WannaCry Ransomware – a Call for Enhanced Cyber Hygiene
Only one week has passed after a mass phishing attack hit the Gmail users, and the world came under attack by a new global cyber threat called WannaCry ransomware. One month ahead – new victims of WannaCry appear: the Honda car plant and an Australian government contractor. These cloud ransomware attacks, as our security experts predict, might become the turning point for individuals and organizations all over the world in strengthening their overall cyber security.
WannaCry – a New Ransomware Threat or an Old Virus?
The algorithm of a virus is simple but dangerous. An email with malicious attachment was sent to a number of users, and when they opened it, the virus infected their computers and ciphered their files. The hackers used Eternal Blue that exploited a Microsoft MS17-010 vulnerability. It let the virus spread over the corporate system and scan all connected computers for the same vulnerability. If the attack had stopped at the first wave, only separate individuals would have been compromised, but with Eternal Blue, the problem mushroomed to the enterprise level.
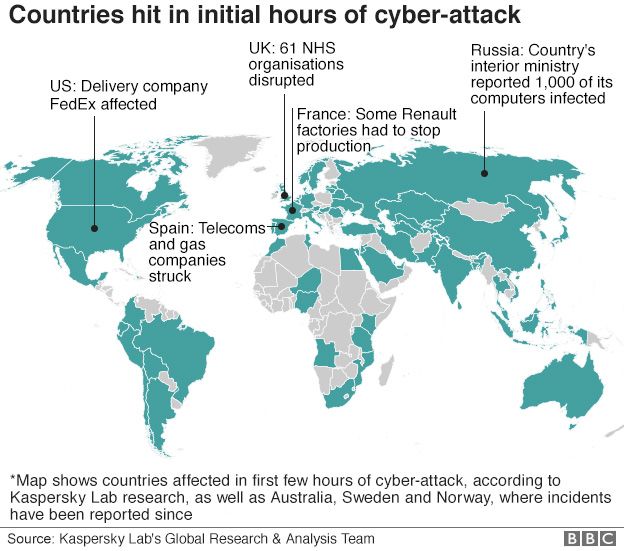
Actually, there is nothing special and sophisticated about WannaCry. It did not make a zero-day exploit, but used the vulnerability that had been discovered and fixed by Microsoft in March 2017. Like the 90% of all hacker attacks throughout the world, it used the vulnerability discovered by the OS developers – not by hackers themselves – during the last 1-2 years. Such attacks target users of outdated operating systems and those who have not updated their software.
This partly explains why Russia, Ukraine, India, and Taiwan suffered the most: at these places many people download cracked Microsoft copies instead of buying legitimate Windows licenses, and such copies are obviously not updated properly. In Great Britain, multiple medical organizations were infected presumably because they used Windows XP and Server 2003 that are no longer officially supported by Microsoft. The attack hit companies at over 150 countries and caused estimated costs of the hack varying from hundreds of millions to $4 billion.
What Is the Solution?
There are two theoretical ways to decipher your data. The first is to pay ransom. For many companies $300 may not seem a high price for their valuable databases and files. However, we emphatically discourage you from doing so. Not only do you sponsor the efforts of the bad guys but also not a single case has been reported of anyone receiving their files back. You can never be sure that your files will be decrypted after submitting payment.
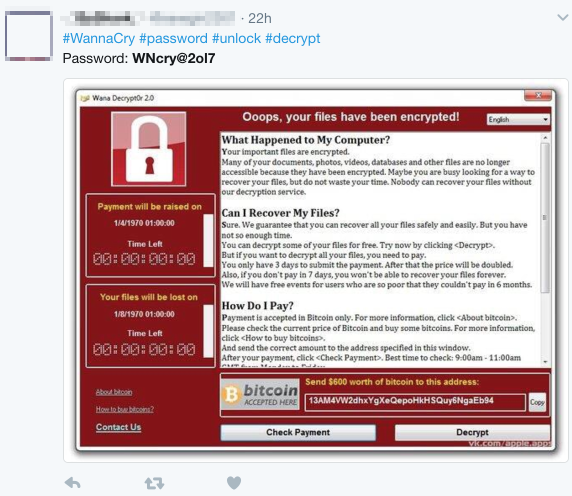
The second theoretical way in ransomware cases is to use decryption software. Here, the problem is that every new type of ransomware creates a new code that complicates the work of finding a decryption key while old keys no longer do the job. Antivirus and internet security companies work hard on it, but you never know when the decryption software will become available. And for corporate data, containing your sensitive files blocked for even one day can result in significant data loss with serious financial implications. You may have probably read multiple tweets about the code WNcry@2ol7 that allegedly deciphers WannaCry files. Actually, this is fake and as of this point no decryption key exists for this type of malware.
How to Prevent Ransomware Infection?
Here we come to the basics of cyber security hygiene for Ransomware protection in the cloud.
Backup to a secure third-party storage is the only 100% secure way to recover your files after ransomware and build a cyber-resilient strategy. For successful recovery, backup must take place BEFORE the ransom occurs. And you never know when it will occur.
Look at the simple analogy. Why do you brush your teeth every morning? You protect them from cavities and plaque. You don’t wait until the diseases occur, rather you take measures beforehand. This is how it works with dental hygiene, but the same is true for cyber hygiene. You did not need backup fifty years ago because personal computers and cyber data did not exist. But as the technology evolves and becomes an integral part of our lives, as the information stored at cloud and hardware storages becomes critical, and as hackers become even more sophisticated, backup becomes a must-have tool for everybody: from a middle school pupil to global enterprises.
Life gives us a wake-up call that the time for the early and late majorities to backup their data has arrived. The cloud is as vulnerable to ransomware virus as local computers are by the means of desktop synchronization. Furthermore, experts predict that in the nearest future the cloud will be attacked directly via malicious third-party apps. To remove human factor from ransomware protection, we have released Automatic Ransomware Protection that automatically detects the attack, blocks its source and recovers damaged files with no human resources involved.
If you worry about data stored at G Suite like Gmail, Google Drive, Shared Drives, Contacts, Calendars, here at Spinbackup, Backup and Recovery and Automatic Ransomware Protection pricing plan for G Suite is only $5/user/month. Is your data worth of $5?
After you subscribe to Spinbackup, your G Suite applications data will be stored at secure Amazon server. And then it will be automatically backed up EVERY DAY. If you become a victim of ransomware, youк sensitive data will be automatically restored and you will learn that ransomware occurred from a Spinbackup security alert only. This way you are protected around the clock.
What Should We Learn from WannaCry Ransomware Attack?
The conclusion is short and the recommended course of actions is obvious.
- If you were attacked by WannaCry, we recommend reinstalling your OS at all infected computers and install Microsoft patch MS17-010 as soon as possible.
- Always update your software to the latest version.
- Always have your data backed up to 3rd-party cloud storage automatically, on a daily basis. Work only with trusted backup providers that use encryption in transit and at rest.
Discover more on how to protect your corporate sensitive data from phishing attacks and ransomware. Do not wait until you become a victim – protect your data proactively!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
6 Common Mistakes in Google Workspace Backup
Google Workspace is a set of productivity apps, including Gmail, Drive, Docs, Meet, and Calendar...
Google Workspace vs. Microsoft 365 comparison
With so many productivity suites available, it can be overwhelming to decide which one is...
Top 10 Low-Risk Applications and Extensions for Google Workspace
Google Workspace is an extremely popular SaaS productivity suite used by millions of organizations today....


