How to Implement an Ultimate SaaS Safety Plan
Maintaining the availability to data and services are two of the most important technical feats that businesses today must achieve when protecting business-critical IT infrastructure. For decades, the traditional server backup has been protecting on-premises files, folders, and business applications for SMBs. As digital information and data have become an integral part of business operations for most organizations, protecting these digital resources is a mission-critical task that must be taken seriously.
The complexity and the diversity of workloads and business-critical resources have continued to grow as organizations today are increasingly migrating resources to the public cloud. They are making use of Software-as-a-Service (SaaS) offerings provided by the major public cloud vendors such as Amazon, Google, and Microsoft. The possibilities, functionality, and capabilities of today’s public cloud SaaS offerings are allowing today’s businesses to move at lightning speed and agility as well as have access to infrastructure that would simply not be possible by provisioning on-premises infrastructure.
As a downside, the addition of public cloud SaaS resources to the infrastructure of today’s SMB enterprise environment, as well as the tremendous migration of infrastructure resources to the public cloud, have greatly increased the complexity of both business continuity and disaster recovery. The lines have been blurred between on-premises and cloud environments. Critical resources and services now can exist both on-premises and in the public cloud. Traditional data protection solutions that were designed for on-premises environments.
What do organizations need to do to properly protect their Software-as-a-Service infrastructure? Let’s take a look at how to implement an ultimate SaaS safety plan. What does this involve? How can organizations easily implement the required aspects of a SaaS safety plan?
What is Involved in Protecting SaaS Infrastructure?
There are several facets to being able to properly protect Software-as-a-Service infrastructure. Even though Software-as-a-Service offerings exist in the public cloud infrastructure of the world’s leading providers such as Microsoft or Google, this does not mean that protecting your data is not important. In fact, many organizations make the disastrous mistake of simply trusting the public cloud provider to ensure data integrity and availability. However, this type of thought process is short-sighted. What about security concerns in a Software-as-a-Service offering? Is the security that is provided by public cloud vendors enough for organizations housing resources in the SaaS environments?
What about Data Leakage?
Let’s take a look at the following aspects of protecting public cloud SaaS offerings and see why they are important:
- Software-as-a-Service Data Protection
- Data Privacy and Data Leak Protection
- Cybersecurity
Implementing both data protection mechanisms as well as cybersecurity capabilities into the Software-as-a-Service environment will help to ensure that data is both protected from accidental and intentional deletion as well as protected from malicious attacks or attempts to steal data. Going hand-in-hand with the cybersecurity aspect, making sure to implement features that helps to ensure Data Privacy and Leak Protection is essential in today’s world of high-profile news headlines featuring leaked data from large online customer databases, etc. When formulating an ultimate safety plan in regards to Software-as-a-Service offerings, businesses need to consider all aspects of threats to data that is housed in public cloud SaaS environments.
Software-as-a-Service Data Protection
Organizations may assume that since they are entrusting their data to a large public cloud vendor such as Microsoft Office 365 and Google G Suite, there is no need to protect their data. However, your data is your responsibility and the public cloud vendors will readily tell you that at the end of the day, you are responsible for data loss that may happen. Public cloud platforms provided by Microsoft and Google provide high-availability of your data, but not built-in recoverability. There is a difference.
If you look at the offerings currently provided by Microsoft and Google for recovering your data, they provide little to no options for true, versioned, controllable backups of your data housed in their Software-as-a-Service offerings. Microsoft only recently added the ability to recover a different version of your file in Office 365 OneDrive. Additionally, you can only recover a version within the last 30 days at this point, and no options to recover data in any of the other Office 365 services, only OneDrive. Google does not fair any better, if not offering fewer options to organizations housing their data there. The closest thing that Google offers in this regard would be the Google Vault, which is not meant to be a data protection platform, but rather an archival solution for legal and other regulatory and audit requirements.
An ultimate SaaS safety plan must include data protection with the following characteristics:
- Protection for all services in either the Office 365 or G Suite public clouds
- Multiple restore points in time
- Effective Versioning
- Ability to control retention
- Secure backups
- Effective archiving
- Ability to restore data easily
- Ability to migrate data easily
- Ability to recover items that have been deleted
Data Privacy and Data Leak Protection
Equally critical and part of an organization’s overall security strategy, but deserving of its own attention, is data privacy and data leak protection. There have been all too many cases of organizations making the news headlines for the leaking of customer data. These types of headlines are never good for business as it can tarnish business reputation and customer confidence. Both can potentially be catastrophic for a business and possibly reasons they never recover from such an event. Data privacy and Leak Protection are two very crucial cloud security concerns, especially when thinking about Software-as-a-Service solutions that are hosted in the public cloud.
