Recovery Time Actual in Cloud Office Suites: What SMBs Do Not Expect
Companies that have disaster recovery strategies use a Recovery Time Objective to identify the downtime in case of a cyber event. However, when the incident strikes, the real downtime takes much longer. This article discusses Recovery Time Actual and the reasons why it often comes as an unpleasant surprise.
What is Recovery Time Actual?
Recovery Time Actual is an important indicator in the disaster recovery process that quantifies the amount of time the business has spent to recover from a certain cybersecurity incident.
RTA varies depending on multiple factors, including:
- the severity of an incident,
- the availability of an Incident Response Plan,
- the time when the cyber event happened
- the resources the company has for the recovery (team, money, time).
The goal of any IT team is to minimize the Recovery Time Actual and make it less than Recovery Time Objective.
Recovery Time Actual vs. Recovery Time Objective
Recovery Time Actual shouldn’t be confused with Recovery Time Objective. RTO indicates how much time the company wants to spend on recovery from a certain incident.
RTO is a hard compromise between the capabilities of a business to withstand downtime and the available resources to respond adequately to a given cyber incident. Cyber events differ in magnitude and manageability from minor (e.g., a lost file) to major (e.g., a ransomware attack). Predicting how much time the company will spend on recovery is hard. That’s why RTO is seldom correct. As a result, businesses have to face an unexpected extension of their downtime, impacting their operations.
Both Recovery Time Objective and Recovery Time Actual are critical to small businesses. These companies often lack the necessary resources to both withstand downtime and respond to the incident.
Why do businesses fail to meet their Recovery Time Objective in the Cloud?
We’ve seen many companies incorrectly determining the Recovery Time Objective in cloud office suites like Google Workspace and Microsoft 365. One of the major reasons for this is the failure to take the API into account.
Many businesses rely on data recovery from backups in case of major events like ransomware encryption. Ransomware causes the loss of entire cloud data dwelling in your cloud office suites since these environments are well protected against most other incidents of a similar magnitude (e.g., hardware failure). Paying ransom for many businesses isn’t an option and, in most cases, doesn’t guarantee the full recovery of data. There are also strains that wipe all the files rather than just encrypt them.
Unfortunately, when companies start recovering from backup, they come across API calls limitations. These limitations restrict the speed of data upload from the backup significantly and expand the RTA significantly.
Related Link: Five Steps to Protect Your Clients’ Data From Ransomware Attacks
How to reduce Recovery Time Actual in the cloud?
Let’s discuss what businesses can do to ease the recovery issues that occur in cases of major data loss.
- Use ransomware protection
We suggest looking at tools that use data-behavior-based ransomware detection and are able to spot and stop ransomware within minutes after the attack. SpinOne ransomware protection is a unique tool that reduces ransomware-related downtime by 99.9%.
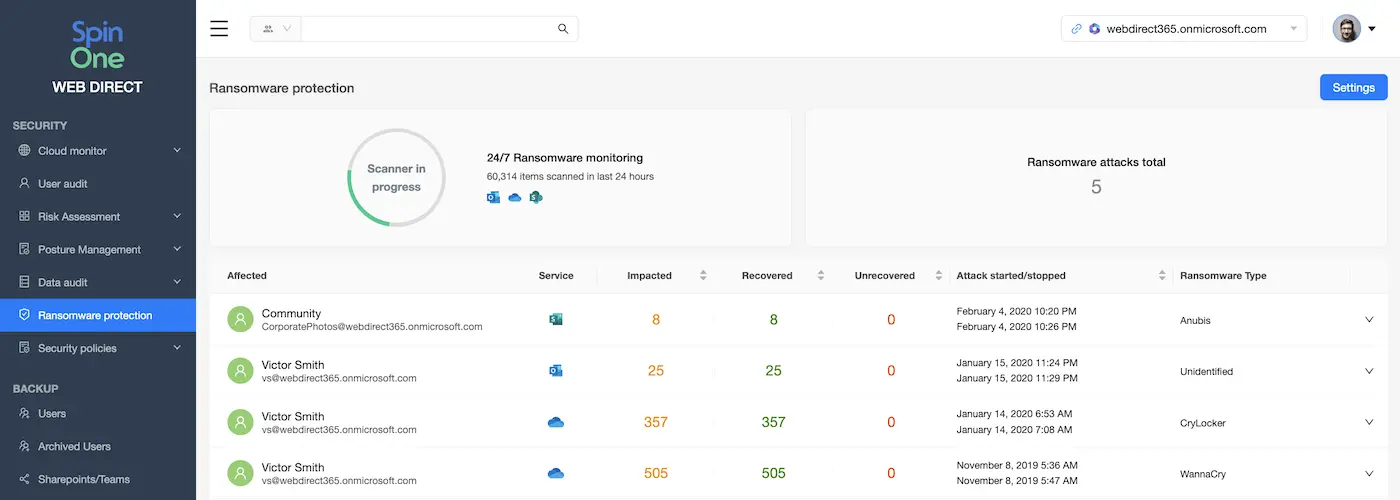
- Apply the 3-2-1 rule
Do not store all your backed-up data in one place. Diversify! Have the files’ copies in cloud backup tools and store them on-prem. In this case, you will be able to provide your employees with the data to work with while your IT team is taking time for a proper response.
- Get a cloud-to-cloud backup with a local download
Local downloads can get your data on your on-prem device quicker than on the cloud. You will be able to hand this data to your employees so that they can continue working.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthenin...
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthening Your SaaS Security From November 2023...
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...


