Office 365 Security Best Practices for Ransomware Protection
Multiple businesses have suffered a successful ransomware attack in 2021 alone. In this article, we discuss Microsoft Office 365 security best practices to protect your cloud data from ransomware.
Ransomware Grows Smarter
As you probably know, ransomware is a type of malware that encrypts user files or files in the corporate network. Before taking a deeper dive into ransomware protection and recovery, we recommend you learn more about recent trends in ransomware.
Unfortunately for users of cloud services, ransomware strategies are evolving rapidly. Hackers apply more sophisticated smart social engineering tactics.
Here’s a quick summary of modern ransomware attacks:
- The goal of the attacker is to get a ransom for decrypting files (the ransom is usually paid in Bitcoin).
- Ransomware is not an on-premise problem anymore. Even the Office 365 cloud is vulnerable. Ransomcloud, the new type of ransomware, encrypts cloud emails (including Outlook emails).
- A usual way to get a ransomware infection is to click a phishing link and give permission to a risky app. Hackers gain control over your email after you click an infected link.
- Ransomware is well-disguised. It may look like an email from a trusted source like tech support, colleagues, well-known organizations.
- Attackers pressure you to pay the ransom by setting up a time limit for making a payment, or your files will be deleted.
- After you pay a ransom, your emails are restored to their original form.
How Dangerous is Ransomware?
Ransomware attacks the O365 cloud of individual users, small businesses, and enterprise companies. Corporate networks are especially hard to protect. A single click from one employee may be enough for a full-scale infection.
In 2018, there were more than 200 million ransomware attacks. Some ransomware attacks deal no damage, yet some are truly disastrous. For example, the estimated damage from WannaCry ransomware is up to $4 billion.
The cost of decrypting the affected data is growing. Сompared to the previous year, the average ransom demand has almost doubled in 2019, from $6,733 to $12,762.
End users and enterprises can be caught off guard and forced to pay the ransom. Does paying the ransom to save you from future ransomware infection? No. Trusting ransomware authors is not a game worth playing, especially when your data is on the line.
Ransomware is not unbeatable. There are measures to protect your data against ransomware and recover corrupted files.
Learn more about Office 365 ransomware.
Office 365 Security Best Practices for Ransomware Protection
The Office 365 security best practices against ransomware attacks are:
1. Teach your employees how to detect and avoid clicking suspicious links.
Microsoft Office 365 services are well protected against ransomware. That’s why cybercriminals exploit human error to infiltrate the O365 environment and target sensitive data with ransomware. They use phishing emails and other deceiving messages to get access to your Office 365.
Your employees will be your second line of defense against ransomware. We suggest using platforms like KnowBe4 to raise awareness in your company, train your teammates, and keep them alerted.
2. Backup Office 365 data
Backup is necessary when your second line of defense lets you down. Instead of paying a ransom, you can simply restore your data from a previously made copy. Tools like SpinOne enable you to make up to 3 automated backups per day and an unlimited amount of manual backups. Apart from ransomware use cases, this solution will be useful in case of data deletion or corruption and knowledge transfer.
3. Use application whitelisting
OAuth applications used by your employees gain access to your Office 365. As a result, they can use editing permission rights to infect your data with ransomware. Some of the Microsoft Office subscriptions enable Admins to create allow/block lists for applications. This will prevent unapproved risky programs from accessing your system.
4. Use anti-ransomware protection solutions
There are two main types of tools that help you fight ransomware:
- tools that use historical data on previous strains
- tools that analyze abnormal behavior in Office 365 – like SpinOne.
Advanced Office 365 Ransomware Protection and Recovery with SpinOne
SpinOne is an Office 365 ransomware protection tool that allows businesses to meet the challenge of ransomware head-on. We offer:
- Up to 2 hours downtime
- 24/7 security scanner
- Immediate termination of the attack
- Granular recovery of damaged data from our backup
- Safe data storage in Google Compute Storage, Amazon Web Services, or Azure clouds.
- In-flight and at-rest data encryption to keep your data safe in both transit and storage.
- Indefinite data retention.
- Weekly and monthly reports to monitor the status of your protected data
- Unlimited restore points to have a variety of versions to restore from.
- 100% accurate recovery using the same folders hierarchy from any point in time
- Email notifications and detailed reports in case of an attack.
