CISO Guide to Securing Control over Sensitive Data Access
There is a data classification that extends beyond “normal” day-to-day data. This type of data is sensitive data. Sensitive data is some of the most sought-after data by attackers and is the type of data that can hurt organizations the most when it is leaked, lost, or stolen. What are the common sensitive data types? What makes them vulnerable? Why are cloud Software-as-a-Service (SaaS) environments vulnerable? How can organizations protect these types of data in cloud SaaS environments?
What is sensitive data?
First of all, before businesses can protect sensitive data, they must understand the types of sensitive data and which data types need to be protected. Arguably the stance of sensitive data is growing broader and more profound as a more significant number of data types are classified as sensitive or confidential.
Historically, sensitive data may have only included social security numbers (SSNs), financial data, or other confidential information. However, new rules for personal, sensitive information classify personal information as sensitive. It includes any information relating to an identified or identifiable natural person.
With compliance frameworks such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and other cybersecurity frameworks, virtually any personal information of an individual is deemed sensitive. These new compliance frameworks and the requirements they entail emphasize the need to protect sensitive data vigorously.
Sensitive data types as defined by today’s compliance regulations include any of the following:
- Racial or ethnic origin
- Political opinions
- Religious or philosophical beliefs
- Trade union membership
- Health data, including genetic or biometric data
- Information regarding a person’s sex life or sexual orientation
As the list details, sensitive personal information and sensitive data, in general, has evolved over the past few years and continues to evolve as modern compliance frameworks come into existence and begin to be enforced at state and national levels.
Why is sensitive data vulnerable?
Private, sensitive information is vulnerable and valuable to attackers. Attackers seek to compromise sensitive personal information found in internal databases, user lists, customer records, payment information, and many other data sources. These are often the first types of systems that attackers seek to compromise for the treasure trove of sensitive information. Information may be compromised due to weak encryption, no encryption, software flaws, or poorly monitored and controlled cloud Software-as-a-Service environments.
These information types are much more valuable on the dark web than other data types. Attackers leveraging ransomware to encrypt and intentionally leak data have much more leverage when private, sensitive data is encrypted and held hostage. It helps to ensure attackers are more likely to receive the ransom payment demanded.
Why are cloud Software-as-a-Service (SaaS) environments vulnerable?
Organizations today are migrating to cloud SaaS environments at a blistering pace. In fact, according to Garner:
Worldwide end-user spending on public cloud services is forecast to grow 18.4% in 2021 to total $304.9 billion, up from $257.5 billion in 2020, according to Gartner, Inc.
Businesses see the value proposition in Software-as-a-Service services hosted in the cloud by cloud giants such as Google and Microsoft. Egged on by the global pandemic, remote work has exploded, and end-users need to communicate and collaborate effectively and efficiently despite location.
Despite their power and the capabilities they offer, public cloud SaaS environments can expose organizations to a lack of control and visibility over sensitive data. Many businesses struggle to understand what data they have after migrating to cloud SaaS solutions. In addition, built-in native tools may lack easy visibility to data locations. As a result, organizations can quickly lose control over their data with sprawling solutions. In addition, the free reign by end-users to share data and use cloud applications freely can exacerbate the problem.
With a lack of visibility and control over their data, businesses can quickly become vulnerable to data leaks and accidental data exposure. Multiple auditing dashboards and different security solutions that directly depend on the cloud SaaS subscription level worsen the problem.
Attackers can capitalize on these vulnerabilities by going after exposed data, using cloud ransomware, or using malicious or unscrupulous cloud apps or browser plugins.
Visibility and control of sensitive data in cloud SaaS environments
Organizations need the right tools to discover sensitive data and enable controls to guard against leaks or breaches. Yet, often, businesses find the built-in security and compliance tools in cloud SaaS environments to be cumbersome, subscription-level dependent, and even lacking in needed capabilities.
