How Banks Can Enhance Security of Office 365 and Google Workspace
The move to the cloud has been somewhat of a foregone conclusion among most businesses today. The services and products that are offered by public cloud vendors often provide solutions that would otherwise be financially or technically unattainable by businesses building out similar infrastructure on-premises. Public cloud has tremendous advantages for many business use cases. Various industries are taking advantage of the public cloud to host many different business-critical services such as email and file storage. However, there are other services housed in public clouds today that can enhance business productivity and collaboration.
Security has always been a hot topic among those utilizing the public cloud and has arguably been the most debated topic since public cloud environments came onto the scene just a few years ago. Especially for business sectors that by default demand an ultra-secure posture such as banks and financial institutions, security in the public cloud is certainly a topic for concern. Banks and financial institutions have been very slow to adopt cloud technology and service offerings either in the public cloud or via hybrid cloud offerings.
However, there are trends in the customer base as well as banking directives that are dramatically changing the landscape for today’s financial institutions. Especially with financial organizations, security needs to be first and foremost. How can today’s financial institutions keep pace with today’s business demands and still maintain an ultra-secure security stance?
Key Factors Driving Migration of Banks and Financial Institutions to the Cloud
There are many cloud migration factors in today’s business and customer landscape that are the driving force behind today’s financial institutions deciding to embrace cloud as a major part of their infrastructure. The culture of today’s online banking customer and access activity has drastically changed from what has been seen in year’s past. The modern era of mobile devices and “always on” access and activity has driven a change in the way businesses architect infrastructure and allow customers to access data. This has also affected the banking world.
The business challenge to be able to service an unknown number of mobile customers who are accessing and querying an unknown amount of data can be challenging to scale when building out on-premises infrastructure. Cloud computing and resources provided by today’s public cloud vendors such as Amazon, Microsoft, and Google allow organizations to build out infrastructure quickly and have the ability to scale the infrastructure as needed. These powerful cloud environments allow businesses to have “elastic” infrastructure, meaning the infrastructure needs can easily be expanded and compressed as needed. This type of expanding and compressing of on-premises resources is simply not feasible or cost-effective.
In the EU, a plethora of new regulatory guidelines are changing the ownership of data and empowering customers to have much more control on their data and data privacy. The perhaps now well-known General Data Protection Regulation or GDPR empowers customers to own their data and have the ability to demand total erasure of personal data from organizations infrastructure that have handled or stored customer data. There is another new EU regulation that is a bit lesser known since it directly pertains to customers financial data and their ability to have other payment services.
The new PSD2 directive, or the Second Payment Services Directive as it is known, went into effect in 2018. What is the PSD2 directive? The PSD2 directive essentially requires today’s banks and financial institutions to support customers being able to share financial data with a third-party payment provider of their choosing. This is a much more customer focused directive that requires banks and financial institutions to have the infrastructure and technical connectivity to their systems that allows collaboration with these third-party entities. To enable connectivity, banks and financial institutions must provide the APIs or Application Program Interface that allows querying and connecting to customer data effectively and efficiently.
Building out the infrastructure to facilitate the technical requirements and connectivity on-premises can be challenging and problematic for financial institutions. However, by shifting infrastructure into the cloud, public cloud providers already have frameworks and technical requirements in place that can alleviate the need for financial institutions to build this infrastructure from the ground up and “reinvent the wheel”. The various cloud offerings from Software-as-a-Service to Platform-as-a-Service (SaaS and PaaS respectively) provide tremendously powerful offerings on which today’s banks and financial institutions can build out flexible, scalable, and extremely agile infrastructure.
Cloud security has certainly been one of the major deterrents to cloud adoption across the board. This is certainly even more concerning for financial institutions who have to meet much more stringent compliance regulations in general than typical business entities. In recent years however, public cloud vendors and cloud offerings in general have greatly improved and tightened down security. The focus on security by the major vendors has certainly helped in facilitating the adoption of cloud technologies by banks and financial institutions.
With the above-mentioned reasons for cloud adoption including customer demand for rapidly moving technologies, compliance regulations such as PSD2, and new security-focused offerings from cloud vendors, financial institutions are making the move to cloud platforms for both customer-facing technologies as well as the hosting of internal business-critical resources. Despite the driving reasons mentioned above, what are the major challenges that remain to cloud migration for financial institutions looking to leverage the power of the cloud for both customer-facing and internal business-critical resources?
