5 SaaS Security Best Practices for Your Business
SaaS environments like Google Workspace or Microsoft 365 have won over businesses globally. They provide a great set of productivity tools. However, they require a very different security architecture compared to on-prem environments. Here’s our list of SaaS security best practices.
Understanding SaaS Security
To understand SaaS security, you can think about the 80/20 principle. In the on-premise model, 80% of business processes took place within the internal environment. And only 20% of activities took place outside it. This enables the SecOps team to build a strong security perimeter and tightly control all incoming and outgoing data through one protected entry point.
With the adoption of cloud technologies and transfer to SaaS environments like Google Workspace or Microsoft 365, 80% of business processes take place outside the safe perimeter. In fact, now you have hundreds of entry points for data flow. And most of them are not only beyond your control but also beyond your visibility.
The key characteristics of SaaS environments from a security standpoint are:
- absence of a security perimeter
- large attack surface
- lack of visibility and control
SaaS security vulnerabilities include:
- Lack of user control that leads to higher chances of account hijack;
- Uncontrollable OAuth access can cause zero-day attacks;
- Weak protection against social engineering that causes ransomware attacks;
- API limits causing longer downtime in case of an incident;
- No control over user access to sensitive data within and outside organization;
- Lack of security controls within the major SaaS collab tools (GW, MSO 365);
- No native backup tools that can cause data loss;
- Misconfigurations that can cause non-compliance or data breaches.
SaaS Security Best Practices
To protect your business-critical data in SaaS apps, we suggest following several best practices.
Data Backup
One of the must-have practices for any SaaS environment is data backup. CISA suggests following the 3-2-1 rule when you have three copies of data on at least two different media, one stored off-site. We recommend using cloud-to-cloud incremental backup. They will ensure high accuracy of data and high speed of the backup process (which is critical for cloud environments). Recovery, however, takes a longer time.
The backup will help you in case of human error or man-in-the-middle attacks.
Ransomware Protection
Some companies tried to use backup tools for disaster recovery after ransomware attacks. However, API limitations made the recovery process too long. We recommend using proactive AI ransomware protection based on data behavior analysis.
Such tools as SpinOne can detect and stop cloud ransomware within minutes after the attack. They also have an in-built backup, so they recover your data automatically. In some cases, by the time the SecOps team gets to their PC to check on the attack, it’s long over.
Application detection risk assessment
OAuth Applications are the entry points to your SaaS collaboration environments like Google Workspace or Microsoft 365. That’s why many hackers search for app vulnerabilities to exploit, get access to sensitive corporate data, and steal it with a view to selling it on the black market or back to the owners.
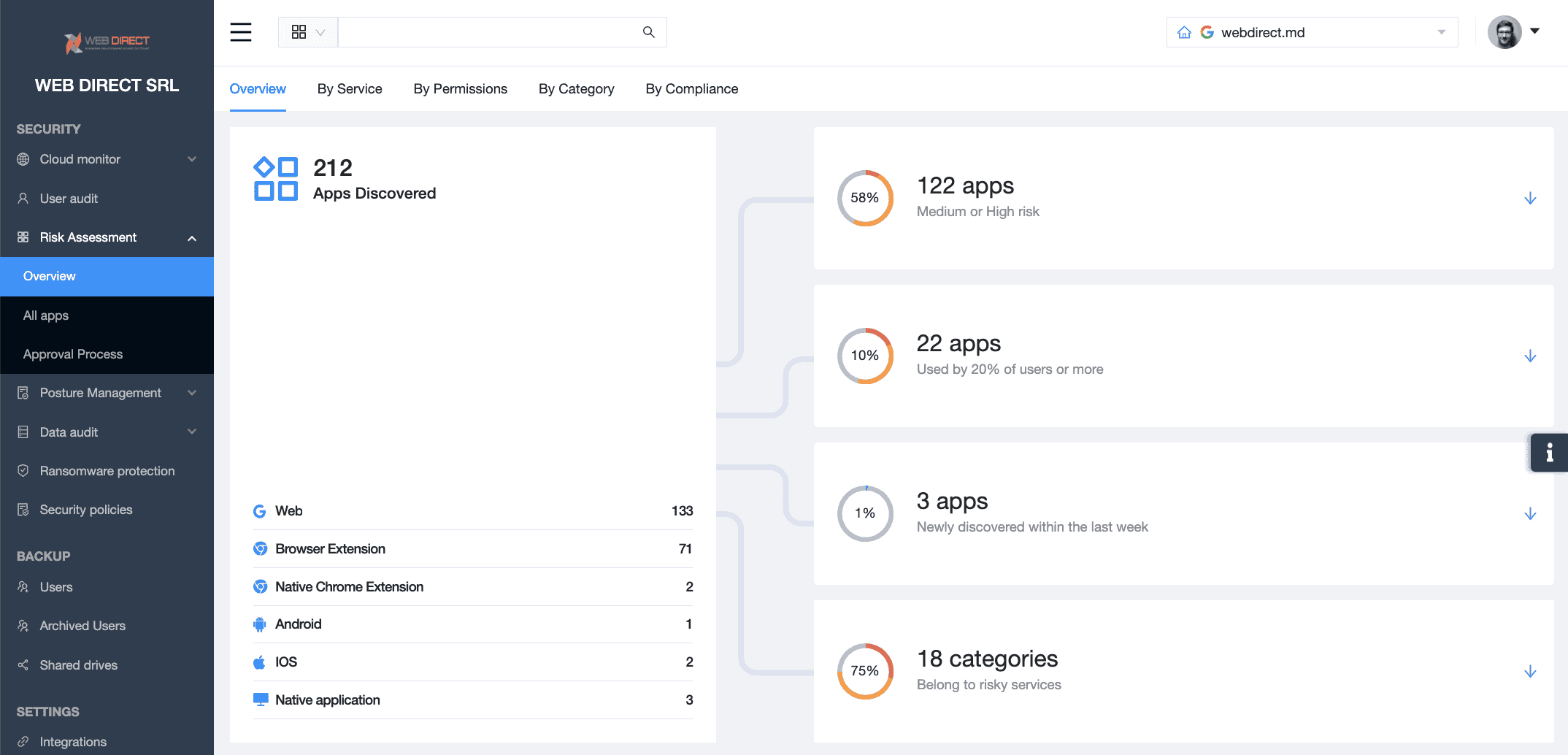
We suggest using SSPMs that can help you detect and evaluate SaaS applications. They also have the functionality to blocklist apps and create policies to prevent users from using their accounts to sign in to applications that do not meet certain security requirements.
