Cloud security posture management (CSPM) and SaaS security posture management (SSPM) solutions are two separate, but equally important steps in protecting your data from cyberattacks and breaches.
CSPM focuses on protecting data and apps stored on cloud platforms like Google Cloud, Azure, or AWS, while SSPMs center on monitoring third-party apps outside your cloud infrastructure critical to your organization’s daily operations (Slack, Google Workspace, etc.).
With over 3,000 leaks in 2023, cloud data breaches have become commonplace today and highlight the need for comprehensive data security solutions.
With most breaches being the result of the misconfiguration of a business’s cloud service provider, or their third-party apps, doing more than relying on the basic security measures of cloud services and SaaS applications is needed to keep your data safe.
Below we will go over the roles each plays in plugging potential gaps in your business’s online security in detail, shedding light on their unique features and functions and how they may add to the safety and compliance of your company’s data.
The Evolution of Cloud and SaaS Security
In the mid-2000s, when cloud computing services like AWS, GCP, and Azure first started to appear, concerns sparked over data now residing outside a company’s local infrastructure.
Legacy, on-perm, security was typically a closed network connecting to the outside world through one or two entry points, usually through a local device. Because of this, strong firewalls and physical company security were all that was needed for a secure environment.
However, the lure of cost-cutting cloud servers led to the rapid adoption of cloud services that brought a list of new security threats. Increased entry points, sharing settings, improper configuration, and Shadow IT forced companies to adopt new security practices.
Enter cloud security posture management (CSPM) solutions, and SaaS security posture management solutions soon after, as SaaS applications also became integral to business operations.
What is CSPM?
While cloud services for tech-savvy groups are extremely flexible tools that can help increase efficiency while reducing overhead, improper configuration can open you to costly cyber attacks or data breaches.
Unchecked account privileges, inactive accounts, insecure APIs, and privileges granted to installed applications, are all possible attack vectors for cybercriminals.
Cloud security posture management, then, are the steps organizations take to secure their data across their cloud environments.
These often include monitoring and updating admin accounts, permissions, encryptions, and account activity while maintaining the most recent industry compliance restrictions. This can be accomplished manually, but time sinks and increased risks of inconsistent monitoring often lead groups to automate their CSPM with a CPSM solution.
Key Features and Functions of CSPM Solutions
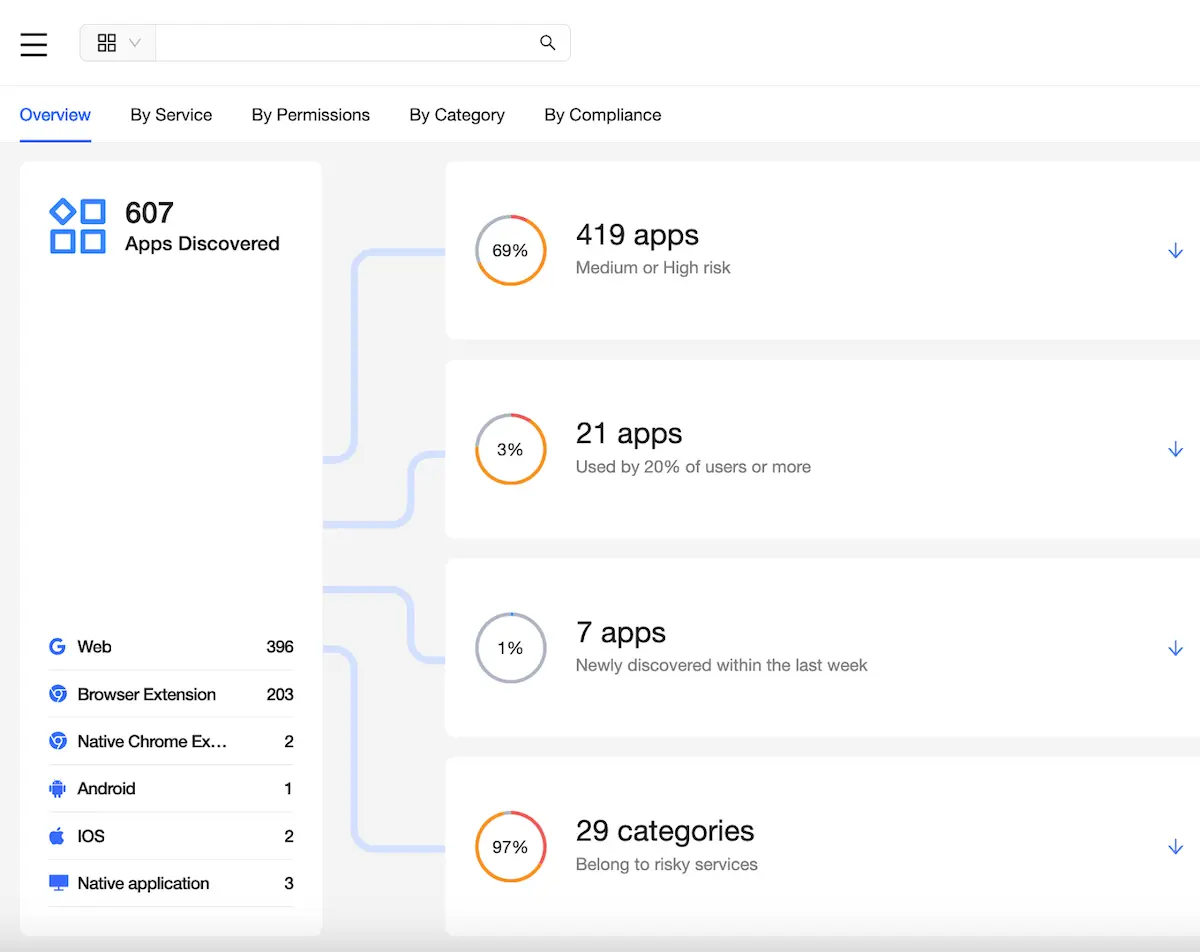
As a service, CSPM solutions offer a one-stop dashboard that increases visibility into cloud infrastructure and security configurations by continuously monitoring for any compliance or security threats that could put your data at risk, including:
- Misconfigurations
- Encryption settings issues
- Unauthorized access
- Compliance and regulation issues
- Anomalous traffic and insecure interfaces/APIs
- Improper use and configuration of identities and cloud permissions
- Account hijacking
Once a risk is identified, CSPMs will automatically create a report prioritizing vulnerabilities based on severity and offer remediation plans to security teams.