Most businesses traditionally have control systems in place with on-premises networks that allow keeping information within the bounds of the on-premises infrastructure. Control systems such as network policies, role-based permissions, and firewall rules can be familiar on-premises means to help control how data is transmitted. However, it can be challenging once the decision is made to incorporate Software-as-a-Service infrastructure into the overall business-critical infrastructure. Public cloud infrastructure, services, and systems, can be unfamiliar, and present challenges to the traditional methodologies of controlling data and ensuring data privacy.
Additionally, the public cloud vendors often have many different disjointed systems for controlling data leak and security in general that unless businesses have well-versed public cloud architects on staff, these can be confusing and are often improperly implemented. Implementing an ultimate SaaS safety plan involves ensuring that data is kept in its proper place and data privacy is enforced. These can be challenging since public cloud environments can generally be accessed from anywhere, from any device, and from any network. Businesses can find themselves struggling to have the visibility needed to how data is being access and from whom.
With new compliance regulations such as the General Data Protection Regulation or GDPR, infrastructure systems must be implemented with privacy by design. This means that data privacy and security are not afterthoughts and are part of the design of the infrastructure system. This includes Software-as-a-Service systems and offerings that may be used by organizations today.
A huge threat to Software-as-a-Service systems that are utilized is BYOD devices and also end users granting permissions to third-party applications that do not need or are authorized to have the access they may be requesting to sensitive company data. It has often been noted how end users will blindly grant requested permissions from a third-party app to data without thinking about the possible implications.
As part of an ultimate Software-as-a-Service safety plan, businesses must have visibility to, audit, and monitor the access to corporate data housed in SaaS platforms and see who is access the data and which applications are granted permissions on the data. This type of visibility can be difficult to achieve with the native tools provided by public cloud vendors. This will most likely require effective third-party tools that allow customers to see the environment transparently and intelligently analyze user activity and behavior metrics.
Cybersecurity
Cybersecurity is essentially important. Organizations who do not invest in securing IT infrastructure are asking for trouble. In fact, even those who do put proper emphasis on security are still at risk and most organizations at some point will experience a breach in security. There is certainly no shortage of attackers looking to capitalize on vulnerabilities and gain access to business-critical systems. This can lead to further compromise, data leakage, and also to the destruction of data depending on the motives of the attacker.
Traditional security mechanisms for on-premises environments are generally much more familiar to businesses who may as of yet, not migrated resources to the cloud. Security in the public cloud can be intimidating to many based on the lack of familiarity and understanding of proper security mechanisms for public cloud environments. The traditional approach of an on-premises firewall filtering all ingress traffic to the on-premises environment does not really translate to the public cloud. Additionally, this approach does not scale very well either.
Communication with Software-as-a-Service offerings may happen from many different networks, devices, and geolocations. The ultimate SaaS safety plan in the public cloud needs something more powerful and secure than the traditional firewall guarding the perimeter network as with public cloud, there really isn’t a perimeter network per se.
Cloud Access Security Brokers
Cloud Access Security Brokers or CASB technology is a great way to allow securing public cloud SaaS environments and certainly fit in as part of the overall ultimate SaaS safety plan. Cloud Access Security Brokers or CASBs, allow organizations to enforce the same policies and access restrictions in the public cloud as exist on-premises. The two types of CASB technology, the firewall-based and API-based CASB, each provide protection for public cloud environments. However, the API-based CASB approach is much more powerful. The API variant of CASB technology requires no reconfiguration of the clients to use a “proxy” address, does not have to be “inline” with the client’s connection to the public cloud SaaS environment and allows the CASB to essentially become part of the public cloud SaaS environment. This means the solution scales extremely well. By implementing API-based CASB technology, organizations can effectively implement and enforce corporate data access and security policies in the public cloud.