Challenges to Cloud Migration for Banks and Financial Institutions
Even though there are great reasons for businesses today to migrate to the cloud, including financial institutions, there are certainly still challenges to doing so. When focusing in on financial institutions what challenges are presented when thinking about migrating to cloud for both customer-facing and internal business-critical resources. What are some of these challenges?
- Compliance Regulations
- Security and specifically data leak
- Data locality
- Migration complexity
Compliance Regulations
Even though financial institutions have really good reasons to consider public cloud resources including customer demands and PSD2 (Revised Payment Services Directive) initiatives, there are still very stringent compliance and regulatory concerns for financial institutions. Finance is one of the most regulated industries and face severe fines when in violation of regulatory.
There have been several studies and findings published that have warned financial institutions about the dangers to data security when considering utilizing the cloud for hosting data and services. Even though cloud has been accepted as perhaps the most viable means of infrastructure for businesses moving forward, there is still somewhat of a stigma attached to cloud from more traditional infrastructure viewpoints. Perhaps the majority of the concern from regulatory compliance and those reviewing and considering cloud infrastructure involves security and the protection of data.
Banks and Financial institutions are subject to the PCI-DSS compliance regulatory requirements. PCI-DSS is the Payment Card Industry Data Security Standard and is a set of security standards designed to ensure that any organization that accepts, processes, stores, or transmits credit card information maintain a secure environment. The Payment Card Industry Security Standards Council (PCI SSC) was launched on September 7, 2006 and its sole purpose is to manage the evolution of the payment card industry and the security standards involved.
PCI-DSS places very strict and often very complex requirements on financial institutions such as banks and the requirements for handling any credit card data and the security involved with doing so. This is certainly to the benefit of the customers and their data. It does however, mean that financial institutions that are looking to migrate systems, services, or any other infrastructure into the public cloud, have to take into consideration the requirements that are placed upon them from a PCI-DSS standpoint.
Another compliance regulation that is fairly late-breaking is the new General Data Protection Regulation or GDPR compliance regulation that affects organizations doing business in or with the European Union. Financial institutions process a vast amount of personal data for customers on a daily basis. A large quantity of this information is confidential and sensitive. This means financial institutions are certainly under close scrutiny with GDPR objectives. With GDPR regulations customers have renewed ownership of their data with security being a prime focus. Infrastructure systems must have “security by design” and be architected in such a way that data security is thought of up front. Customers can also request total “erasure” of their personal information.
Any customer-facing or business-critical internal services and data that are housed in the cloud must have the processes and technology in place to be able to meet up with GDPR objectives. This includes such critical capabilities as backing up mission critical data, controlling data locality of both production and backup data.
Security and Data Leak
Security and specifically data leak are tremendously concerning for financial institutions. Financial data is perhaps one of the most sensitive types of data. Often, the target of attackers can be financial information or other information that can compromise identity. This can lead to financial services being compromised.
It seems as if every few days or weeks, we hear of financial data such as credit card information and identities being compromised from organizations with an online presence. Attackers are certainly looking for vulnerable financial data that may be accessible via loose security standards implemented, known vulnerabilities in the infrastructure being used, overly permissive account permissions that may be compromised, or any other flaw in the security that can allow information to be siphoned from the system gradually or in bulk.
One of the worst data breaches in history happened in 2017 with the Equifax data breach. Due to a flaw in a tool that was designed to build web applications called Apache Struts, hackers were able to gain access to some 143 million Equifax customers and their data. The data compromised included Social Security numbers, birth dates, addresses, and drivers license information. Even though Equifax knew about the vulnerability some two months before attackers were able to exploit it, corrective action was not properly taken and thus we see the tremendous fallout from one of the worst data breaches in history.
When thinking about housing customer-facing infrastructure in the cloud or if placing internal business-critical systems in public cloud infrastructure, financial organizations must treat security with utmost importance in the building out of infrastructure and designing secure data systems that house financial data. Any customer-facing or internal business-critical system that is used by financial institutions must have the controls and processes in place that allow meeting PCI-DSS objectives and ensuring systems are protected from data leak.