Bolstering protection of your sensitive data means strengthening cybersecurity in general and closing cybersecurity coverage gaps. SpinOne provides the essential tools needed by organizations to have visibility to and protect their sensitive data. These tools include:
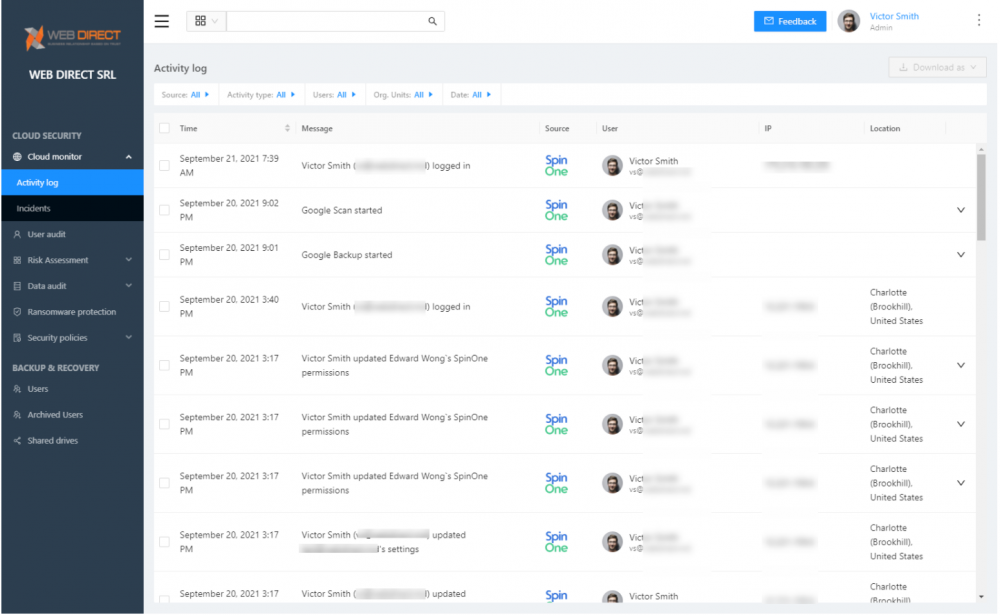
- Cloud Monitor – The Cloud monitor activity log allows viewing all events in the environment, including those produced by the cloud service provider and those triggered by SpinOne. The Incidents dashboard helps IT admins key in on cybersecurity events, including the risk level.
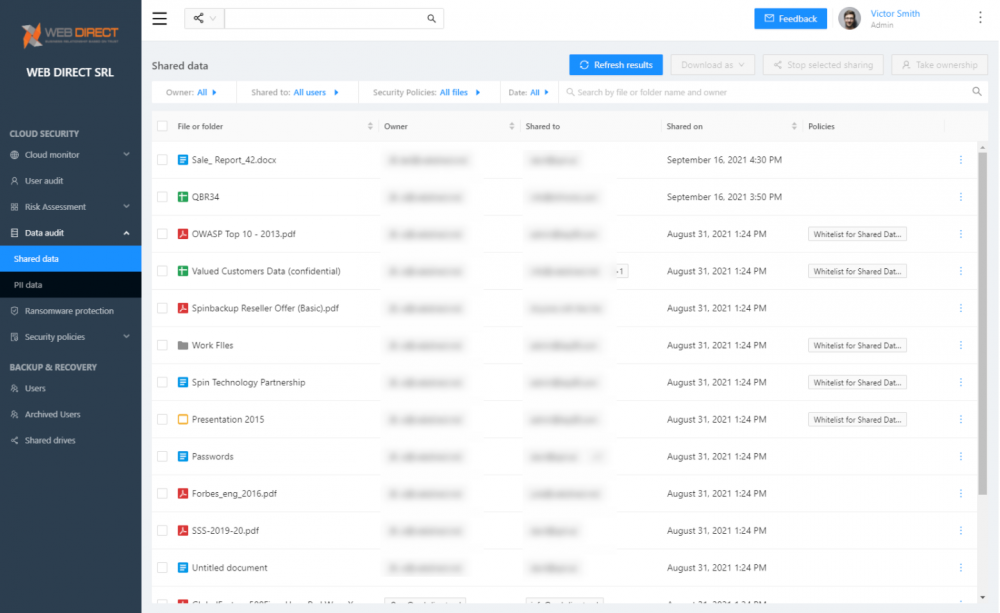
- Data Audit – The SaaS Data Audit dashboard provides the ability to see all data shared in the organization, who shared it, who it is shared with, the data it was shared, and if any policies are applied. It helps to understand how information is exposed in the environment, control these, and remediate them as needed. As part of the Data Audit, the PII data dashboard allows viewing redacted data sent using Exchange Online that is deemed sensitive.
