SaaS Data Loss Prevention: Compliance & Security Guide
As easy as the Internet, modern networking technologies and cloud SaaS environments make it to transmit, collaborate, and communicate data, they also make it easy to do something else – lose it. Data loss due to many reasons can cost an organization dearly. For example, companies can lose data by having it communicated or shared in a way that “leaks” data, exposing sensitive information unexpectedly. SaaS Data loss prevention (for instance Google Workspace DLP) is a critical facet of the cybersecurity strategy in the cloud SaaS environment. Having the security controls to prevent data loss due to leaks or inappropriate sharing is necessary to maintaining and achieving compliance. So how can organizations implement SaaS DLP for achieving compliance and maintaining their security posture?
How can data loss happen in cloud SaaS?
Let’s focus for a moment on how data loss can result in cloud SaaS environments. Data is now the most critical resource that must constantly be accessible to customers, end-users, and others. Unfortunately, unavailable data or data loss for reasons such as data corruption, system downtime, or other IT infrastructure issues violates many compliance frameworks, including HIPAA, ISO 27001, PCI-DSS, GDPR, SOC 2, NIST, and others.

The primary reasons for data loss in cloud SaaS environments come from:
- Human error
- Ransomware or other malicious threats
Human error in SaaS environments
Most IT teams will agree that accidental data deletions by a user are by far the most common culprit for data loss. For example, users may accidentally delete the wrong file. Or, they may update the wrong file and forget to “Save As” instead of “Save.” These types of human error accidents can be simple and common. However, they can cause significant business continuity disruptions.
The primary protection against data loss is backups. Backing up your data is the most basic and important way you can protect your data from loss. If data is lost, it can be recovered using good copies of the data contained in the backups. In addition, backups can totally recreate data without any dependencies on production infrastructure.
Organizations can mistakenly assume data loss is not possible in cloud SaaS environments. However, there are no native backup solutions that exist in either Google Workspace or Microsoft 365. The same types of end-user mistakes that have been made for years in on-premises environments equally apply to cloud SaaS environments. Without third-party backup solutions, businesses open themselves up for the risk of major data loss in their cloud SaaS environment.
SaaS Ransomware or other malicious threats
The other primary culprit of data loss is ransomware and other malicious threats. According to Cybersecurity Ventures, ransomware will attack businesses every 11 seconds in 2021. Unfortunately, due to the fact it is incredibly effective, ransomware is only going to get worse. Ransomware can destroy massive amounts of data in a relatively short time, even in cloud SaaS environments.
Kevin Mitnick demonstrated an attack he coined as a “Ransomcloud attack” where a malicious attachment masquerades as a legitimate application and then encrypts cloud email. Once users grant permissions to the malicious cloud application, the application begins encrypting the user’s mailbox in real-time.
Due to the ease of installing cloud SaaS applications by default, organizations are at risk for data loss of critical and sensitive data at the hands of ransomware. In many cases, attackers can easily trick end-users into granting the OAuth authorization for a malicious application by making it look legitimate. Most users do not scrutinize permissions requests of cloud applications as most of us are conditioned to grant requested permissions when using similar technologies such as smartphones. As shown in the major ransomware attack of Colonial Pipeline, the damage can be catastrophic and costly.
What is SaaS Data Loss Prevention (DLP) and why is it important?
Data loss prevention represents the set of tools and processes that ensure business-critical and sensitive data is not lost, leaked, misused, or compromised. It also puts the protections in place to ensure unauthorized individuals cannot access it. So really, it encompasses protecting against two primary risks to sensitive or critical data – loss and leaks.
DLP is massively important today for several reasons. Organizations who do not give the needed attention to DLP open themselves up to the potential for lawsuits, including ones whose data was exposed by a data loss or leak event.
Aside from lawsuits from individuals, there can be penalties from regulatory agencies. For example, fines from the General Data Protection Regulation (GDPR) are significant if a company is grossly negligent. GDPR penalties, in this case, can amount to 4% of the global turnover or €20 million, whichever is higher.
Finally, there is the loss of your business reputation, which can bring untold repercussions for the fiscal bottom line of an organization. Lost customer confidence and damaged business reputation can take years to recover if it is even possible.
Due to the stringent compliance requirements today, organizations must prioritize data loss prevention strategies as part of their overall data recovery and cybersecurity initiatives.
Data leak prevention
Data leak prevention is a component of DLP that protects your data from leaks, resulting in sensitive information being accessible by unauthorized individuals. How can business-critical or sensitive information be leaked outside a cloud SaaS environment? Notice the following:
- Leaky third-party applications
- Data shared outside the organization
- Personally Identifiable Information (PII)
- Insider threats
Leaky third-party applications
One of the powerful features of cloud SaaS environments, including Google Workspace and Microsoft 365, is the accessibility to third-party applications. Both cloud service providers offer access to thousands of third-party applications that extend the native functionality of Google Workspace and Microsoft 365.
While these applications can provide many benefits to the capabilities offered in cloud SaaS environments, they also lead to an increased risk of data leaks. How so? All third-party applications available in the cloud SaaS marketplace are not created equally from a security standpoint. While the developers of one application may have developed the app with security in mind, the developers of other applications may have had laxer security standards in their application code.
Specific cloud SaaS applications may not securely store sensitive data. For example, data may be encrypted at rest but not in-flight, or vice versa. Also, certain applications may violate data locality concerns when interacting with cloud SaaS information, breaking compliance regulations. Finally, cloud SaaS applications may not use proper security controls to ensure only authorized individuals can access the data held by the application.
