How to Protect Against Ransomware: 9 Best Strategies in 2024
Ransomware has become one of the most impactful cybersecurity threats over the past years. Besides paying huge ransoms to criminals and regulatory fines, businesses suffer downtime and strong reputational damages In 2024, organizations reported an average cost of $2.73 million from a ransomware attack considering downtime, people time, device cost, network cost, lost opportunity, etc., and excluding any ransoms paid. Furthermore, ransomware recovery time is getting steadily longer, with one-third (34%) now taking more than a month to recover.
At the same time, the profitability of ransomware is flourishing due to the simplicity of the ransomware-as-a-service model. Ransomware criminals shifted focus to the industries that have little option but to pay, such as healthcare, small and medium businesses (SMB), governments, critical infrastructure, NGOs, and education. Attackers are aware that these industries handle sensitive data, frequently face challenges in funding their IT resources, and are often bound by regulations that hinder their ability to effectively utilize backups and use all possible opportunities to deliver ransomware.
Strong foundational security is a must to protect against ransomware. This includes (but is not limited to) endpoint, email, and firewall technologies. Automated ransomware detection and response tools provide cyber defenders with new tools for rapidly identifying ransomware and automating responses to those threats.
In this article, you will find 9 viable strategies for 2024 to protect against ransomware and learn what are the best tools that can help you with this.
What is Ransomware
If you do not protect your organization from ransomware, it’s only a matter of time before you fall victim.
Ransomware is a type of malware that blocks access to a computer system and/or encrypts data until a victim pays a ransom. Typically, attackers demand payment in exchange for restoring access to the affected system or data. Ransomware can spread through phishing emails, infected websites, or software vulnerabilities, and it poses a significant threat to individuals, businesses, and organizations by disrupting operations and potentially leading to data loss.
Attackers then hold the data hostage until a ransom is paid. After receiving a payment, criminals provide encryption keys to unlock and normalize the data,
The early signs of ransomware spreading across the organization’s systems are hard to notice, even for experienced users. Usually, once the encryption process is completed and the damage is done, the attackers deliver a ransomware note, notifying users of the ransomware infection and demanding a ransom.
Learn about what to do with the ransomware and the common steps to take during the ransomware attack.
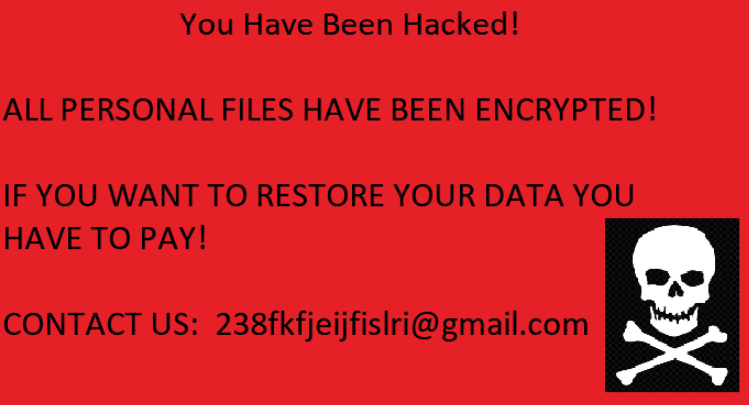
The ”Ransom” note left on the desktop of an infected workstation
Types of Ransomware
Over the past 30 years since its initial appearance, ransomware has developed into one of the most effective tools in cybercrime. Today, various types of ransomware differ in how they affect systems, their methods of attack, and the techniques used to extort victims. Today, the most popular ransomware types include:
Encryptors (full and non-full). Encryptors are classic ransomware types that encrypt files and their versions, typically allowing recovery with a decryption key. The 2016 Petya ransomware is a notable example, initially targeting specific files before evolving into full disk encryption.
Leakware. Leakware steals data before encrypting it. Attackers then threaten to publicly release or sell the stolen data if the ransom is not paid, a tactic known as double extortion. Some variants escalate to triple extortion by involving third parties, such as customers or partners, and threatening to expose their data as well. This approach was first noticed in 2020 with the REvil group targeting the law firm Grubman Shire Meiselas & Sacks, pressuring victims to pay to prevent sensitive information from being leaked.