This level of automation and visibility makes CSPMs extremely powerful tools against cyberattacks. If you are interested in learning more about the importance of CSPM, click here.
What is SSPM?
SSPM are the actions organizations take to secure SaaS third-party apps existing outside the company’s cloud infrastructure.
Third-party SaaS applications like Slack, Salesforce, and Google Workspace have become critical to the operations of almost all businesses, and are fully developed apps managed and hosted entirely by the service provider.
This means businesses have far less control over how the product’s security is tuned.
Many require unique permissions and/or host critical company data, which can create several holes in a company’s security if not properly managed.
Salesforce, for example, is a third-party CRM application that houses countless data concerning a company’s sales funnel, sensitive client information, and login credentials. And while it is a valuable tool for any business, it also increases the amount of attack vectors a cyber criminal has to your critical data.
Each user has an account that needs to be monitored, and each account will have permissions to be regulated, creating various opportunities for data leaks and cyber-attacks.
Like CSPM, it is possible to monitor security protocols, configurations, account permissions, and industry compliance restrictions manually, but that also leaves the door open to inconsistent, time-consuming updates that may leave your organization vulnerable.
Because of this, businesses will often turn to SSPM solutions to help secure their data.
Key Features and Functions of SSPM Solutions
SSPM solutions offer the same automated routine security evaluations as CSPMs but are targeted towards integrated third-party apps.
Familiar features like a one-stop dashboard with automated security risk reports and continuous monitoring come together to increase a company’s visibility into its security posture while offering remediation plans to mitigate any discovered vulnerabilities.
SSPMs offer similar benefits to a company’s security posture by automatically detecting unsafe app configuration, checking for compliance issues, and evaluating any excessive user permissions that third-party apps may have introduced.
Differences Between CSPM and SSPM
While CSPM and SSPM share similar features, it does not mean they can be used interchangeably. Each has its distinct use cases that should be considered before partnering with either, or both, forms of protection.
CSPMs focus on evaluating security configurations across components within your cloud infrastructure for the many risks that occur within network settings, installed applications, user permissions, and compliance requirements.
SSPMs, on the other hand, are tailored to monitor each of the SaaS applications outside your cloud infrastructure. This requires SSPM solutions to be compatible with countless third-party applications and to live monitor them for their unique configurations, permissions, and compliance requirements.
So while a CSPM may not be able to examine security risks for third-party apps like Salesforce, if you are storing sensitive data or deploying customer-facing applications through a cloud service platform, a CSPM will have you covered.
Vice versa, SSPMs cannot protect you from data leaks across your cloud environments but can monitor and inform you of the risks across third-party apps like Salesforce, Slack, Microsoft 365 and Google Workspace.
It is important to remember, then, that the two do not oppose each other in their capabilities, and if you are storing data across your cloud infrastructure and SaaS applications, using the two in tandem is your best defense from data leaks.
Choosing Between CSPM and SSPM (Or Both)
If you are considering a CSPM or SSPM solution, the most important thing to keep in mind is your company’s current tech stack and how it manages and stores its data.
If your business only manages data across either a cloud service or SaaS applications, make sure you partner with either a CSPM or SSPM solution respectively that meets your company’s current needs.
However, these days most companies use cloud services and SaaS applications to operate their business. In this situation, where company information is inevitably shared within your cloud environment and across third-party applications, having CSPM and SSPM solutions is likely your only guarantee of fully securing your data.
Partnering with only one neglects the attack vectors of the other, and leaves you open to the risk of critical data loss.
