Secure Your Device From Ransomware and Malware
Today, mobile devices, mostly tablets and smartphones, are widely expanding and becoming an integral part of our daily life. Users are increasingly storing their personal data on the devices, which they practically do not let out of their hands. It’s practical and useful, but at the same time, it gives rise to new problems. Easily accessible valuable information increases the risk of online threats. Every year, security of mobile devices and the stored data is being given more attention.
Why has Cloud Security Become Important?
Modern mobile devices’ functionality is comparable with desktop functionality. Processing power of mobile devices and the built-in storage grows, which leads to the fact that users can keep a huge amount of data directly on their smartphones. It can be private photos, social, working, or bank account information. We think it would be unnecessary to remind about the importance of such information after the sensational chain of Hollywood stars iCloud accounts hacking and over 60 million Dropbox users credentials theft. And speaking about the corporate environment, security issues are far more important if corporate data, in hands of the third parties, may do great harm to the company.
What Data is Subject to Hacker Attacks?
Access to the Mailbox
Most often, access to the actual account is given only once, both on Android or iOS device. With device loss or theft, attackers might gain access not only to all the correspondence, but to all the services tied to this email account.
The Address Book
Devices can store not only phone numbers and addresses, but almost all personal information of its owner, including his / her social networking information and photos. Such information might be compromising.
Mobile Banking
Using a mobile banking application gives you access to your bank account anywhere, anytime. It is practical and useful for doing business outside of the office, for example, on a business trip. However, what if the device suddenly disappears or is hacked? The answer is – financial losses.

Documents and Notes
Most users store their passwords in the notes or applications that allow keeping data about all services. It means Google Drive can become a source of access to important documents.
Networking
Often, mobile devices are used to access the corporate network via VPN or RDP (Remote Desktop Protocol). In case of an employee’s device loss, the protected enterprise network might be opened to third parties, and this can lead to unintended consequences.
Also, keep in mind, unintentional disclosure. By this term, we mean an activity in which one might not be informed, for example, that some applications on the device may redistribute the information about the person’s location. This may occur when you use social media or application-partners that provide discounts in cafes or bars.
Ransomware
This is perhaps one of the worst attacks. Ransomware can harm your device in several ways. All the data on the infected device gets locked by a hacker until the owner of the device pays a certain sum of money to this hacker. Ransomware is an intelligent and smart malware, as it’s almost impossible to track a hacker due to the payment in the form of bitcoins. If you don’t want your phone to get locked or all your data encrypted, better watch the suspicious files or links you try to open. Check our ransomware protection tips to learn more.
How to Protect Your Information?
Be aware of suspicious emails and messages that come from unknown people
Such messages may contain links, files, or instructions that can take control over your device for the attacker in case of its execution.
Data Encryption
Today, iOS and Android offer data encryption. If you value your information, then you should think about encryption. Encrypted data is virtually impossible to read without a specific key, which only the person who created it knows, eliminating the chance of interference by an outsider.
All you need to do is go to the Settings, tap on the “Security” tab (on your device, it can have a different name), and then click the “Encrypt phone”, read the warnings carefully, and agree with it.
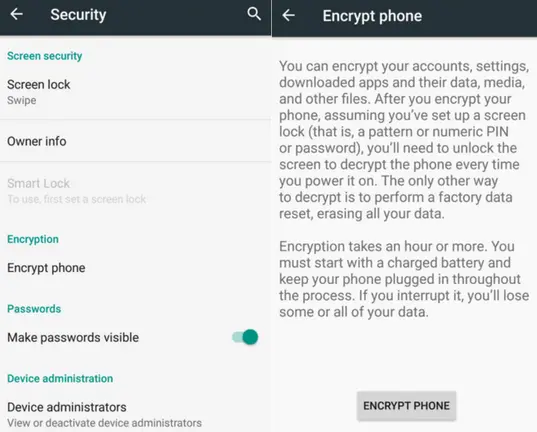
If the device has been encrypted, it will be indicated. Some smartphones or tablets also allow encrypting the contents of the SD card.
The important thing is that you need to make sure your device is fully charged, and you have half an hour to one and a half hours of free time. Also, do not interrupt the process, because it threatens data loss.
Use Only Official Application Sources
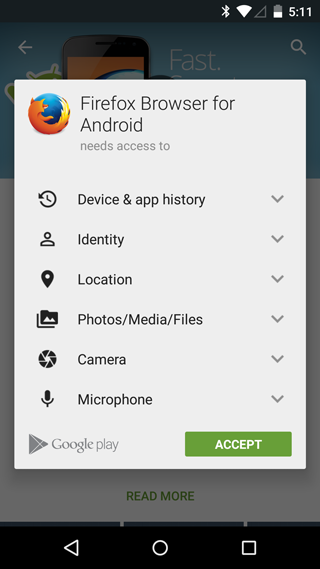
Using the AppStore or Google Play Market reduces the risk of infection by Ransomware and other malware. Policies of these stores do not allow programs that can harm a device or someone’s personal data, and every app is strictly moderated before publication. Although it cannot guarantee 100% protection, so check the permissions required by the app, because it would be strange if the flashlight asked to use a microphone or camera, right?
Backup Your Data
Cloud-to-cloud backup enables valuable information to be accessible. Even if you lose your device or it is blocked by hackers, you can always get access to your files, provided the copies are not on the infected phone.
Be Careful Using a Public Network
Though wireless internet access is available in almost any place, usage of the unprotected access points can lead to data loss. Attackers can intercept and analyze (sniff) traffic generated by your device and consequently gain access to your data. To avoid this, it is recommended to use mobile internet instead of a public network.
If you nevertheless connect to a public Wi-Fi, pay attention to the pop-up messages from active applications, for example, a Gmail client. Usually networks use protected SSL connections, and you will be notified if somebody is going to replace the security certificate.
Concluding Thoughts
There’s nothing more valuable to us than personal data. Every individual appreciates privacy and feels vulnerable when even a small piece of such data is leaked. If you don’t want hackers to use your own data against you, protect your mobile device, and we hope this article will serve you well in securing your most valuable data!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
6 Common Mistakes in Google Workspace Backup
Google Workspace is a set of productivity apps, including Gmail, Drive, Docs, Meet, and Calendar...
Google Workspace vs. Microsoft 365 comparison
With so many productivity suites available, it can be overwhelming to decide which one is...
Top 10 Low-Risk Applications and Extensions for Google Workspace
Google Workspace is an extremely popular SaaS productivity suite used by millions of organizations today....


