6 Tasks for Efficient Google Workspace Admin
- Google Workspace Admin Monitors Google Workspace Environments
- Google Workspace Admin Leverages Cloud IAM and 2-step Authentication
- Looks for Abnormal Behavior and Insider Threats
- Controls Third-Party Apps
- Implements Cybersecurity Protection in Google Workspace
- Implements Google Workspace Security Best Practices for Data Loss Protection
- Takeaways
- Frequently Asked Questions
Google Workspace Admin needs to provide a seamless experience for Google Workspace users. Simultaneously, they must protect cloud data from multiple threats. In our article, you will learn how to balance user experience with cybersecurity and be efficient in your tasks.
Businesses today are moving at a faster technical pace these days than ever before. This is largely due to organizations having access to public cloud infrastructure. This infrastructure is built on top of the most powerful technology companies in the world, including Amazon, Microsoft, and Google.
Google’s Workspace (formerly Google Workspace) environment offers businesses today a highly robust and powerful infrastructure. It also provides software as a service (SaaS) capabilities that would be extremely challenging for businesses to develop independently.
However, by leveraging Google’s powerful infrastructure and software stack, businesses can swiftly gain access to the same high-performance infrastructure that powers Google’s services. Moreover, they can seamlessly integrate with Google’s business services, including Gmail, Google Shared Drives, Google Calendar, and many other Google services.
Public cloud environments offer significant advantages and rapid time-to-value for organizations today. However, many businesses face challenges when it comes to swiftly retooling and rethinking their infrastructure management. Google Workspace is a behemoth suite of public cloud services that can be challenging for Google Workspace administrators who are only familiar with on-premise environments and have not had experience with public cloud administration.
However, it can also be a challenge for seasoned Google Workspace administrators to keep a handle on day-to-day administration. With that being said, what are the top admin tasks every Google Administrator should do?
Now, let’s explore a few essential best practices in Google Workspace administration that proactive and conscientious administrators should keep in mind. Additionally, we will see how utilizing Spinbackup to augment effective Google Workspace environment administration best practices makes this much easier.
Google Workspace Admin Monitors Google Workspace Environments
An effective Google Workspace monitoring strategy provides visibility to key performance and security indicators within the Google Workspace environment. Its basic monitoring will include keeping an eye on the following KPI’s in the environment:
- Users
- Security configuration, including Cloud IAM
- Storage
- Shared Resources (including sensitive data)
- Third-party Apps
- Cybersecurity events
Why is keeping an eye on the above aspects of the Google Workspace environment important? The above items, while not all-inclusive, represent some of the more major areas of day-to-day Google Workspace administration. This involves the daily activities of provisioning users and other resources, to keep an eye on security configuration and security-related events in the environment.
A good Google Workspace administrator keeps a check on the “pulse” of the Google Workspace environment. Any one of the above-listed areas of Google Workspace administration can have a significant impact on the overall health of the Google Workspace environment. It has the potential to either enhance or impede its performance.
Especially keeping an eye on Google Workspace security is important. Malicious attackers are focusing more of their efforts on cloud environments. This is because an increasing number of companies are now running business-critical applications and storing important data in the cloud.
SpinOne greatly enhances a Google Workspace administrator’s ability to keep a pulse on the Google Workspace environment. Google Workspace environments can be complex with hundreds or even thousands of users connecting from various devices all over the world. It is quite simply impossible for a human to filter through the mass of audit information to identify issues or possible security threats.
SpinOne provides powerful machine learning algorithms that work for the Google Workspace organization administrator 24 hours a day, 7 days a week. These algorithms continuously analyze the environment, detecting anomalies and monitoring other factors of interest without interruption.
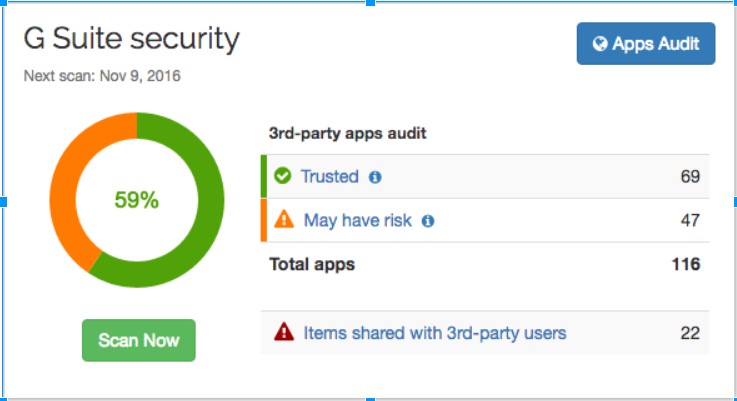
Google Workspace Admin Leverages Cloud IAM and 2-step Authentication
Proving identity and assigning permissions are fundamental tasks in administering any digital resource. These tasks apply to both on-premise and public cloud environments. Proving identity can be more challenging in public cloud environments because users access the system from multiple devices and network resources.