CASB technology also allows businesses to have a system that can “intelligently” monitor the public cloud SaaS environment with cutting-edge machine learning. This means the systems constantly has “eyes on” the environment 24×7. As we will see, this type of technology can be extremely powerful in monitoring and protecting public cloud environments. Depending on the capabilities of the CASB technology, it can proactively learn based on the data gathered from the public cloud environment. By using this information, it can then dynamically and intelligent make decisions and perform remediation.
Ransomware Protection of SaaS Data
A huge concern in the realm of cybersecurity today is Ransomware. Ransomware is equally as dangerous when it comes to public cloud storage. Software-as-a-Service offerings generally host public cloud storage that businesses can take advantage of for storing business critical data. Both Microsoft and Google offer synchronization utilities that allow synchronizing on-premises files up to the public cloud. This in turn means that ransomware can be automatically copied to the public cloud via a sync operation. Additionally, any files that are corrupted by ransomware are then synchronized to the public cloud since the encryption process simply makes the file appear to have changed or have been modified. This triggers the sync to take place which will replace the good version of the file in the cloud with a corrupted, ransomware encrypted version.
Cybersecurity is especially concerning for organizations today. This is especially true for organizations that may be thinking of migrating to the public cloud or have already migrated and who do not have a good understanding or implementation of security in the cloud SaaS offering. Having the right tools and capabilities to proactively monitor, protect, and remediate against threats to the public cloud SaaS environment is really the really effective way to be able to confidently protect public cloud Saas. Native public cloud tools provided by the likes of Microsoft and Google are lacking in their ability to provide businesses today with a streamlined, cohesive look at the overall security stance of SaaS environments.
Spinbackup – Integral to the Ultimate SaaS Safety Plan
Providing an ultimate safety plan for SaaS environments in the public cloud is a challenge that businesses today must meet head on. This is no trivial undertaking. Providing safety for data that is housed in the public cloud might seem like a monumental task. After all, as mentioned, data can be accessed, in many cases, much more freely if left to default designs. The native public cloud Saas tools are either non-existent or weak in the ability to provide the tools and protection needed for data stored in the public cloud. As already covered, both Microsoft and Google do not have a proper data protection mechanism natively built into their SaaS solutions. At best, both have archiving abilities that do not really satisfy data protection, but which some businesses may attempt to utilize to satisfy this requirement. Proper security and data leak protection is either disjointed, not cohesively implemented, or features are simply lacking.
Spinbackup provides the answer for businesses looking for a single solution that provides both a data protection solution as well as a cybersecurity/data leak protection solution for public cloud SaaS environments. It effectively achieves the needs of businesses who migrate to public cloud Saas environments with a three-fold approach in a single product. This includes data protection, data leak protection, and cybersecurity, all in a single product. Let’s look briefly at the key Spinbackup features that allow effectively protecting and securing public cloud SaaS from both Microsoft and Google.
Spinbackup SaaS Data Protection
The Spinbackup SaaS data protection solution is a state-of-the-art solution that effectively implements secure, robust, and efficient backups of public cloud SaaS. Microsoft has only implemented basic restore capabilities up to 30 days for OneDrive files only and no other services and Google has as of yet implemented any restore functionality for Google Drive. Spinbackup protects ALL services included in the public cloud SaaS offerings from both vendors. This ensures that no matter which service you need to recover, Spinbackup has you covered.
Spinbackup SaaS data protection includes:
- Automatic backups up to 3X daily
- Efficient incremental backups
- Secure backups that are encrypted in-flight and at-rest
- Unlimited retention
- Versatile recoverability including deleted files
- Effective versioning
- Automatic recovery with Ransomware protection (more below on this topic)
- Easy migration of resources
Spinbackup allows protecting your public cloud SaaS environment like it is an on-premises resource with the familiar control, visibility, and protection afforded by most on-premises modern backup solutions. This allows organizations to house business-critical resources in the public cloud with confidence, knowing files can be recovered quickly, effectively, and efficiently. Additionally, Spinbackup allows restoring files to another user account. This means you have a powerful migration utility built into the Spinbackup solution to handle employees leaving or other change of duties that requires migrating resources around to different user accounts.