Ransomware-as-a-Service. Ransomware-as-a-Service (RaaS) is a model where hackers offer ransomware tools and infrastructure to other cybercriminals on a subscription basis. These “clients” pay to use the ransomware for attacks and often share a portion of the ransom with the service providers. The DarkSide ransomware group operates using this model and gained notoriety in May 2021 when they targeted the Colonial Pipeline.
How Can Ransomware Infiltrate Your Environment?
There are many ransomware delivery vectors, but one of the most commonly used one is a phishing email. . Using social engineering techniques, criminals send phishing emails urging users to click a malicious link, open an attachment, or urgently respond. Once their request is satisfied – e.g. a malicious attachment is open – ransomware infects your organization’s system and encrypts files.
Many ransomware variants can evade traditional antivirus protection, posing a challenge to its effectiveness. These ransomware variants can then encrypt critical files, folders, mapped network drives, and any other resources the end-user has permission to access.
One of the avenues for ransomware infection that ties on-premises environments to the Google Workspace (a former G Suite) public cloud SaaS environment is file synchronization. Google Workspace offers installable utilities to synchronize files from on-premises end-user devices to the Google Workspace cloud. If ransomware infects an end-user device, it will begin encrypting files that will then be synchronized to the Google cloud. The ransomware encryption process is viewed as a change in the file, which will trigger the synchronization process.
Ransomware Can Infect Public Cloud
There are still huge misconceptions regarding public cloud environments and ransomware. Many businesses with untrained or naive and inexperienced personnel may think that once data enters the realm of a public cloud SaaS environment such as Google Workspace, their data is immune to the effects of ransomware infections that wreak havoc on-premises. However, this is far from the truth.
The significant advantage of public cloud SaaS environments comes from high availability, which is achieved through world-class data centers and robust failover systems integrated into the underlying technologies that support these services.
However, this should not be confused with backups and data protection. While Google, Microsoft, and others are introducing the most basic nuances of data protection, these in themselves are not and should not be considered backups.
Google Workspace has the ability to restore data in a rudimentary fashion of “versions” of files in their cloud storage as well as a “recycle bin” of sorts that allows “un-deleting” files that have inadvertently been deleted either accidentally or intentionally by end-users for up to 30 days.
Read more on how to recover deleted files from Google Drive.
While businesses may be potentially leverage the file versions to recover data, this is not a method that can be relied upon for wide-scale protection of business-critical data hosted in the public cloud. Ransomware is greedy and destructive to any data it touches.
What if ransomware-infected files are not discovered in the 30-day window of time for recovery? What if businesses need to restore a “version” of a file that what not captured by the versions in cloud storage? What if there are services affected by ransomware outside of Google Workspace storage, such as email? “RansomCloud,” a term coined for a ransomware variant able to encrypt cloud-based email, offers the smoking gun to show that even public cloud email is at risk for ransomware infection.
Currently, only the Google Workspace cloud drive storage is available for the recovery of various versions of data. What about email? What about any other services that may potentially be infected by ransomware or a yet-to-be-utilized ransomware attack that targets other cloud services contained in SaaS services like Google Workspace?
All of these and many other questions lead to the conclusion that more is needed in the way of backups for data stored in the public cloud. This can not be stressed enough – backups are essential to surviving a ransomware attack on-premises and in the cloud.
The meager data protection provided as a native feature in Google Workspace cloud storage is not sufficient for surviving a massive ransomware attack in a Google Workspace environment. Organizations need an enterprise data protection solution that provides proper backup functionality for data stored in the Google Workspace SaaS environment that allows proper versioning, retention beyond the 30-day limit imposed by Google with their file versions, automation, powerful restore functionality, migration features, and many other features and functionality that provide proper protection for public cloud Saas like Google Workspace.
How to Protect Against Ransomware
- Backup your data regularly
If you don’t have a robust Data Loss Protection (DLP) plan, all your security strategies will fall apart. The core of all the DLP plans is having a ransomware-proof backup that will let you restore data in case you get hit. Backup is literally the first thing you must take care of, so if you don’t have one, set everything aside and start tackling this task.