Google Workspace administrators should use Cloud Identity and Access Management (Cloud IAM) to secure their Google Workspace organizations. This is an important part of their overall security strategy.
IAM is the mechanism that allows organizations to manage access to resources by defining who has what access to which resource. There are many aspects of the cloud IAM that Google allows organizations to implement in the Google Workspace organization. However, below are a few of the benefits and features of Google Workspace public cloud IAM:
- Access control based on identity
- Permissions that are defined by roles
- Policies based on access requirements
- Single management interface to administer cloud IAM
- Auditing functionality
- APIs that allow automation
Cloud IAM helps organizations to effectively implement the idea of “least privilege” which means that a user has only those permissions that he or she absolutely requires to carry out their role.
SpinOne strengthens the cloud IAM mechanism for Google Workspace administrators. It enables easy implementation of certificate-based single sign-on functionality based on the blockchain. While certificate-based authentication is more secure than simple username/password authentication, it is generally complex and cumbersome to implement correctly.
However, SpinOne, with a few simple steps, allows organizations to quickly provision certificate-based single sign-on for access to Google Workspace resources. The signature of the certificate is stored across the blockchain. Due to its decentralized nature, the signature of the certificate is virtually impossible to compromise by an attacker, which adds a new layer of protection for identity management.
Google Workspace administrators also want to implement 2-step authentication. With 2-step authentication, users must use a secondary device, in addition to a password, etc, to prove their identity. Generally, this is a smartphone or other electronic device that will allow completing the 2-step authentication process. The 2-step authentication process makes it exponentially more difficult for an attacker to compromise security credentials.
Looks for Abnormal Behavior and Insider Threats
Administrators of any system today must be vigilant with regard to threats to data security. Data must be protected at all costs as it is typically what drives and fuels most businesses today.
Threats can come from any vector or weak point. Google Workspace administrators must keep an eye out for any abnormal behavior that may constitute a breach in security. This may even come from insider threats.
What would constitute abnormal behavior or threats to data security and potential data leakage? The following events would be events a vigilant Google Workspace administrator would keep an eye on.
- Abnormal logins (failed login attempts, or odd geolocation)
- Generally speaking, user activity stays within a certain baseline of activity. If a user account experiences an influx of failed login attempts or shows access from an unexpected geolocation, it may indicate an ongoing or attempted compromise of user credentials by an attacker. Prompt attention from administrators is necessary to mitigate potential security breaches.
- Abnormal data download or transfer of data
- Data leak is a serious danger to Google Workspace organization security
- Sensitive data detection and events
- Abnormal sharing of data
- Third-party access to sensitive data
Any of the above events could likely signal abnormal behavior that Google Workspace administrators would want to give immediate attention to. However, parsing events and audit logs to gain insights into potential threats is very time-consuming, and again, is really impossible for humans to do effectively.
With SpinOne’s API-based CASB Google Workspace administrators receive continuous machine learning-enabled protection and insights for the listed events and more.
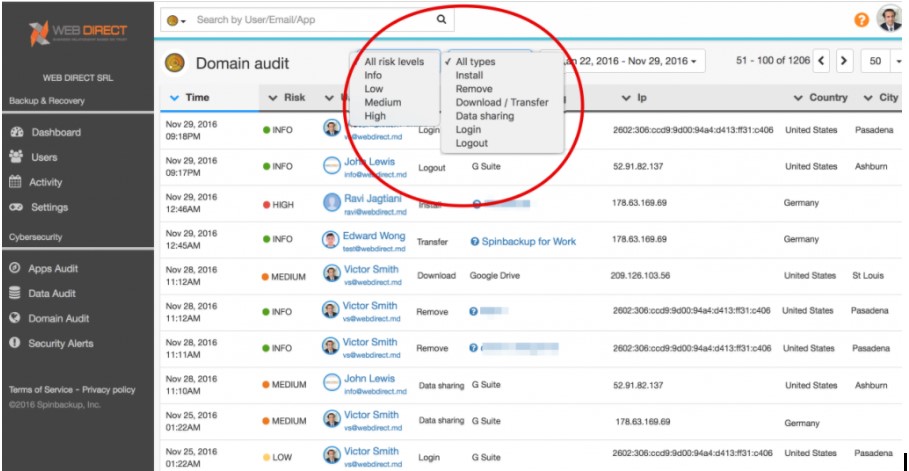
Furthermore, SpinOne offers powerful Domain Audit functionality, providing a comprehensive and centralized view of important events within the Google Workspace environment. This “single pane of glass” view encompasses a wide range of significant activities.
