Secure Your Data with Cloud Agnostic API-driven CASB
Traditional security mechanisms in today’s hybrid network configurations are simply no longer effective as a means to secure communications and data for organizations. Today’s end user’s no longer fit the traditional work force coming from behind the same firewall, IP subnet, and crossing through the same firewall to get to the Internet/public cloud environments. Today’s highly mobile workforce make use of a variety of devices including a mix of BYOD devices as well as corporate issued devices. This creates the challenge of being able to secure data from these various endpoints as well as to apply various organizational policies so as to create a homogenous security posture across the board for various devices.
Public cloud environments such as Google’s G Suite and Microsoft’s Office 365 environments are heavily used by today’s organizations who have either migrated or are migrating data and services. The problem for enterprise businesses today is that connectivity to public cloud environments does not route through organization firewalls as mobile devices and other connectivity can simply connect via the Internet to these public cloud environments.
Cloud Access Security Brokers are a powerful solution for organizations today to be able to enforce security policies between on-premises enterprise environments and the public cloud environment. We will take a look at the various implementations of CASB deployments and which is the most effective and modern approach. Additionally, we will look at the cloud-agnostic API-driven CASB from Spinbackup and how it provides a fully-featured, modern, and multi-cloud solution that allows organizations to secure public cloud environments with standard security policies across the board.
Cloud Access Security Broker Technologies
Today’s businesses are more mobile than ever before. With that being said, the end points and end users are often global in footprint. More businesses than ever before are utilizing public cloud environments to store their business-critical data as well. Cloud Access Security Brokers or CASBs are often the “go to” solution to allow organizations to have the control and management tools needed to keep their data safe. Cloud Access Security Brokers or CASBs sit between the on-premises environment and the public cloud vendor to inspect traffic to ensure it aligns with business policies as they are enforced on-premises.
CASBs help to ensure that public cloud access is in accordance with sanctioned use. This is especially critical for certain industries that fall under strict regulations. CASBs help to ensure visibility, compliance, data security, and threat protection. What are some of the more detailed key features that today’s modern CASBs provide organizations utilizing them to protect and extend on-premise to public cloud data and security?
Today’s advanced CASBs provide the following and many other capabilities:
- Discovers public cloud applications including those applications that may be high-risk
- Discovers high-risk users and user behavior and activities that may give evidence of unscrupulous activity or a compromised user account
- Helps to prevent unsanctioned “Shadow IT” operations
- Enforces security access controls including encryption, device profiles
- Allows enforcing policies at the public cloud that align with on-premises environment usage and access policies
- Protects against and prevents data loss between sanctioned public cloud environments and those that are not sanctioned no matter where data is being accessed from including mobile device, web browser, mobile app or other application client
- Prevents data leakage of data that is deemed sensitive such as credit card or social security number information
- Protects against malware and ransomware threats by allowing visibility to anomalous activities and gives businesses real threat intelligence metrics to analyze public cloud activities
- Leverages machine-learning algorithms to intelligently analyze learn based on constant profiling of the public cloud environment
Having the ability to provide the above-mentioned capabilities from a security and compliance perspective for today’s public cloud-centric organizations is essential. Traditional means of controlling data by means of on-premises technologies are simply no longer relevant or effective at securing data. With the aforementioned capabilities in mind, businesses can make use of two basic types of CASB technologies – Proxy/Firewall and API based. What are the differences between the two? What are the advantages and disadvantages of each solution? Which solution is the more effective, modern approach for today’s businesses looking to implement CASB technology
Proxy/Firewall vs API Based CASBs
As with any technology, Cloud Access Security Broker technology has evolved over the years. Organizations who are considering CASB technology to protect their public cloud environments want to ensure they choose the technology that provides the most capabilities and security feature set available. With that in mind, there are two types of CASB technology that can be implemented to scrutinize public cloud traffic. They are the firewall/proxy CASB and the API CASB. The API CASB is the more powerful of the two options. Let’s see why that is the case.
