redacted PII information sent via Exchange Online.
Viewing shared PII information using SpinOne
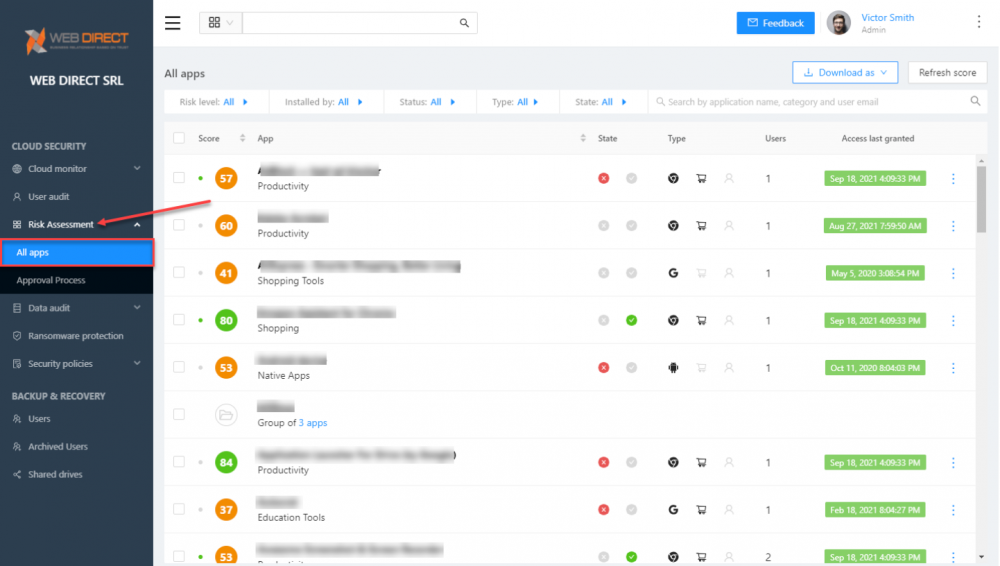
What about leaky or otherwise unwanted cloud applications? SpinOne’s Risk Assessment module allows businesses to have visibility into applications integrated into the environment and either allow or block applications based on the risk score provided by SpinOne.
SpinOne application risk assessment
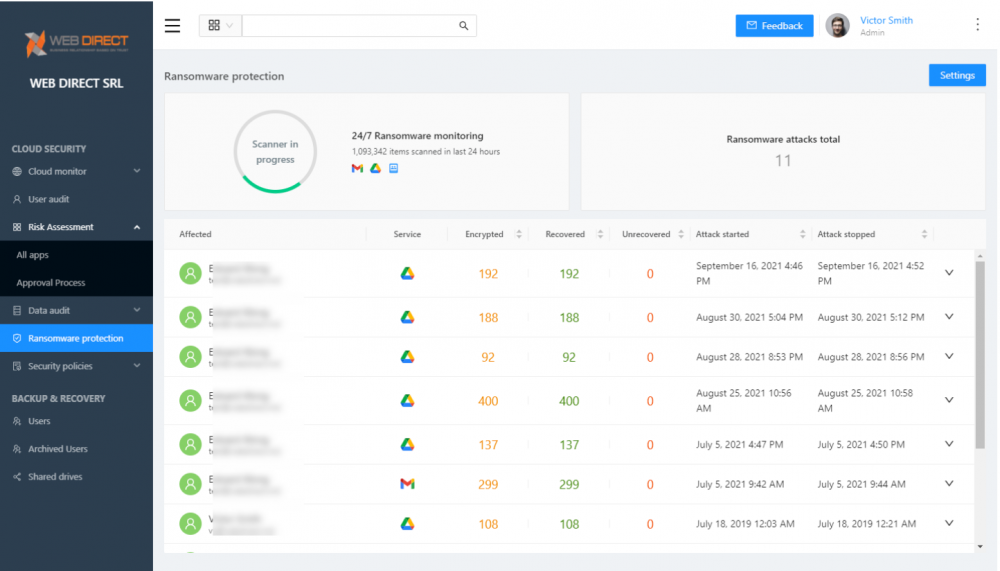
Finally, the SaaS Ransomware protection module provided as part of SpinOne provides industry-leading ransomware protection that is fully automated and powered by next-generation artificial intelligence (AI) and machine learning (ML) algorithms.
The automated Ransomware protection module provides the following benefits:
- Scans the environment for signs of a ransomware infection
- If ransomware is detected, SpinOne automatically blocks the process at a network level
- SpinOne scans the environment for any affected files
- Any affected files restored automatically from backup (configurable)
- IT admins are notified
By quickly stopping any ransomware attack in the cloud using SpinOne’s automated processes, organizations eliminate ransomware data leaks.
The protections provided by SpinOne are automated and take the heavy-lifting out of protecting cloud SaaS environments from data leaks. In addition, the visibility and automated remediations offer a level of protection not found using built-in cloud SaaS tools and solutions.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...