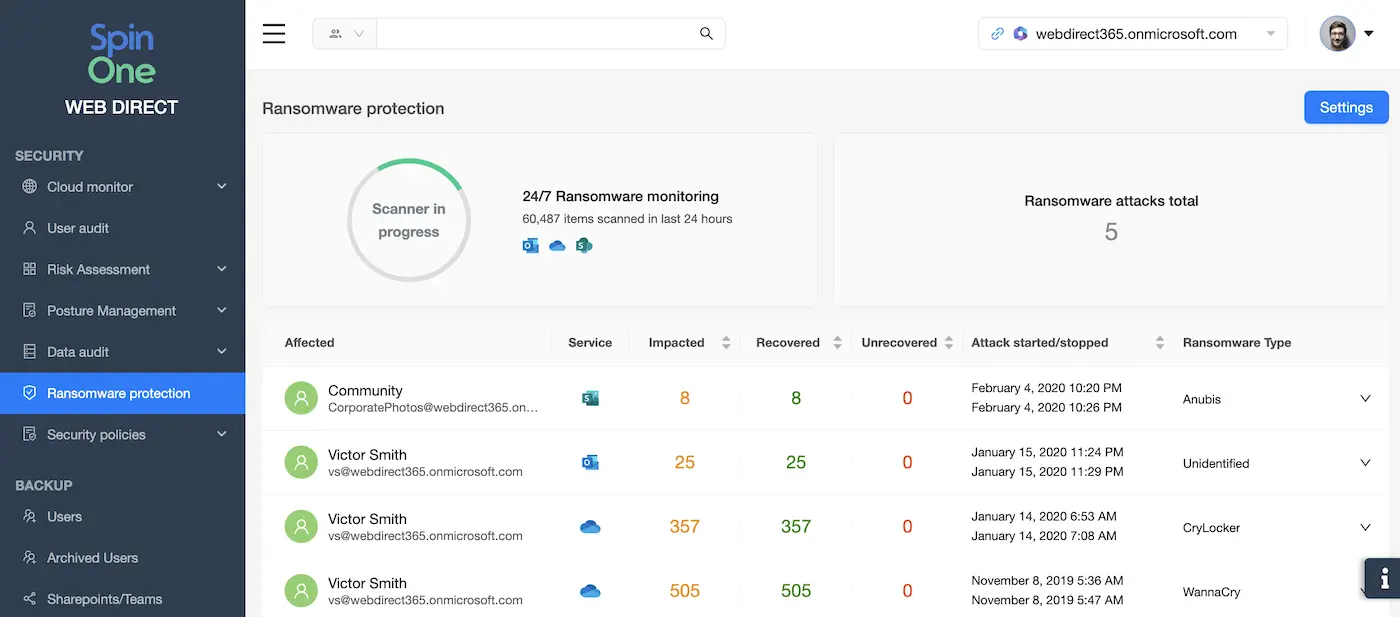
New ransomware detection interface
Are you looking for a reliable way to recover your data in case of a ransomware attack? We recommend Ransomware Protection for Office 365. With this cloud-to-cloud backup and ransomware solution, you’ll stop any ransomware attack and restore your Office 365 files in a few clicks. Try Sinbackup and don’t let ransomware put your organization at risk.
Office 365 Ransomware Recovery
When a ransomware attack happens, there are several actions to take. We recommend combining them to ensure nothing of value is lost.
Going Offline
After you have detected ransomware, immediately disconnect the infected device from the network (turn off Wi-Fi and unplug Internet cable). This will prevent ransomware from spreading through the network. Also, you should disable Onedrive sync and other sync services.
Recovery from OneDrive
You can protect OneDrive from ransomware with Microsoft native tools. To do this, log in to OneDrive from the non-infected device. Your task is to identify the infected file and restore its previous version. Select the file and click Version history (or More, then Version History, if you have a classic OneDrive view). After that, Restore the file.
This method has a significant drawback. Multiple files may be infected and restoring them manually takes an enormous amount of time. It’s not that hard to restore one file, but imagine restoring tens of thousands.
On-device Recovery
Security software installed on your device is likely to have some anti-ransomware tools. Have a full scan of your system. The infected files will be detected. By removing them, you’ll restore the system.
However, do not rely on your security software too much. Antivirus software may not detect new versions of malicious software. In other words, even a full scan may not recognize ransomware with 100% accuracy.
Recovery from Backup
Native OneDrive ransomware protection and recovery tools are not convenient if you need to restore many files. Antivirus software or firewalls don’t always protect your data from ransomware.
That’s why recovery from a backup is the best Office 365 ransomware protection practice. Backup is a safe copy of your files which means you get back your items even if they were encrypted with ransomware. To access your backed-up files, use a non-infected device.
SpinOne is a cloud-to-cloud tool for Office 365 ransomware protection. It allows you to recover Outlook and Onedrive files in their original form. You can choose the version you want to recover and SpinOne will get back your data immediately.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...