In addition, SpinOne offers real-time alerts to Google Workspace administrators regarding data leaks and other security events. This proactive approach enables administrators to respond swiftly and prevent potential security incidents, rather than reacting after the fact.
Controls Third-Party Apps
Third-party Apps that integrate into the Google Workspace environment provide tremendous value in extending the default functionality and features that are found in the Google Workspace environment. However, with the tremendous value they bring, third-party apps that are integrated within the Google Workspace environment can also pose a tremendous security risk to organizations housing data in a Google Workspace environment, potentially resulting in data loss or data leak of business-critical or sensitive data.
Controlling third-party apps that have access to this data is imperative. Third-party apps easily gain permissions to data, assuming the permissions of the user who is granting access. Most employees blindly allow permissions that are requested by an application (storage permissions, camera, contacts, etc).
Malicious third-party apps may even mask the permission set they are requesting. How can organizations control data access to third-party applications when access to these applications may be coming from BYOD devices or any number of devices and source networks?
Google natively provides basic whitelisting capabilities for third-party apps. You can allow installation of only white-listed apps, etc. However, there is no intelligence baked into the native solution.
What if a whitelisted third-party app starts exhibiting signs of risky behavior or data access not seen or noticed previously? If the app is whitelisted, it will have free reign over the data is has access to
SpinOne provides an intelligent solution to third-party apps control and Google Workspace security best practices that incorporates machine learning algorithms into the mix to profile application behavior and detect any change or anomalies in the expected behavior of the third-party app. This is a much more powerful solution to intelligently monitor apps rather than a simple whitelisting mechanism. SpinOne’s automated scan and apps control allow:
- Risk analysis
- Assessing the app and description of the app
- Permission levels that apply to the app
- Employees that are making use of the app
- List of connected devices that are utilizing the app
- Allows “blacklisting” apps
Additionally, the alerting mechanism that is contained within SpinOne allows proactive alerting of Google Workspace administrators with notifications and the ability to automatically revoke access based on “abnormal behavior”. Certain third-party apps may attempt to transfer data between public clouds the employees have access to or attempt to download Google Workspace data.
Spinbackup’s powerful Incident Response Plan includes these automatic responses to threat vectors that malicious or “leaky” third-party apps might pose. This proactive stance allows SpinOne’s third-party apps control to be a much more robust protection mechanism than the built in basic whitelisting that Google Workspace includes by default.
Implements Cybersecurity Protection in Google Workspace
Cybersecurity is a top concern among everyone today, including business leaders. It must be viewed as important! Cybersecurity is no longer simply an IT problem, but it is a real business problem. Businesses who fail to take it seriously won’t be in business long.
Many mistakenly believe that ransomware cybersecurity risks only affect on-premise environments and cannot target their public cloud environments or data. However, this is not true, as public cloud environments are also susceptible to such threats.
Organizations today with apps that synchronize on-premise files such as Google Backup and Sync can easily sync ransomware from on-premise file systems up to the Google Workspace public cloud. Additionally, if malicious third-party apps are connected to the Google Workspace environment, they can also be a vector for malware entering the Google Workspace organization. The problem with ransomware is that it silently encrypts files until announcing itself after the damage is already one.
SpinOne provides proactive Google Workspace ransomware protection that recognizes when files are being encrypted, blocks the offending process responsible for the encryption, and automatically restores the encrypted files that have been damaged from the latest backup! Effective cybersecurity also includes third-party apps control and insider threats protection as we have already mentioned.
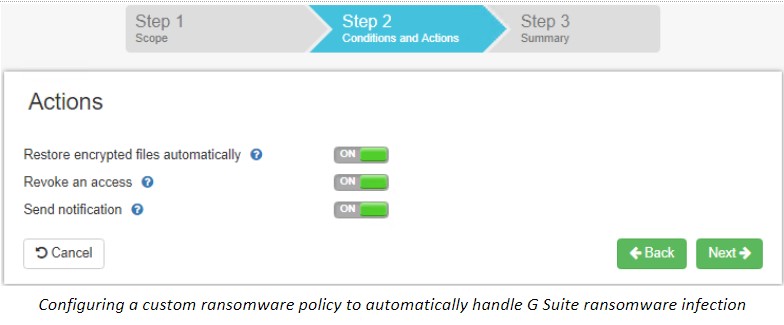
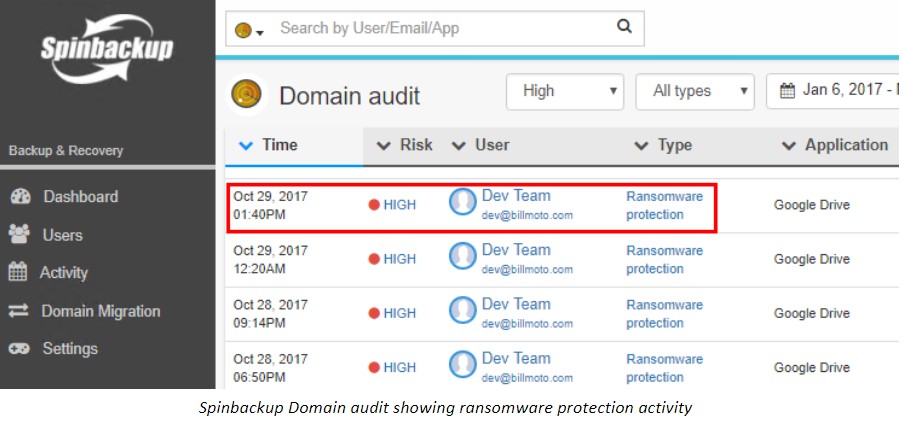
SpinOne provides proactive reporting on all cybersecurity-related events that allow Google Workspace administrators to stay on top of any event that is noteworthy. Additionally, Google Workspace administrators can enable aggregated reports or daily Google Workspace security reports. These reports provide a concise overview of cybersecurity events, helping administrators stay informed about the security of the environment.