DLP policies
DLP policies are algorithms of actions that are triggered by certain events in your SaaS environment. For example, you can disable sharing outside your organization to the majority of your users, or you can receive notifications whenever personally identifiable information is sent via Gmail.
We suggest using third-party tools as they have a wider range of DLP policies you can apply than MSO 365 or GW.
Cybersecurity awareness training
One of the main attack vectors in SaaS environments is your user. Social engineering techniques are abundant and diverse. However, your users can become less manipulative if they are equipped with the necessary knowledge.
We recommend hiring a company that will conduct regular training sessions for your employees. This training should be augmented by regular tests (when fake social engineering emails are sent to your users). It will keep them alert and vigilant.
Keep in mind that cybersecurity awareness training doesn’t guarantee that your users will detect social engineering attacks every time they happen. People get tired and stressed. They lose focus due to work overload or personal issues. That’s why you need other tools to guarantee the security of your SaaS environment.
FAQ
What is SaaS security, and why is it important?
SaaS security is the body of tools and practices to prevent cyber incidents in SaaS applications or minimize their impact.
How does the shared responsibility model work in SaaS environments?
The shared responsibility model in SaaS environments states that SaaS providers and SaaS users share the responsibility for data protection in these environments. The provider undertakes to protect against physical damage and many types of cyber attacks (e.g., DDoS). The vendor on their end is responsible for any incident caused by their users. This includes man-in-the-middle attacks, social engineering and ransomware, security misconfigurations, and data loss due to human error (e.g., accidental deletions).
What are the common security risks associated with SaaS solutions?
The common security risks associated with SaaS solutions are ransomware attacks, man-in-the-middle attacks, zero-day attacks, account hijacking, misconfigurations, unauthorized access to sensitive data, data leaks, and data loss.
How can I ensure the security of user authentication in a SaaS environment?
We suggest imposing multifactor authentication, strong passwords, and regular password changes (both MSO 365 and Google Workspace have the functionality for it). Additionally, we suggest using tools like SpinOne, as it monitors abnormal user and data behavior and helps identify potential account hijacks.
How can I monitor and detect security incidents in a SaaS environment?
It’s better to use tools like SSPM that enable you to monitor and detect security incidents in SaaS environments. Many such tools (e.g., SpinOne) also have an in-built automated incident response, for example, pro-active termination of ransomware attacks.
What steps should I take to evaluate the security practices of SaaS vendors?
Start with the developer and their country of registration. We suggest avoiding individuals and sticking to businesses. Also, we recommend choosing vendors from countries with strong regulations of data privacy and security. Next, check their privacy policy and terms of service. You might need to consult your legal office about it. Search for previously discovered vulnerabilities and make sure that the developer updates the app on a regular basis.
How can I ensure compliance with data protection regulations in a SaaS setup?
Create Data Loss Prevention and data retention policies, acquire third-party backup, and get a proactive ransomware protection tool. Archive old users, conduct regular cybersecurity awareness training, get tools to take applications under control, and monitor user behavior.
What measures should be in place for data backup and disaster recovery in a SaaS solution?
We suggest applying the 3-2-1 backup rule and having an incident response plan in case a disaster takes place. It’s best when everyone knows what to do, and you don’t waste your time searching for solutions and deciding who’s in charge of their implementation. Additionally, it’s good to have backup tools for your employees to continue their work (where possible) while your team is taking care of the incident.
How can I educate and train my employees on SaaS security best practices?
We suggest hiring companies that conduct cybersecurity training with an emphasis on SaaS. Such companies will guarantee regularity, duration, and high training engagement.
What are some emerging trends or technologies in SaaS security?
One of the latest trends is using SSPMs and SIEMs to guarantee multi-cloud control of security. SSPMs control misconfigurations and SaaS apps. SIEMs collect data from multiple sources and use AI to analyze the overall security posture and risk trends.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

