Insider Threat Software for Google Workspace™ Security
Not all security threats come from outside your organization. Employees are a leading cause of data breaches according to a report by Experian. In this report, over half the companies surveyed said they had suffered a security incident or data breach due to a malicious or negligent employee. That’s why insider threat software is becoming increasingly important.
Some employee security risks can be dealt with through staff training and the implementation of security policies; for example, ensuring all users on the system are educated in password security and follow the company’s BYOD policy. Moreover, it is important to plan a secure employee exit beforehand.
However, it is not sufficient to simply educate staff and hope that they follow the rules. In every organization, cases are likely to occur in which company policy is deliberately not followed.
This may be for malicious reasons (for example a disgruntled member of staff or a leaving employee, who wishes to take confidential corporate G Suite data with him or her), or for more innocuous reasons such as an employee wishing to download data to their own local device so they can work more easily out of the office.
Either way, it is vitally important for organizations that use cloud services to monitor their employee activity so that any suspicious behavior will be recognized immediately.
SpinOne Domain Audit as Abnormal Behavior Monitoring
The G Suite domain audit, which is part of the cybersecurity service of SpinOne for Business, provides an overview of all user actions in real-time and allows G Suite administrators to see the risk level of all activities at a glance.
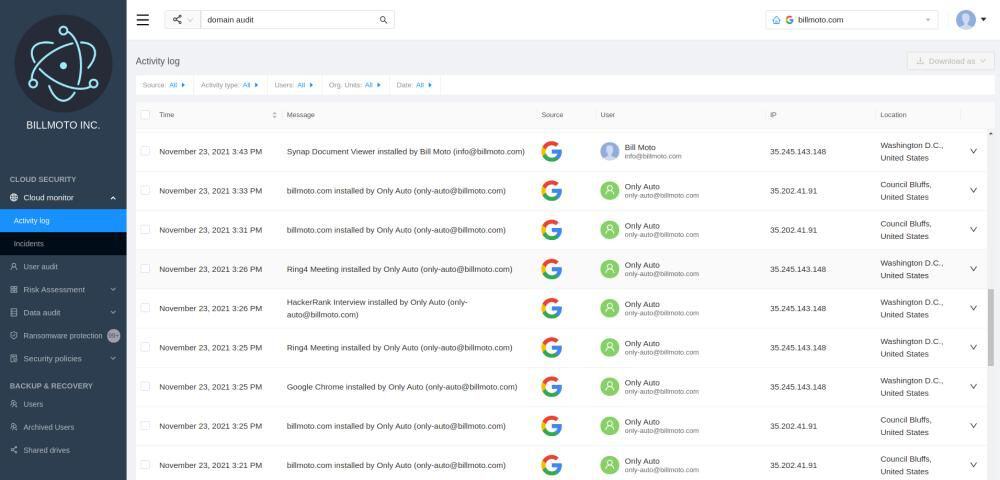
On the domain audit screen, G Suite administrators are able to view the following information for each user action as it occurs:
- Date and time of the action
- Color-coded risk level (high, medium, low or info)
- The user who initiated the action
- The type of action (login, transfer, download, data sharing, or authorization)
- The app associated with the action
- The IP address of the user
- The location of the user, including country and city.
A unique part of our cybersecurity solution – abnormal employee behavior analytics that can help you to detect the following security threats:
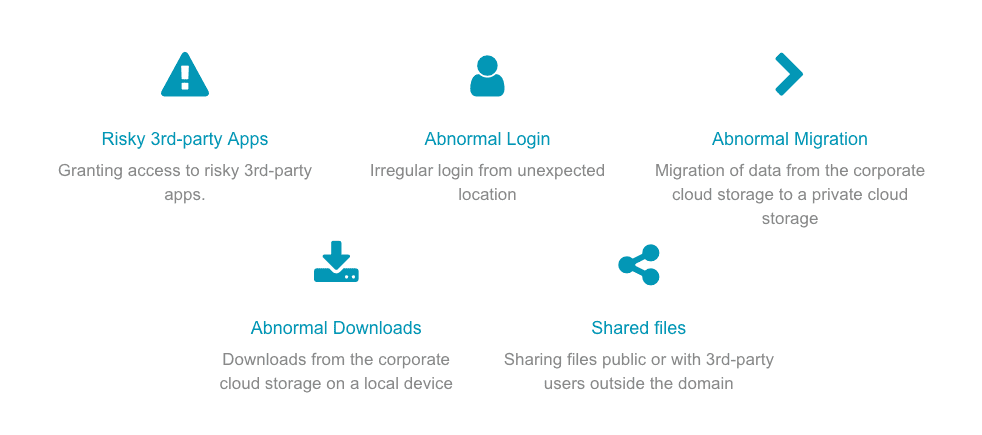
- Granting access to and control over risky third-party apps
- Irregular login from an unexpected location
- Migration of data from corporate cloud storage to private cloud storage
- Downloads from corporate cloud storage to a local device
- Sharing files publicly or with third-party users outside the domain.