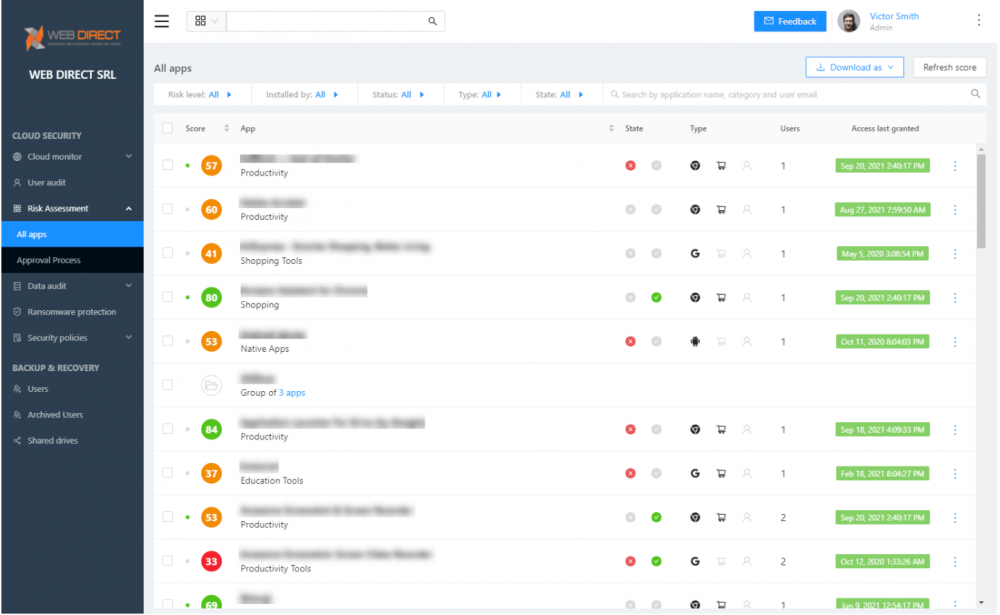
- Risk Assessment – Using SpinOne’s SaaS application risk assessment, businesses can control which cloud apps or browser plugins are integrated with their cloud SaaS environment. Apps can be blocked or allowed, aligning with business policies. SpinOne takes the heavy lifting out of auditing cloud applications by assigning each a risk score based on behavior algorithms. It provides an extremely powerful way organizations can quickly take control of cloud applications.
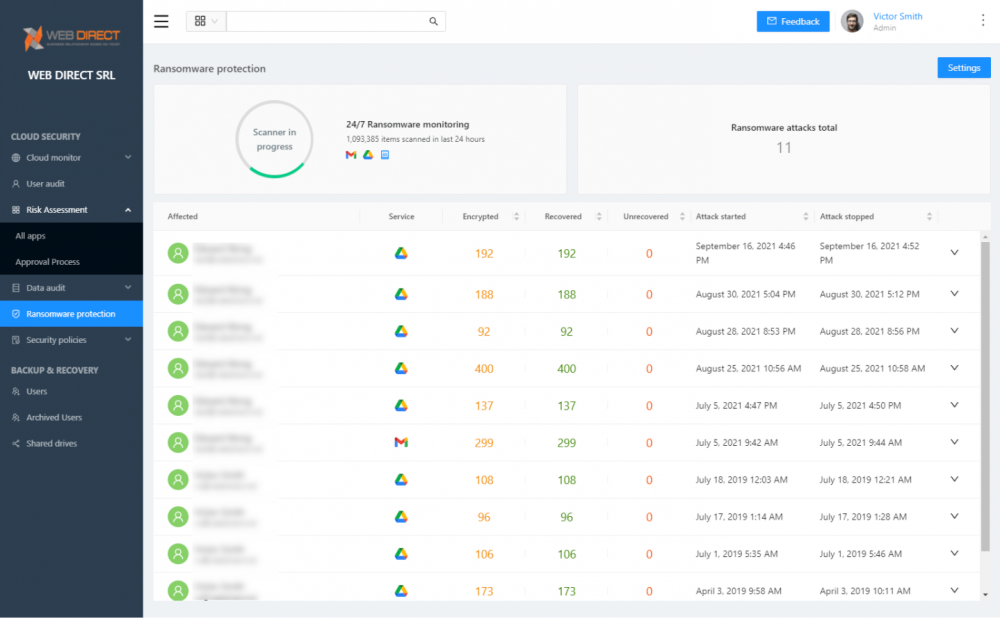
Ransomware protection – The SpinOne ransomware protection module allows organizations to protect against ransomware attacks in their cloud SaaS environment. It automatically detects, stops, restores, and notifies when a ransomware attack is attempted.
SpinOne uses next-generation artificial intelligence (AI) and machine learning (ML) algorithms to perform low-level cybersecurity tasks effectively and efficiently so SecOps professionals can take on higher-level forensics tasks. As a result, it helps organizations streamline cybersecurity and minimize the headcount needed to keep cloud SaaS environments secure. Protecting SaaS data in cloud services like Google Workspace, Microsoft 365, and Salesforce is your responsibility. Stay safe and schedule a demo here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...