The proxy/firewall based CASB works very much as you would imagine. As we think about the model of how a traditional firewall sits between the outside world and an internal network and then scrutinizes traffic passing between, this is very much how the proxy/firewall based CASB works. With the CASB proxy approach, all connections must be made through the proxy CASB address before the CASB can effectively apply policy and filter traffic.
An additional drawback is the traffic destined for the public cloud environment must explicitly be configured for flowing through the proxy based CASB. If a client is not configured to utilize the proxy/firewall CASB, the traffic will not be appropriately scrutinized. A limiting factor that also comes into play is some devices do not support being configured to take advantage of proxy based CASB connections. This will affect the ability of the CASB to filter and scrutinize traffic This is not ideal for security purposes.
This is not the case with API based CASB configurations. API CASB configurations utilize a modern mechanism of querying and interacting with various software technologies. APIs are essentially the modern programmatic vehicle that provide software interfaces to code. Public cloud vendors have built an entire management ecosystem on top of RESTful API interfaces. This model allows interacting with web services using object-oriented programming languages so developers can call and reuse code as appropriate. RESTful APIs allow third party software such as API based CASBs to effectively interact and essentially integrate as part of the public cloud fabric so that it is not a single entity or “inline” mechanism such as the proxy/firewall-based configuration, but rather part of the public cloud environment.
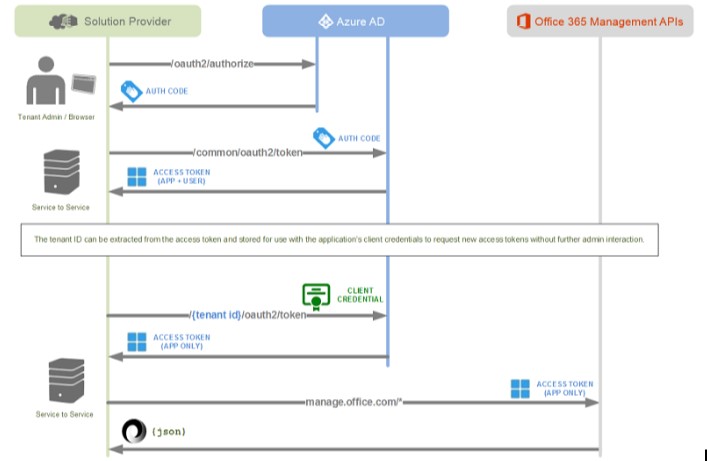
Microsoft Office 365 Management APIs conceptual drawing (Image courtesy of Microsoft)
All of the downsides of the proxy/firewall CASB implementation are no longer relevant. Clients no longer have to be configured to utilize the proxy/firewall CASB for accessing the public cloud environment. Unsupported clients are no longer able to bypass the enforcement of organization policy. With API based CASB implementations, public cloud environments have the means to natively apply policy, search for threats, and scrutinize user and application behavior. This also opens up the possibility with today’s powerful machine learning technology to be integrated with API based CASB implementations to allow the CASB solution to learn based on activity in the environment.
Spinbackup Cloud Agnostic API Driven CASB
Businesses today are faced with the monumental security challenges that come with spanning on-premises networks and often multi-cloud environments to form complex hybrid networks. Cloud Access Security Brokers or CASBs allow organizations to take a modern approach to securing data access and allowing policy application to be homogeneous across both on-premises and public cloud environments. With API driven CASB implementations being the most capable and desired approach to implementing a CASB solution for the reasons mentioned above, let’s take a look at how Spinbackup’s API driven, cloud agnostic CASB approach allows businesses to have secure, consistent, and seamless public cloud environments that mirror the policy and security controls already in place on-premises.
Spinbackup provides one of the most powerful API CASB implementations available to organizations today, allowing businesses who utilize Google G Suite or Microsoft Office 365 to protect business-critical data and services. Spinbackup provides a machine learning enabled solution that constantly scans public cloud environments looking for anomalous behavior. It also ensures data loss protection and prevention mechanisms that ensure data never leaves the public cloud environment for unsanctioned use.