Data Locality
As mentioned earlier in the compliance regulation section, data locality is another topic of thought/concern among those housing data in the cloud. With today’s complex regulations such as GDPR or General Data Protection Regulation specifying regulations regarding data locality, etc, organizations must be conscious of the locality of their data. This can certainly include the location of data backups. Organizations must ensure that data is housed in a way and location that complies with regulations specifying where data needs to be located and how it needs to be stored in line with security and other regulatory compliance regulations.
Migration Complexity
There is certain a barrier of entry with moving to cloud environment due to the complexity of the process. There are generally many moving parts to complex IT infrastructure, especially those dealing with financial systems. When thinking about challenges for financial institutions in migrating and utilizing cloud environments effectively, securely, and in a way that data is both protected and secure, migration complexity can be a primary challenge.
Additionally, organizations want to think very seriously about how the migration process is planned, staged, and even executed. If any part of the process is flawed, this can leave data vulnerable, unprotected, and open to exploitation or data loss. The moment data leaves the boundaries of the on-premises environment, it is vulnerable if not protected during transmission and once the data arrives at the destination storage.
Financial organizations want to ensure that all considerations in regards to compliance and other regulatory obligations are fully satisfied when migrating data and services to cloud environments. This can also be part of the challenge as there needs to be individuals involved with the needed expertise in handling the requirements in a way that meets regulation and satisfies the needs of the business, ensuring security and data protection is of primary concern.
What Can Help Financial Institutions Meet the Demands of Cloud Migration?
Financial organizations including banks certainly have a long list of objectives to consider and include as part of any migration initiative to the cloud. Any migration initiative needs to be fully thought through and considered at length by all stakeholders to ensure all the details and aspects of the migration, compliance, security, network, storage, and cloud are fully considered. Aside from the proper planning, staging, testing, and other aspects involved in the testing phase with a successful migration, financial organizations can make use of technology solutions to bolster security and compliance requirements of migrating to cloud environments.
SpinOne provides a powerful API-based Cloud Access Security Broker (CASB) solution for both Google Workspace and Office 365 environments that provides financial organizations with the technology needed to ensure a secure and compliance environment with the strict guidelines and regulatory guidelines imposed upon them including:
- Data locality for backup storage
- Automated Daily Backups
- Sensitive Data Protection
- Insider Threat Detection
- Risky Third-party Apps Control
- Cloud Ransomware Protection
- Machine Learning-powered Cyber Threat Intelligence
One of the first things you notice with SpinOne when configuring the account for storing data backups is the ability to choose both the public cloud provider who backs the “backup” storage as well as the location for the storage.
Configuring data locality with SpinOne data storage used with automatic backups
When you think about compliance and other cloud considerations, data locality certain comes into the picture. Other cloud data protection solutions on the market do not provide the ability to choose where data backups are stored which may result in compliance or other violations. SpinOne follows the mantra that the organization should have control of its own data and where that data is housed. SpinOne simply provides the vehicle and technology to get it there.
A tremendously important aspect for financial organizations to consider is ensuring that proper data protection is in place for data that is migrated to the public cloud environment and making sure the data is protected by in-flight and at-rest.
SpinOne provides automated daily backups:
- Frequency of 1X to 3X daily.
- Backups are encrypted in-flight and at-rest with AES 256-bit encryption.
- Provides versioned multiple restore points in time backups.
- Data storage locality ensures that organizations can meet up with GDPR objectives.
- Data retention can be controlled to include indefinite storage along with specific data storage and backups pruning.
Backups are an absolutely business-critical process that must be carried out for organizations housing data in the cloud. SpinOne allows businesses including financial organizations to effectively meet the need to perform backups of data that allow multiple restore points and effective versioning, transmitted and stored securely, via industry-standard encryption.
Financial institutions including banks maintain and store some of the most sensitive customer data of any other sector. Making sure to have control over the sensitive data that is stored, transmitted, and potentially shared in the cloud. Having control over sensitive data can help to ensure that ultra-sensitive information such as Credit Card Numbers are not inadvertently transmitted or accidentally shared outside the cloud environment which could be disastrous and certainly is a PCI-DSS issue.