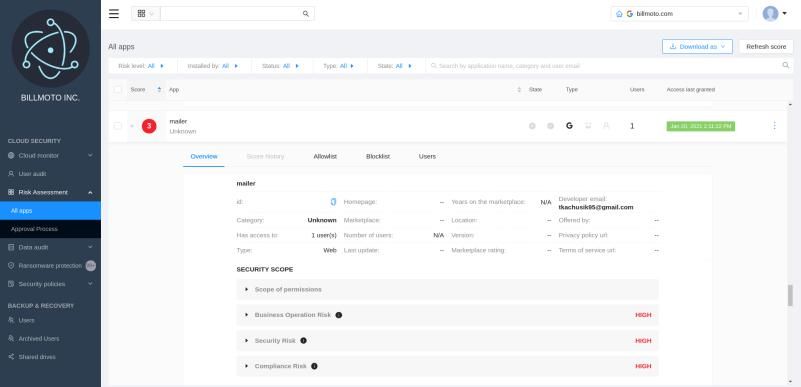
Clicking on the risk level you can access an audit of individual apps:
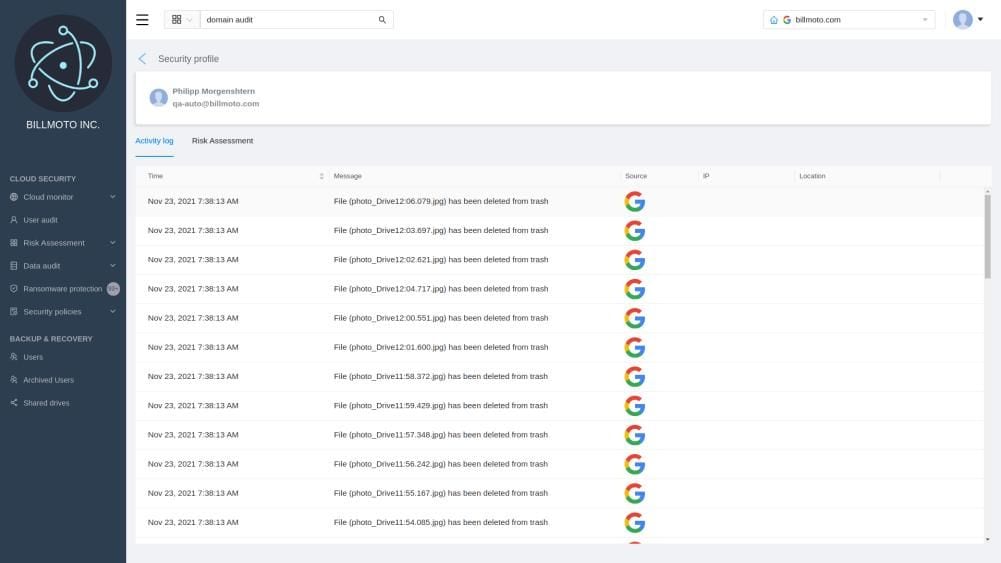
The G Suite admin can also choose to monitor the activity of individual employees. This screen lists all recent actions of the selected user, with the same information as on the main domain audit screen:
How SpinOne Insider Threat Software Can Enhance G Suite Security
SpinOne’s cloud cybersecurity service is unique as it provides data leak and loss prevention (DLP), all in one dashboard.
SpinOne (DLP) data loss prevention solutions for G Suite are designed to provide you with complete visibility of potential security breaches and business risks in your organization because visibility is the first step towards better G Suite security (don’t forget to check our G Suite security guide and find out about G Suite best backup practices and Google Apps backup).
The following are some examples of high-risk situations that could occur due to insecure employee actions, either maliciously or due to a lack of understanding about company data security. These examples illustrate how SpinOne can help to prevent these risks from becoming serious security problems:
- A departing employee transfers sensitive data from a corporate G Suite account to his private one at DropBox, SkyDrive, or another cloud storage service. SpinOne detects it and reports the transfer to a G Suite administrator and allows the admin to revoke access (most common case).
- An employee shares critical data with a third-party outside of your organization accidentally or on purpose. In this case, SpinOne provides a detailed map of all the items shared with the 3rd-party or shared on the Web to help administrators easily fix all security breaches in the company.
- An employee installs a new third-party app that has full account access to corporate data. SpinOne detects it and reports this to the administrator, allowing him to revoke access.
- An employee downloads an abnormal number of files to his local device. Once SpinOne detects this, a G Suite administrator will be notified about it instantly.
- A criminal from outside the organization has managed to obtain the login credentials of an employee and is logging in remotely in order to access confidential corporate data. The login history and activity allow administrators to detect any suspicious logins from unfamiliar locations and revoke access if necessary.
You can receive automatic notifications of any actions by email and/or Slack, based on the level of risk you choose to trigger an alert (high risk only, medium and high risk, or all levels of risk).
It is also possible to set SpinOne to automatically revoke access to a risky app that has access to corporate data.
With this multi-pronged approach, SpinOne is highly effective at preventing data leak disasters in a company of any size.
Here at SpinOne, we are looking forward to working with you to ensure the safety of your business in this field. You can rest assured that the cybersecurity of our clients is our top concern.
Check out the cloud security expertise that SpinOne API-based CASB brings to the table!