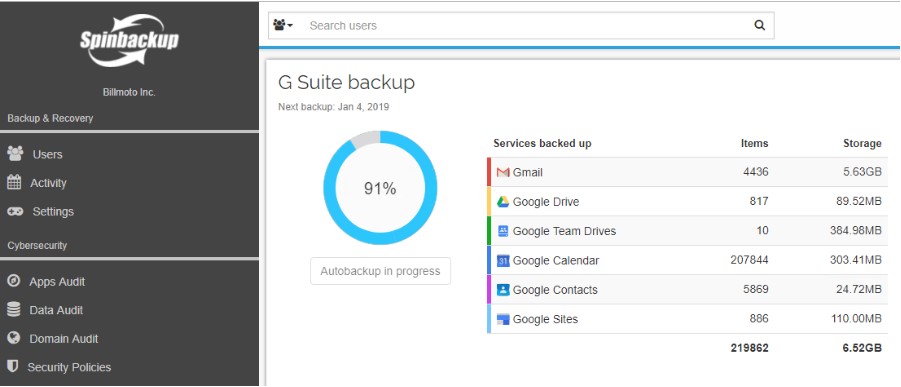
Spinbackup allows easily seeing the protected data in the G Suite environment
Spinbackup Data Privacy and Data Leak Protection
What about Data Privacy and Data Leak Protection? Spinbackup is an API-driven CASB solution that intelligently allows organizations to implement the same on-premises policies in the public cloud SaaS environment. This ensures that data restrictions and acceptable use are adhered to in the SaaS environment. Spinbackup provides modules that allow effectively having visibility to how data is being accessed. Also, businesses can define and prevent sensitive data from leaving the boundaries set in the SaaS public cloud environment. Sensitive data such as credit card numbers, social security numbers and others can be flagged and prevented from leaving the public cloud environment. Data movement can be monitored as well. What if an employee attempts to inappropriately download data from the sanctioned public cloud environment to a personal public cloud or possibly to a personal local hard drive? Spinbackup gives visibility to and can prevent these types of actions by employees who may be unscrupulously attempting to access data inappropriately.
Third-party applications pose a tremendous risk to SaaS environment data. Employees may blindly allow permissions to data they have access to and grant these permissions to third-party applications that request them. Spinbackup can audit and remediate these types of permissions that may be granted to “risky” third-party apps. Risky applications can pose a serious data leak danger to organizations housing business-critical and sensitive data in public cloud SaaS environments. To recap the capabilities that Spinbackup affords to organizations:
- Sensitive data protection – Prevent leakage of sensitive data such as credit cards and social security numbers.
- Data Audit dashboard – See who has access to data, both inside and outside the organization.
- Data access remediation – Remediate access and have the ability to revoke unauthorized access.
- Third-party apps control – prevent and deny risky third-party applications from accessing data.
- Alerting and notifications – By way of effective alerting and notifications, Spinbackup allows organizations to have proactive alerts to have visibility to data leak events so administrators have real time visibility to these events.
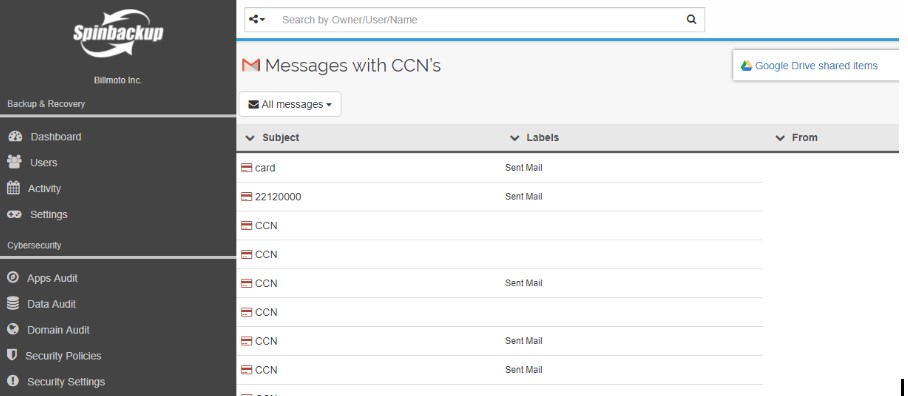
Spinbackup provides sensitive data protection and visibility
With these and other powerful mechanisms, Spinbackup allows organizations to prevent the leakage of sensitive data and also to ensure data privacy. What about overall cybersecurity?