SpinOne provides a powerful and robust Sensitive Data Control module that allows organizations to prevent leaking of sensitive data such as Credit Card Numbers outside the cloud environment. The Sensitive Data Control module allows effectively preventing credit card numbers from leaking outside the bounds of the organization. This includes emailing credit card numbers or storing credit card numbers in cloud storage.
Organizations can create their own sensitive data detection rules for other types of data and strings that match patterns that are deemed sensitive. Having this ability allows organizations to effectively control leaking of sensitive types of data such as credit card numbers and prevent this type of information from being intentionally or accidentally transmitted.
Not only does SpinOne contain these types of events, administrators are also properly and quickly alerted to various security events that are noteworthy, such as sensitive data detection/transmit attempts This allows administrators to be effectively proactive in their efforts to combat security and other data related events.
The SpinOne Data Audit allows quickly seeing Messages with CCNs detected
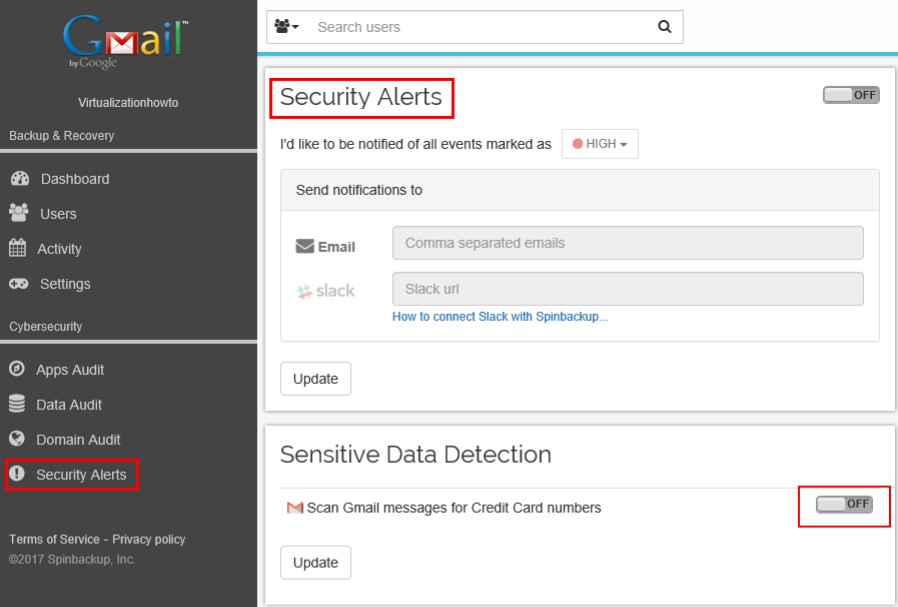
The Sensitive Data Detection can be flagged on for finding messages with Credit Card numbers
Domain Audit can quickly show Credit Card information that has been detected in the environment
What if organizations have an unscrupulous employee? What if an employee user account has been compromised by a phishing attack or some other credential harvesting mechanism? SpinOne’s Insider Threat Detection is a great way that organizations can key in on anomalous behavior that may indicate an employee is not acting appropriately or the account is compromised. Especially related to financial institutions, sensitive data may abound in internal systems. If public cloud storage is being utilized for storing business-critical information, you want to effectively be able to monitor and know if that data is being downloaded to local storage inappropriately, or perhaps a user account is being logged into from a totally anomalous location or there may be many failed login attempts
SpinOne’s Insider Threat Detection module gives visibility to all these types of scenarios by closely monitoring the environment and notifying administrators when events are detected that match anomalous behavior. Additionally, SpinOne can stop the process of data being downloaded inappropriately and notify administrators
What about users who have access to financial data stored I the public cloud that also have mobile access on various devices? There can potentially be security risks with applications installed on mobile devices that request permissions be granted to storage and other device-level systems. Unknowingly, employees could be granting access to a malicious or unscrupulous third-party app that may now have access to sensitive data stored in the cloud.