How CSPM and SSPM Work Together
Because CSPMs can only protect data in your cloud infrastructure, and SSPMs protect only third-party SaaS applications, the two complement each other by fulfilling the security needs the other lacks.
If you are a company storing data on a cloud service platform and through SaaS applications, using both solutions in tandem is the best way to secure your data.
Future Trends in CSPM and SSPM
As CSPM and SSPM solutions continue to grow and meet more complex challenges, the integration of AI, quantum computing, and other emerging technologies will likely play a major role in powering each solution.
These new tools will allow security groups to predict anomalous behavior better, catch cyber attacks faster, and increase the depth and nuance of security reports and remediation suggestions.
Not only this, but each will likely see the continued adoption of Zero-Trust policies, forcing users to verify identities and privileges regardless of where requests originate.
Separately, CSPM solutions may begin to see use in “Internet of things” and 5G network management, while SSPM will likely continue to expand their integration abilities to ensure the coverage of all third-party applications.
As CSPM and SSPM solutions become more popular, each will have to continue to update and enhance their UI and dashboard experience and accommodate their growing customer base.
Conclusion
SSPM and CSPM each solve specific security issues depending on your digital integrations, and the choice between them is based on various factors.
An organization’s cloud adoption strategy, regulatory compliance requirements, and the complexity of its IT infrastructure all must be considered when choosing a solution, but if you have data stored on the cloud and through SaaS apps, you will likely require both tools to secure your data.
However, regardless of the solution chosen, prioritizing proactive security measures, continuous monitoring, and swift incident response will be paramount in safeguarding against evolving cyber threats and maintaining a robust security posture.
SpinSPM – A modern SaaS Security Posture Management solution by Spin.AI
SpinSPM is a SaaS Security Posture Management solution that provides full visibility and fast incident response for misconfigurations and Shadow IT, including third-party apps and browser extensions, to help IT Security teams reduce manual workloads while decreasing security, compliance, and data loss risks.
Enterprises can choose between two solutions:
- SpinSPM: SSPM functionality
- SpinOne: SaaS data protection platform that includes backup and recovery, ransomware protection, DLP, and SSPM.
Pricing
Request Pricing here.
What are the key features and functions of CSPM solutions, and how do they contribute to cloud security?
- Risk Assessment: CSPM solutions will scan your cloud environment for misconfigurations, improper account privileges, encryption settings issues, compliance issues. anomalous traffic, and insecure APIs and provide you with an overall risk score.
- Threat Detection: CSPM solutions continuously monitor for hijacked accounts, unauthorized data encryption and sharing to detect and alert to cyberattacks.
- Remediation: Along with your security score, CSPMs will offer you ways to resolve detected vulnerabilities
- Visibility: One-stop dashboards provide security teams a single source of truth into their security posture, allowing for increased efficiency when mitigating security risks
What are the key features and functions of SSPM solutions, and how do they enhance SaaS security?
- Risk Assessment: SSPM solutions will scan your SaaS apps for misconfigurations, improper account privileges, encryption settings issues, compliance issues, anomalous traffic, and insecure APIs and provide you with an overall risk score. Many SSPMs will also give a risk assessment for each third-party OAuth app found on the marketplace. Each SSPM product offers unique features. For example, SpinSPM is the only SSPM solution that also offers risk assessment for browser extensions.
- Threat Detection: SSPM solutions continuously monitor for hijacked accounts, unauthorized data encryption, and sharing to detect and alert to cyberattacks.
- Remediation: Along with your security score, SSPMs will offer you ways to resolve detected vulnerabilities
- Visibility: One-stop dashboards and heat maps provide security teams a single source of truth into their security posture, allowing for increased efficiency when mitigating security risks
What are the main differences between CSPM and SSPM solutions, and when should organizations consider using one over the other?
The difference between CSPM and SSPM solutions is the environment they monitor. CSPM solutions monitor the security posture of your cloud infrastructure and have no insight into the risks and vulnerabilities of your SaaS stack.
If you are a company solely operating a cloud service platform, stick with CSPM solutions to fill your security needs.
SSPM solutions, on the other hand, operate outside your cloud infrastructure to monitor the security posture of third-party applications like GoogleWorkspace, Microsoft 365, Salesforce or Slack.
If your company does not have a cloud service platform, and stores SaaS data solely through third-party applications, SSPMs will provide you with the security you need to keep your data secure.
How do CSPM and SSPM work together to provide comprehensive security for cloud and SaaS environments?
Because CSPMs only protect data in your cloud infrastructure, and SSPMs protect only third-party SaaS applications, the two complement each other by fulfilling the security needs the other lacks.
If you are a company storing data on a cloud service platform and through SaaS applications, using both solutions in tandem is the best way to secure your data.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Top 12 Slack Security Best Practices In 2024
Slack might feel like the digital version of your office break room with quick chats,...
Backup Microsoft: Securing Critical Business Data Across Microsoft ...
We all know Microsoft is a behemoth with all types of critical products used by...
Unpacking the Browser Extension Threat Model
Mastering the Balance Between User Empowerment and Organizational Security Web browsers are not just passive...