Data shared outside the organization
Aside from third-party applications, data can be exposed and leaked due to improper data sharing. By default, like installing third-party applications, cloud SaaS environments make it easy to share data. While this eases communication and collaboration, it can also pose grave risks to data leaks.
If an end-user shares sensitive information with someone outside the organization improperly, data is openly exposed and accessible by an unauthorized individual. Businesses must have visibility to and controls over how data is shared and with whom to meet compliance regulations.
Personally identifiable information (PII)
In today’s compliance world, Personally Identifiable Information (PII) data is essentially any personal details about an individual. For example, it can include their name, address, age, sex, telephone number, religion, or any number of other personal details. Tying into the abovementioned points, organizations must have tight controls over sensitive information, how it is accessed, shared, and integrated applications.
Insider threats
All too often, companies focus on the threats from the outside and neglect threats that exist on the inside. For example, unscrupulous employees or compromised user accounts can wreak havoc on the security and compliance of your data. Therefore, organizations need to have solutions to analyze behaviors and user activities to spot abnormal activities easily.
These activities may include abnormal downloads of data (from business cloud to personal desktop or personal cloud locations), transferring data to and from outside or personal locations, abnormal file deletions, attempts to access unauthorized resources, and other types of activities. Additionally, brute force attempts or abnormal logins from strange geographic regions may indicate attempts to compromise accounts or a currently compromised account.
Compliance regulations require organizations have cybersecurity protections and governance solutions to prevent compromised accounts and other cybersecurity breaches.
Effective Cloud SaaS DLP
Controlling data in cloud SaaS environments is becoming increasingly challenging. As organizations make greater use of cloud SaaS data locations and services, they must have the visibility and controls in place to govern data access and security. Unfortunately, native DLP solutions often fall short in features and seamless integration across cloud SaaS services.
SpinOne’s SaaS Security Posture Management (SSPM) tool provides the Data Loss Prevention (DLP) features needed to meet the challenges of data loss and data leak in modern cloud SaaS environments. Note the features of SpinOne data protection via cloud SaaS backups:
- Automatic backups multiple times per day
- Ability to store backups across numerous cloud storage locations
- Encrypted backups in-flight and at-rest
- 100% recoverability of your data
- Protected from ransomware and other attacks
SpinOne SaaS Security Capabilities for SaaS Data Loss Prevention
SpinOne also provides the needed protection against data leaks due to lack of visibility and control due to third-party applications, data sharing, insider threats, and other abnormal behaviors. It provides:
- Artificial Intelligence (AI) powered cloud ransomware detection – SpinOne provides proactive ransomware detection and remediation to stop a ransomware attack before it becomes a significant data loss event, affecting RTOs and hitting cloud API throttling when trying to recover
- Protection against risky third-party applications via automated app scoring – SpinOne provides automatic, AI-powered risk assessments of third-party cloud SaaS applications.
- 24x7x365 automated monitoring – Around the clock monitoring of all cloud events
- Alerts and analytics – Receive proactive alerts on cybersecurity events and analyze and produce compliance reports quickly and easily.
- Insider threats protection – Spot abnormal behavior from an end-user account quickly
- Domain security policies – Apply automated security policies to your cloud SaaS domain level
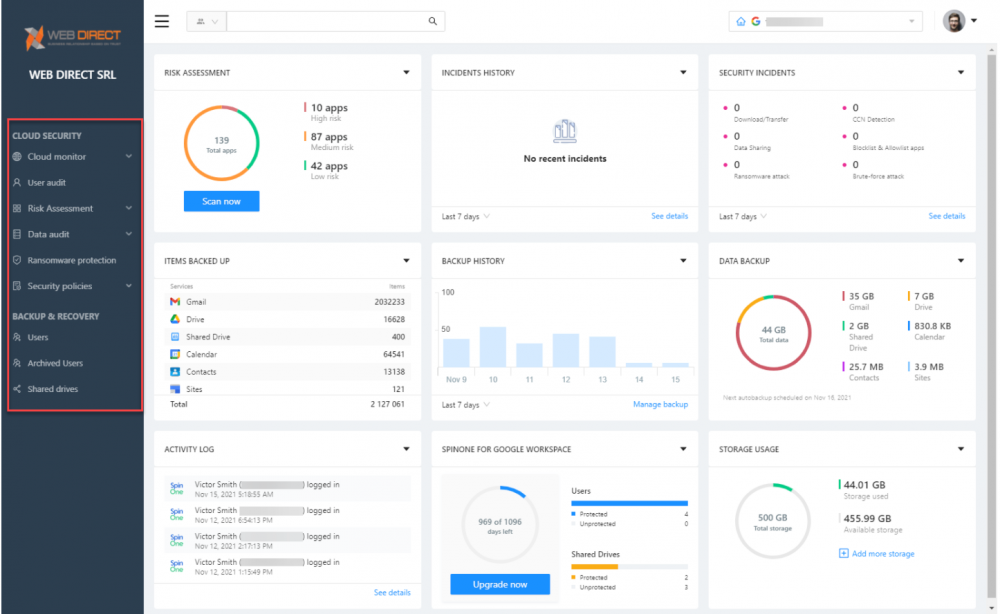
The SpinOne interface provides seamless visibility and controls over cloud SaaS security and backup and recovery in a simple, intuitive interface. An administrator can see risks, security incidents, backup history, protected data, and activity logging from a single view, bolstering both security and compliance of your business-critical data.
SpinOne provides unrivalled backup and cybersecurity features
Learn more about SpinOne and how it can help with security and compliance challenges in your cloud SaaS environment, including ransomware protection and third-party application monitoring and auditing here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....