SpinOne once again gives visibility to which apps have access to cloud resources by constantly monitoring the environment and alerting administrators to resources that are shared both inside and outside the organization. Under the Data Audit module, you can effectively and quickly see these resources
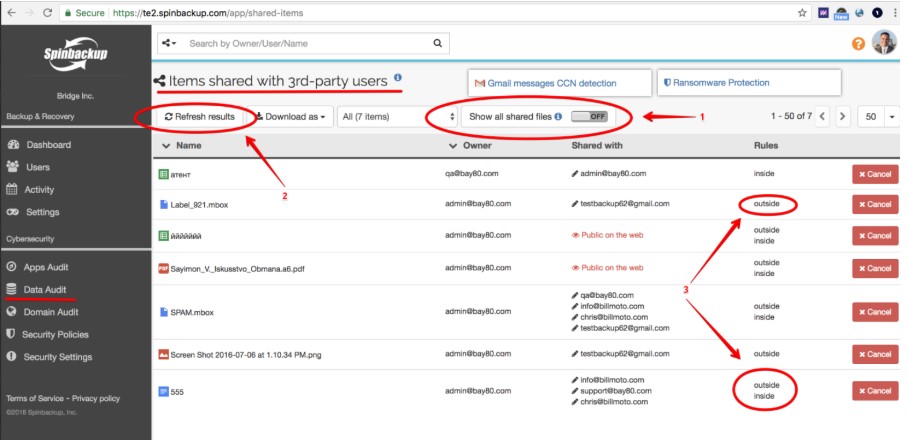
Items shared with third-party users
Administrators can also effectively revoke access from third-party applications and create black-lists of applications that are not allowed for access to the environment. Once again, for financial organizations looking to have complete visibility and control over data that is stored, access to it, and alerting for data that is shared, SpinOne provides a powerful way to do this.
What about Ransomware? Ransomware is one of the most formidable enemies to organization data among the many threats present today. Ransomware slyly and inconspicuously encrypts business-critical data using an encryption key held onto by the attacker. Unless payment is given, the data becomes useless. Once the demanded “ransom” is paid, the attacker releases the key that allows unlocking encrypted data.
With often up to the second critical transactions and business-critical processes that rely on always being able to access data needed, financial organizations can’t afford to have data interrupted by ransomware infection. SpinOne provides arguably the most powerful ransomware protection on the market by providing a machine-learning enabled ransomware detection algorithm that monitors the environment for any potential encryption processes. If ransomware infection is detected, the process is automatically blocked and any initial file encryption that may have taken place is automatically reverted using the latest backup point-in-time! Administrators are alerted to the activity and remediation as well.
We have mentioned and touched on “machine-learning” enabled abilities that are utilized by SpinOne. SpinOne is powered by powerful “intelligent” algorithms that have the ability to “learn” and detect anomalies in the baseline of a healthy and uncompromised cloud environment. Any behavior or activity that falls outside of this “baseline” can be scrutinized further by SpinOne’s threat engine. By using this powerful learning and detection intelligence, financial institutions have access to an “always on”, intelligent, guardian of business-critical data and security.
Concluding Thoughts
Financial institutions including banks and others and others that deal with financial transactions, are perhaps some of the most heavily scrutinized and regulated industries out there. Migrating to cloud holds tremendous advantages for businesses today including financial institutions that have to satisfy the growing demands of their customers. Customers of financial institutions including banks want access to their accounts and other account related information 24x7x365 and expect no downtime to those systems. Additionally, directives such as the PSD2 directive (Second Payment Services) require that financial institutions build infrastructure that allows effective programmatic interfaces by third-party payment services. Building out infrastructure in the public cloud today is a smart move that can allow financial organizations to meet all of these demands both logical and technical.
Public cloud infrastructure including servers, storage, and other services allows businesses to be agile, move quickly, and build services on top of world class datacenters that would be impossible to rival using on-premises solutions. However, with the great benefits and technical solutions these provide to meet customer demands and new payment directives, there are certainly challenges from a compliance and security perspective as well as others. For those organizations who decide to make the migration to the cloud, SpinOne can provide the tools needed to both protect and secure data resources. SpinOne provides powerful machine-learning enabled capabilities that allow backing up data, sensitive data control, insider threats detection, third-party apps control, and ransomware detection, all in a single solution that provides global visibility to data protection and security.
SpinOne can effectively allow financial organizations to make the move to cloud and protecting while at the same time, protecting and securing data that is housed there. This allows those financial institutions to still meet the demands of today’s compliance and security stipulations, while at the same time, meeting customer demands and payment directives.
Discover How to Choose the Best Office 365 Backup Solution!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