What you should remember when implementing your backup plan is that backups are not ransomware-proof by default. It means that if your systems are hit with crypto-ransomware, it will slip into the backup copies as well, leaving you with empty hands.
If your backup provider doesn’t have inbuilt ransomware protection, you need to implement the following backup tactics:
1. Stick to the 3-2-1 rule – have a minimum of three copies of your backup, on two mediums, keeping one copy offsite;
2. Backup your data at least three times a day;
3. Enable version control to be able to restore different versions of your data;
Here is the full article about the Ransomware backup strategy→
An easier way – you can choose a backup provider with inbuilt ransomware protection. Very few providers on the market grant ransomware protection coming with backup services, making the backed-up files isolated and airtight.
Ransomware-proof backup software – SpinOne
We recommend SpinBackup as a highly secure cloud-to-cloud backup solution for Google Workspace and Office 365 data. It covers many the security and compliance issues, providing you with 24/7 ransomware protection that:
- Identifies and blocks the ransomware source
- Alerts you about the incident
- Stops the encryption process
- Identifies the number of damaged (encrypted) files
- Runs a granular recovery of encrypted files from the last backed up version
If you get hit, your backups will remain sealed and the encrypted files will be restored right away.
Also, note that there are no strings attached:
- You don’t need to install any software (everything is web-based)
- You can start from 5 licenses and choose a monthly subscription
SpinOne offers a 15-day trial of backup + ransomware protection for Google Workspace and Office 365 data.
How does Spin ransomware protection work? Watch this video:
2. Install antivirus software
Another must-have desktop protection is having an antivirus. Of course antivirus, no matter how good it is, won’t entirely protect you from ransomware (if you thought otherwise, check out why antivirus doesn’t protect against all types of ransomware ). And yet, an antivirus program is a necessary line of defense that secures your devices from viruses, adware, worms, trojans, and others.
How does antivirus help against ransomware, you may ask? It’s simple: since ransomware is often spread as downloadable malware, there is a chance that antivirus will detect and block it before it encrypted any files.
Don’t know where to look for the right software?
Here is the list of patch management software by rating and the list of endpoint antivirus software by rating
3. Use firewalls
A firewall is your first line of defense or your computer network gatekeeper. Contrary to antivirus software, which requires a very small effort to set up, firewalls usually require special knowledge. Firewalls may come as a piece of software or even hardware, which operates between the user device and the Internet. To put it simply, a firewall is a gatekeeper for the incoming traffic, which may contain a ransom code.
A firewall detects all possible exploits in your network and shields them. Also, it minimizes the risk of lateral movement inside your network and filters all the inbound and outbound traffic. It allows blocking any unsolicited and suspicious websites and attachments.
Don’t know where to look for the right software?
Here is the list of the most popular firewall software by rating
4. Conduct application audit
Employees download and use hundreds of third-party apps and extensions every day. No wonder they are becoming a common channel of malware infections, including ransomware.
These risky applications can contain malware that is deployed when a user provides such apps access to their corporate data.
For example, an employee installs an app that allows signing documents online; in order to function, this app requests different kinds of permissions – to Google Docs, local folders, email, and so on. When the permissions are granted, this app can inject ransomware code to every location it has access to.
This risk with apps is a part of a bigger problem called “Shadow IT”, which we fully address in the article Shadow IT management: rules and tools. But here are some fundamental rules that can eliminate your risk of being infected:
1. Create a procedure for the application approval and the evaluation criteria;
2. Create an ever-growing list of allowed and blocked applications;
3. Prevent users from accessing the blocked applications within your domain;
4. Monitor, assess, and block (if needed) all unauthorized apps connected to your domain.
If you manage a Google Workspace domain with many users, we advise you to use specifically dedicated application audit tools for these purposes. Otherwise, it is almost impossible to track what users download, what permissions they grant to applications or extensions, and whether the app is risk-free.
