Why Daily Third-Party Apps Audit is Important?
The latest malware to hit Android users was discovered in the last week by the research team at cybersecurity firm, Check Point. Over 1 million Google accounts have been hacked by the malware to date and this figure is rising all the time, with an additional 13,000 affected devices being discovered every day.
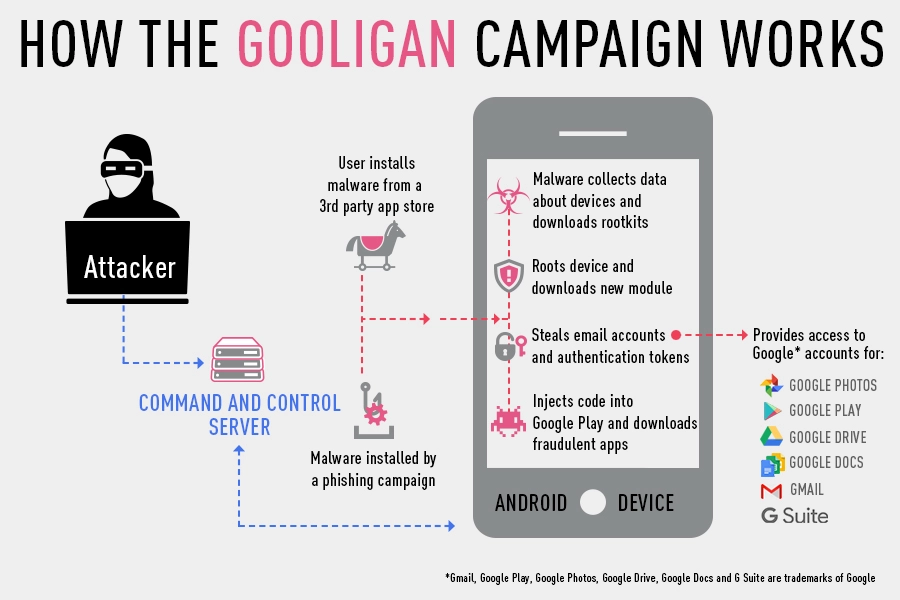
The malware, known as Gooligan, roots infected Android devices and steals email addresses and authentication tokens that can be used to access all G Suite data including Gmail, Google Docs, Google Photos, Google Drive, Shared Drives, and G Suite.
The Dangers of Gooligan
*Source: Check Point.
Gooligan affects devices using Android 4 and 5 (Jelly Bean, Kitkat, and Lollipop), which accounts for over 74% of devices in use today.
After the Gooligan-infected app is installed, the malware downloads a rootkit that allows the hacker to take full control of the device and allows remote execution of privileged commands.
After rooting the device, another module is downloaded that allows Gooligan to steal the user’s Google account and authentication tokens.
A statement from the Google Security team suggests that Gooligan was created in order to promote apps rather than steal user information, and asserts that user data has not yet been compromised. While this may be true currently, the potential certainly exists for sensitive personal or corporate information stored within Google apps to be accessed and manipulated, either by Gooligan or other similar malware.
What Can Gooligan Do?
- Grab authorization tokens
- Add additional apps to the device
- Rate apps at Google Play
- Play in-app ads on the device.
How Does This Affect the User or Help Hackers?
1. Grab Authorization Tokens
The hacker gets full access to the data stored in Google services.
The stolen authorization tokens allow the hacker to bypass two-step-authentication and gain access to the user’s Gmail account as if they were already logged in. Even if the user removes the malware from his or her device, the account is still compromised until the password is changed.
This allows the hacker to access all data from Google apps including Gmail, Google Docs, Google Drive, and G Suite.
2. Add Additional Apps to the Device
After rooting the device, the malware downloads a further malicious module that allows it to install further apps from Google Play. These apps could potentially contain more malware.
Check Point traced the server where Google account tokens were being uploaded to and by examining the server logs, found that up to 30,000 apps were being downloaded each day by infected devices.
3. Rate Apps in Google Play
After hijacking the user’s Google account, Gooligan uses it to rate apps in the Google Play store without the user’s knowledge.
Not only does this artificially raise the ranking of dubious apps and links them to the Google user, but rating apps also uses device resources and can cause the system to slow down as well as using data over the Internet that the user may be charged for.
4. Play In-App Ads on the Device
These ads are a further drain on the device’s resources and can be very annoying for the user. It is also possible that they may link to phishing sites, which could cause the device to be further infected with more malware and viruses.
This system of forcing users to download apps which play advertising is known as Ghost Push malware and is part of a huge advertising fraud scheme estimated to be making the hackers as much as $320,000 a month.
The Risk of Third-Party Apps
Gooligan is a perfect illustration of how risky third-party apps can be for any organization using G Suite, particularly those with a BYOD policy. It is extremely difficult to control which apps employees choose to install on their own devices, but compromised apps can cause a serious data breach, exposing sensitive corporate data that is stored within G Suite.
Malware can easily be hidden in 3rd-party apps that are downloaded from a 3rd-party app store. These app stores do not have the rigorous controls in place that are required for listing an app in the Google Play store. However many users are tempted to install apps this way if they are not yet available officially from Google or because they offer a free version of an app that normally must be bought.
Phishing campaigns are another way that malware can make its way onto an Android device. By clicking a link in an email or SMS, the user may inadvertently install an app that they never intended to download.
Once installed, it is not usually clear that the app was created for malicious purposes. Malware and phishing software are commonly disguised as a legitimate app, or hijacks genuine apps due to insecure code.
How to Protect Yourself and Your Company Against Gooligan
To check if your device has been infected by Gooligan, you can enter your Google email address at the official Check Point Gooligan checker, to see if your account has been compromised.
If your device has been found to be infected with Gooligan, the recommended course of action is:
- Completely reinstall the operating system on your device.
- Change your Google password – this will revoke the token stolen by the malware.
- It’s also essential to make sure that your data is backed up at all times in order to recover quickly from this eventuality.
Only allowing installation of company-approved apps that have been researched and deemed to have low risk is one way of protecting your organization from Gooligan and other malware. At the very least, apps should only be installed from the official Google Play Store (or the Apple App Store).
However this is rarely a practical solution and severely restricting employee installation of apps can also mean missing out on the improved productivity and collaboration opportunity that many apps provide. Additionally, it can be very difficult to completely block the installation of unapproved apps, particularly on employee’s own devices. Blocking installation via Google Play only increases the temptation to install even riskier apps through 3rd-party stores.
A more proactive and realistic approach is to use an app monitoring system such as the Cybersecurity service with 3rd-party apps audit, available from Spinbackup.
The 3rd-party apps audit monitors all apps that have been granted access to Google account data on an automatic daily basis, and apps are graded automatically based on their risk level. Apps with a high level of risk can be blocked and have their permissions revoked, directly from the administration panel.
Spinbackup is currently improving its smart-algorithms so that any apps infected with Gooligan can be automatically detected and an alert sent to the G Suite admin.
To date, Spinbackup has already detected several infected apps in our current clients’ accounts and this number is expected to increase – over 80 fake apps infected with Gooligan.


