Cyber Security: Work From Home Best Practices
Working from home has always been common, and now more companies than ever have to rely on remote workers. The cyber security aspect of working from home is extremely important, as cyber-attacks are on the rise. Hackers exploit the transformation in the usual workflow to spread malware and steal users’ data. This new working style requires a clear understanding of data security issues. In this cyber security guide, we’ll help you to learn more about risks and cyber security work-from-home best practices. We’ll have a stronger focus on G Suite and Microsoft Office 365 as popular in corporate environments SaaS solutions.
Cyber Risks of Remote Work
For many organizations, the global coronavirus epidemic played a significant role in their decision to let employees work out of office. The cyber security of remote work is what requires the highest attention, as the security breach may nullify all other advances.
Recent research shows that 86% of business executives agreed that data breaches are more likely to occur when employees are working out of the office. It wouldn’t be an exaggeration to say that remote work is a serious challenge, and the inability to face it correctly leaves your data vulnerable. There are various cyber risks for your data. They include insider threats, phishing, and ransomware.
Insider Threats
Insider threats include all potential risks of human error or malicious intent. Employees may accidentally delete important data, initiate a cyber-attack by clicking a corrupted link or downloading an infected file, disclose sensitive data to a criminal, or intentionally steal corporate data. No matter the form, insider threats lead to serious financial and reputational losses.
Insider threats are especially serious for remote work. The control may not be as established as with on-site work, which leaves space for human error or malicious actions.
Phishing
Phishing is one of the most significant cyber security risks, especially for remote workers or during the transition period between the office and remote work. Working from home involves a greater number of emails than office work, as they replace verbal communication. For hackers, more emails mean more opportunities to steal your data or infect your system with malware.
Phishing attacks are tricky because even one sloppy click can put the whole system in danger. A home provides a relaxed atmosphere, and it’s easy to get carried away and not pay the required attention. That will result in clicking a malicious link or downloading a corrupted attachment.
With many people shifting to remote work due to the coronavirus outbreak, the related phishing went up 667% in under a month. And not without a reason. As you probably know, phishing involves various social engineering methods. Exploiting fear and uncertainty is one of them.
Ransomware
Ransomware is malicious software used by hackers to encrypt data and demand money to give that data back. Popular in corporate environments, services like G Suite and Microsoft 365 are often targeted with ransomware attacks.
Why is ransomware so dangerous? Even if ransomware infects one account, it can spread through the whole network. Ransomware may be spread using phishing emails, but there are other ways to get it: system exploits, insecure devices, corrupted apps. You can read more about this in our article about how ransomware works.
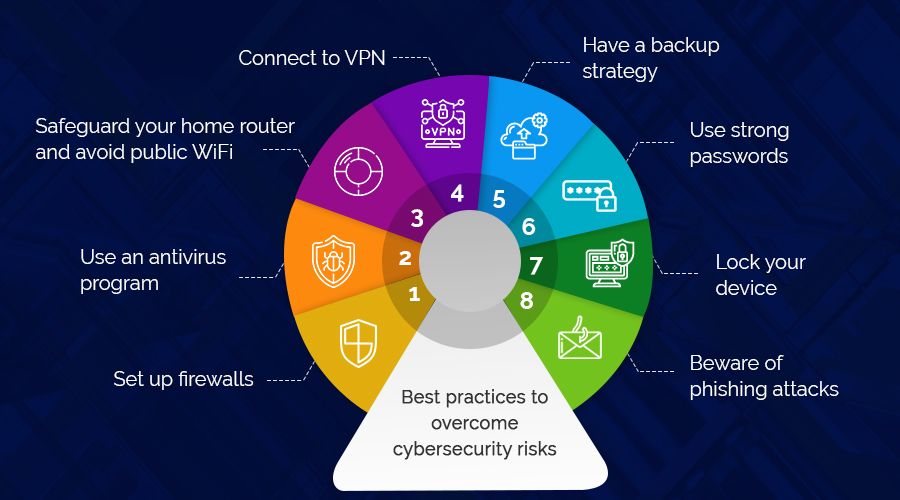
Work from Home Best Practices for Cybersecurity
The cyber threats mentioned above result in billions of damage each year. Recently, the number of cyber-attacks has risen as criminals try to exploit the vulnerabilities of remote work.
To keep your data safe, you need to create a secure remote work environment. The key is to use a multi-layered approach and use various cyber security measures simultaneously. Here are the cyber security best practices that will help you to protect your data.
Select Tools to Work from Home
The first step of remote work is to choose the toolset you’ll use to organize the workflow, such as communication tools like Slack or Skype for Business. However, communication is not the only thing you’ll need. Security is important as well. That’s why using cyber security tools is recommended to protect your remote work environment. Check our list of tools for remote workers and find the tools suitable for you.
Back-Up Your Data
A backup is a safe copy of your data, stored separately from the original data. Backups are helpful against phishing, ransomware, and insider threats alike.
If something goes wrong, having a backup is essential to restoring lost files and emails. Having a regular data backup is one of the best cyber security practices. Here you can read how to back up your data and why it is important.
If you are a G Suite or Microsoft 365 user, you can try our backup solutions. For your convenience, a free trial is included.
Google Workspace Bakcup and Microsoft 365 Backup
Encrypt Important Emails
When you are in the office, printing a document and sharing it with your colleagues is common. However, remote work makes you rely entirely on emails. That’s why protecting them may be a great solution for you. Cloud services like G Suite and Microsoft 365 allow you to encrypt an email. Encrypting an email you send is a good way to protect its content.
Set Up a Strong Password Policy
With all sophisticated cyber security tools and practices, passwords are often left behind. They definitely shouldn’t be. A strong password policy is one of the best cyber security practices. Ensure that your passwords:
- Are at least 8 characters long
- Contain both upper and lowercase letters, digits, and symbols
- Do not look like “11111,” “qwerty,” and such. They won’t stand against a brute-force attack
- Are changed every 90 days or more often
Insider Threat Management
Suspicious or careless behavior may, potentially, be an indicator of high risk. Insider threat detection and control are vital to prevent data loss. Trying to control insider threats manually is ineffective and too time-consuming.
The most accurate method to manage insider threats is to monitor the usage of your data with special tools. SpinOne will help with risk assessment and identification of abnormal user behavior to ensure your cloud data is safe.
Access Management
Access management is also a good way to limit insider threats. It may be a good idea to limit access to important information for users who don’t need it in their working process. Access management improves the visibility and control over cloud data.
For example, Microsoft 365 allows restriction of data access in the Security and Compliance Center. By configuring roles and permissions, an admin can restrict the access to vital information and give it additional security.
Use Ransomware Protection Tools
Backups will help you to restore your data in case of a ransomware attack, but it’s better to prevent ransomware attacks from affecting you. Ransomware protection tools will help you to detect an attack early and stop it before all files are damaged.
Keen to get a deeper dive into ransomware protection? You can read more about it in our articles about ransomware and antivirus software and ransomware detection using machine learning.
And if you want to see how our anti-ransomware tool works, click below to get a demo.
Always Be Careful and Double-Check
It may seem trivial, but everyone needs to be careful all the time. Always think before clicking a link or downloading a file. Are you sure that everything is safe? Even a moment of incaution may result in accidental data deletion or falling for a phishing attack. As we’ve mentioned before, malware can spread through the whole network, so the potential risk grows as the network scales.
Keeping focus while working from home may be a challenge, but it is essential. After all, your data and the data of your colleagues depend on it. Though everything is not so scary. With backups and other cyber security tools, human error becomes less dangerous.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