Application audit software – SpinSecurity (for Google Workspace users)
5. Filter emails for spam
Phishing emails with malicious links in them are confirmed by cybersecurity experts to be the leading cause of ransomware, being responsible for 67% of successful attacks in 2019-2020. Logically, by reducing the number of phishing emails your employees get, you decrease the likelihood of employees clicking on the link.
There are a few ways to set up phishing and malware protection for your email:
1. If you use Google Workspace as your business suite, follow the steps on this page.
2. If you use Office 365 as your main suite, check out this page for anti-spam protection and this pagefor anti-phishing protection.
Don’t know where to look for the right software?
Here are the best email security tools by rating if you look for a third-party solution.
Check out 10 types of ransomware you need to stay away from in 2020 →
6. Manage access properly
Many organizations have a clear understanding of job roles and who does what within their team, but only some manage computer user roles as attentively as required.
You have to determine the users and the data access they have. It should be clear, who can write to a database or specific data set within your database, and how to temporarily acquire or surrender a role in the case when an employee gains new responsibilities – all these processes should be planned. Having a correct employee exit procedure is important as well.
Moreover, for maximum transparency, safety, and efficiency we recommend tracking as many user activities as possible. Having proper software can minimize the human factor and keep your corporate network safe even in case your employees fail to follow your cybersecurity guidelines.
If you are an Office 365 user, you may want to check more about roles and permissions in the Security and Compliance Center.
7. Set Up Password Policy and Enable Two-Factor Verification
Strong authentication practices prevent your system from unauthorized access, like brute-force attacks, password stuffing, and account hijacking.
Weak authentication practices like the lack of a strong password policy and two-step verification make it a piece of cake for a hacker to penetrate your system and inject ransomware.
Weak password policy is the reason behind up to 81% of data breaches. Thus, we recommend you to create a strong password policy and ensure your employees understand and follow it.
Here are some of the main rules:
- Create a unique password for your work. It shouldn’t be the same as in your social media.
- Don’t make your password too short. It should include eight characters at least.
- Use various characters: upper- and lowercase letters, digits, and symbols.
- Never create too obvious passwords like 123456, qwerty, abcdef.
- Change your passwords regularly.
Two-factor verification (or 2FA) provides the second step of checking whether a user is authorized to enter. Ensure 2FA is installed and used to access data in your corporate network.
2FA may prove user identity in a number of different ways. For example, by generating a unique code by a special app like Google Authenticator. The code can be sent via a text message, email, etc.
2FA requires both email and mobile phone to get access to an account. Having the second check-in place dramatically decreases the risk of unauthorized access, and thus limits the ransomware attacks too.
8. Train Your Employees on ransomware protection strategies
In most cases, the end-user is the one that performs an action that triggers a ransomware attack. Security awareness training for your employees, although not being a panacea, can decrease the number of unaware or careless employees up to 90%, which drastically lowers their chances of clicking the wrong link.
Make sure that you have an easy-to-understand cybersecurity training conducted, and all the information is efficiently learned. Then, ensure that people know how to safely behave over the internet and within your internal IT infrastructure. Some testing (and rewards) will help too.
One of the best ways to educate your employees is by running a mock phishing attack. You can send out fake phishing emails and watch people clicking the links. After that, explain that in real life they might have caused a ransomware infection.
Don’t know where to look for the right cybersecurity training?
Here are the best security awareness training by rating.
And here is a list of phishing awareness training providers.
9. Use Third-Party Ransomware Protection Solutions
Leveraging specialized third-party ransomware protection solutions can provide an additional layer of defense. These tools often offer advanced threat detection, automated response capabilities, and continuous monitoring that go beyond standard security measures. They also offer features such as sandboxing, encryption, and behavior analysis, which can effectively block ransomware attacks before they cause damage.
One of the leaders on the ransomware protection solution market is SpinRDR. Specially designed to detect and respond to ransomware attacks in cloud environments, it can become a real game-changer in your battle against ransomware. Powered by artificial intelligence (AI) and machine learning (ML), SpinRDR offers the following capabilities:
Real-Time Ransomware Detection and Mitigation: SpinRDR continuously updates its threat databases with the latest known malicious URLs and blocks access to these sites in real-time. Thus, when a user tries to click a malicious link that can trigger ransomware infection, the tool automatically blocks it and warns the user.