Spinbackup’s API based CASB provides data security beyond the robust feature set of API based CASB. Spinbackup allows organizations to have a fully featured data protection solution that allows creating cloud to cloud backups. This is an extremely important point for organizations to consider. No matter which public cloud your data exists in, you want to have the flexibility to be able to target the storage of your choosing for backups.
Recently, Spinbackup added Google Compute Storage to the list of possible storage options for public cloud backup data. Now, businesses have the ability to backup Google G Suite environments and Office 365 environments and store the data in either Amazon’s AWS or Google Compute Storage. More storage options are being added as well to give organizations the flexibility needed to accommodate businesses needs. This allows organizations the ability to diversify business critical data to keep from having “all the eggs in one basket”. In considering best practice for storing your backup data, you never want to store it in the same location or service that may experience issues affecting not only production but also protected data.
Besides the flexibility in storing backup data (which backups of public cloud data in itself is even outside the scope and abilities of other CASB solutions), Spinbackup provides tremendously robust and fully-featured cybersecurity protection for organizations and their public cloud data. This is provided by Spinbackup’s API driven CASB implementation.
Data Leak Protection. Protects against unsanctioned data downloads and movement of data between public clouds.
Risky Third-party App Protection Allows scanning and blocking access from risky third-party apps that may have been installed by end users and allowed to have permissions to business-owned data
Sensitive Data Protection. Allows protecting against the leakage of sensitive data such as credit card numbers outside the public cloud environment.
Ransomware Protection. Automatically detects and remediates ransomware infections that may be attempting to encrypt public cloud data.
Insider Threats. Protects against the activities of unscrupulous employees as well as possible user accounts that have been compromised.
Machine Learning Algorithms. Spinbackup provides next-generation machine learning capabilities that allows organizations to have the “eyes on glass” feel of a fully staffed security operations center or SOC. The machine learning algorithms constantly watch your public cloud environment and alert based on any anomalous activity.
Real Time Alerting. Gaining visibility into activities inside the public cloud environment. Part of the challenge with managing and maintaining public cloud environments is having the needed visibility into events that require further investigation. With the alerting capabilities in Spinbackup, organizations can receive alerts for relevant events as they are seen by the machine learning algorithms.
Single Pane of Glass Dashboards. With the Domain Audit and Data Audit dashboards, administrators can quickly filter and search for events that are relevant to security and other data anomalies in the public cloud environment.
These powerful API-driven CASB capabilities found in the Spinbackup solution provides not only protection, but also intelligence and visibility to both security and user/app activities.
Concluding Thoughts
Today’s cloud driven world provides real business challenges for organizations who are thinking of migrating or have already migrated data to the public cloud. Public cloud environments create complexities that are simply not seen with traditional networks in the enterprise environments from years past. Today’s modern technology driven businesses are often multi-cloud in scope and have end users and endpoints that may span across the globe. Cloud Access Security Brokers allows businesses to be able to apply the same policies and filtering across both on-premises networks as well as access to business data and services stored in the public cloud.
Today’s API driven CASB solutions allow the CASB to become part of the public cloud environment, rather than a “bolt-on” mechanism requiring each end user device be specifically configured for utilizing the CASB for access. This prevents bypassing the control of the CASB solution as can be the case with proxy/firewall CASBs. Spinbackup’s machine learning enabled API driven CASB solution allows businesses to have a cloud agnostic and flexible solution that is multi-cloud compatible. It also allows businesses to choose where data is stored to meet with data protection best practices and business objectives
Spinbackup provides organizations with the “eyes on glass” feel of AI intelligence guarding their business-critical data 24/7. By using Spinbackup’s API driven CASB, businesses can safely, effectively, and confidently utilize public cloud resources with the intelligence, protection, and insights needed for today’s modern technology-oriented businesses.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security Web browsers are not just passive...
Enterprise Browsers vs Risk Assessment: A Comparative Analysis
New threats are hitting organizations at a rapid pace. Businesses must adapt and evolve with...
What is SSPM (SaaS Security Posture Management)
Businesses are feverishly accelerating their move to cloud SaaS apps, now the standard for modern...