Spinbackup Cybersecurity for SaaS Data
The robust cybersecurity capabilities provided by Spinbackup allow businesses to secure their SaaS environments effectively. Effective cybersecurity starts with visibility. This is what Spinbackup is able to deliver to organizations utilizing public cloud SaaS environments. The Spinbackup Domain and Data auditing dashboards allow administrators to have a transparent view of all user activities taking place in the environment. Additionally, these can be sorted and queried based on the type of events in the environment.
Alerting and notifications allow real-time proactive alerting on cybersecurity events seen in the environment. Additionally, Spinbackup will send a daily security summary email.
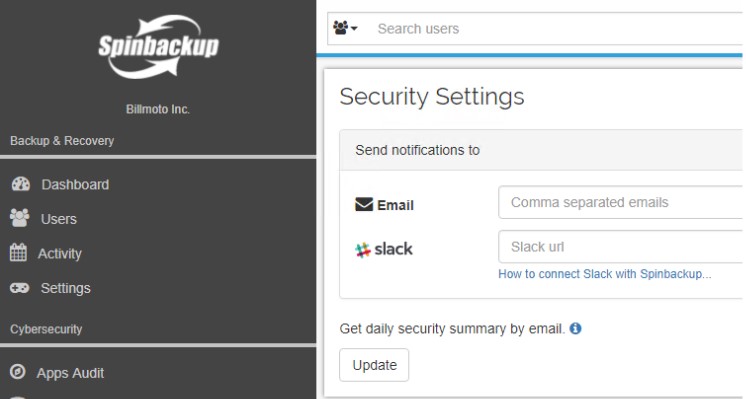
Spinbackup daily Security summary by email or Slack
With Ransomware, Spinbackup’s machine learning algorithms are constantly monitoring the environment for potential ransomware activity. When ransomware activity is detected, the ransomware process is blocked and any files that may have been affected by ransomware encryption are automatically restored! This means without any administrator intervention, remediation actions can be taken and file access restored to a healthy version of the file. This provides an automated approach to business continuity in public cloud SaaS.
In addition to the ransomware protection, Spinbackup protects against insider threats that come by way of accounts that may have been compromised, or employees that may have questionable behavior. The machine learning intelligence once again listens to and watches the environment for signs of any undesirable behavior. This could include an inordinate number of failed logins, or suspicious logins from out of the ordinary geolocations.
Spinbackup Cybersecurity for SaaS Data:
- Ransomware protection
- Insider Threats Detection
- Domain and Data Audit
- Daily Security summary report
- Real-time notifications and alerting
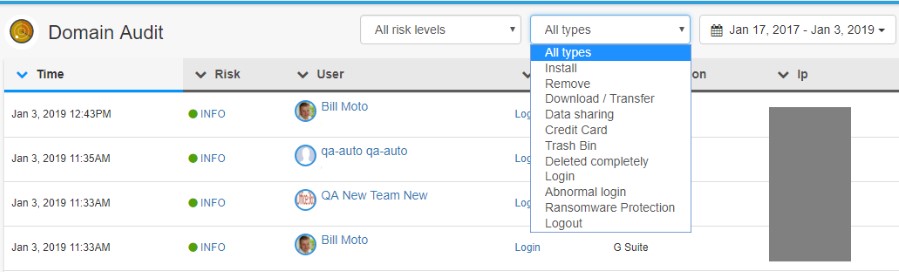
The Domain Audit provides visibility into cybersecurity events
Concluding Thoughts
Software-as-a-Service environments are becoming an increasingly important component of business-critical infrastructure that is housed in the public cloud. Protecting data that is housed in the public cloud in SaaS environments such as Office 365 and G Suite is crucial. It can be a major challenge for organizations today to effectively protect, secure and monitor Software-as-a-Service environments properly, especially by way of only the native tools provides by the public cloud vendors. With Spinbackup, businesses have a truly effective way to ensure an ultimate safety plan for their SaaS environment.
Spinbackup can backup, secure, and monitor SaaS environments, all with a single-pane-of-glass product performing the heavy lifting. Spinbackup provides the ultimate in public cloud safety for organizations who have already started migrating their data or who are looking to migrate their data to the public cloud by way of a SaaS offering. Not only can you implement a safety plan for your data with the Spinbackup solution, you can implement an intelligent, robust, and machine learning enabled 24×7 means to protect and secure your data. This ensures confidence in SaaS data and allows businesses to spend their time and energy focusing on other important business objectives.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