Behavioral Analysis: AI and ML-powered behavioral analysis tracks user behavior and flags unusual activities, such as clicking on suspicious links, prompting further investigation, or blocking the action. If a user clicks on a link that initiates a ransomware attack, the analysis can detect unusual activities like rapid file encryption or unexpected data access.
Data Loss Prevention (DLP): by inspecting the content of emails and web traffic, SpinRDR can prevent users from interacting with potentially harmful files. Furthermore, DLP enforces strict access controls that prevent ransomware from spreading, even if a user clicks on a malicious link. For example, by restricting access to certain file types or directories, SpinRDR’s DLP can limit the ransomware’s ability to encrypt sensitive data.
In addition to functions that specifically work on preventing ransomware from clicked links, SpinDRD has the following useful features:
Automated Incident Response: Spin’s automated incident response can quarantine compromised accounts, revoke access permissions to ransomware processes, proactively restore affected data, and notify administrators immediately.
Data protection: SpinRDR offers incremental, versioned backups of SaaS data stored separately from the production environment. The data is encrypted both in transit and at rest. Administrators can swiftly restore or download data in the event of a security incident.
Compliance and Data Privacy: The SpinRDR supports compliance with regulatory standards such as GDPR, HIPAA, and CCPA. This compliance support ensures organizations meet their legal obligations while securing their SaaS environments.
Get a Free Demo to upgrade your ransomware defense strategy with SpinRDR!
Best Tool to Prevent Ransomware from Clicked Links
A third of organizations pinpoint email-based approaches as the primary cause of ransomware attacks (Figure 1). A well-known example is LockBit ransomware, which spreads in emails via the Phorpiex botnet. Ransomware delivery through phishing emails is generally caused by humans. No matter how good your cybersecurity training is on ransomware protection and phishing, human errors still happen. Therefore, reinforcing the human security link with automatized tools is always a good idea.
Root Causes of Ransomware Attacks
Figure 1 Root Causes of Ransomware Attacks, The State of Ransomware 2024 by Sophos.
One of the best tools to prevent ransomware from clicked links is SpinRDR. This security solution is designed to detect and respond to ransomware attacks in cloud environments, particularly within Google Workspace and Microsoft 365. SpinRDR can play a key role in preventing and mitigating the effects of ransomware, even if a user clicks on a malicious link.
Concluding Thoughts
Native cloud-provided data protection solutions are absolutely required for businesses to withstand and survive a ransomware attack effectively. However, even though backup is one of ransomware protection best practices, alone do not prevent the potential downtime that may result from a ransomware attack.
SpinOne’s ransomware protection and backups are absolutely priceless to businesses looking to back up their data and protect against ransomware attacks altogether. SpinOne saves companies from the manual recovery time needed to identify affected files and restore them. Instead, it blocks the ransomware quickly, identifies the affected files, and automatically restores them. It all makes SpinOne an excellent enterprise ransomware protection service.
By implementing the proactive, automated, and intelligent response provided by SpinOne, businesses can take the offensive against ransomware attacks instead of simply reacting to an attack and restoring data manually.
What is the first action to take against ransomware?
The first action to take against ransomware is to disconnect the infected system from the network immediately. This helps prevent the ransomware from spreading to other devices and systems. Once disconnected, you should then assess the extent of the infection, identify any compromised systems, and begin the process of containing and mitigating the threat.
Can antivirus detect ransomware?
Antivirus software can detect ransomware, but its effectiveness varies depending on the sophistication of the ransomware and the capabilities of the antivirus program. More advanced or novel ransomware strains might evade detection.
What is the most common way ransomware is spread?
The most common ransomware delivery vectors are:
- Phishing
- Malicious websites
- Exploiting vulnerabilities
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
How to Recover Deleted Messages from Microsoft Teams
In modern-day hybrid and remote work environments, collaboration and communication tools like Microsoft Teams are...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...