Implements Google Workspace Security Best Practices for Data Loss Protection
Data loss protection (backups) is arguably the most important single mechanism that organizations can utilize to ensure that data is secure and protected. Public cloud environments such as Google Workspace are built on top of some of the most highly resilient infrastructure in existence today, is located in Google’s data centers. However, all the resiliency provided in the Google Workspace environment does not protect organizations from data loss as a result of end-users.
For example, what if end users mistakenly delete business-critical documents from their Team Drive? What if an end-user inadvertently syncs ransomware to the Google Workspace environment that encrypts Google Workspace files? What if an attacker gains access to data and is able to delete or otherwise corrupt files, emails, etc? All the resiliency in the world at an infrastructure level does not protect you against data loss at the hands of end-users, ransomware, or a potential attacker.
Google Workspace administrators must implement Google Workspace best practices for data loss prevention in their environment. Failure to do so will at some point result in data loss.
Google provides no easy built-in way for organizations to restore data in their Google Workspace environment. At best there is no assurance from Google that data can be restored. Your data is your responsibility and must be treated as such.
SpinOne provides tremendous value to organizations and Google Workspace admins to be able to protect their data in the Google Workspace organization – something that Google does not include. The data protection afforded by SpinOne allows customers to choose which resources they want to include in the backups (Gmail, Team Drives, Calendars, etc). The backups of Google Workspace captured by SpinOne include the following functionality:
- Automated daily backups
- After the first full backup, incremental backups are taken
- Data is encrypted in-flight and at rest
- Multiple versions of files are kept for a complete “versioning” system to restore the version of the file needed
- Data is stored in the Amazon public cloud so that reliance on the underlying Google infrastructure is not a requirement
In any organization, employees will come and go. Since public cloud billing is based on usage, efficient Google Workspace administration includes cleaning up user accounts that have left the company. However, what if the user account is tied to business-critical resources such as Google Analytics, Adwords, or other Google services? Simply getting rid of the user account may render services inoperable or unable to be managed or maintained.
SpinOne provides an effective way to solve both issues by quickly and easily migrating Google Workspace user data from the former employee’s account over to another account. This ability is based on SpinOne data protection that backs up Google Workspace user data. All emails and other data can easily be assumed by the new user account by simply selecting the different account during a restore operation.
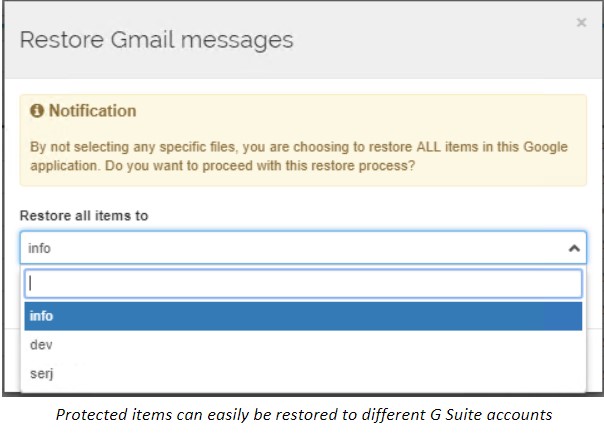
By migrating Google Workspace user data, the Google Workspace environment can be operated efficiently and in a lean manner without excess user accounts that are simply there for historical or service purposes.
Takeaways
Google Workspace is a powerful, agile, and robust platform for businesses today who are looking to scale into the cloud. Google Workspace administrators have a number of built-in tools that provide basic data leak and Google Workspace security functionality. There are a number of top Google Workspace administrative tasks that Google Workspace administrators will find themselves performing in day-to-day Google Workspace operations.
Among those responsibilities are:
- Monitoring the Google Workspace environment
- Implementing and administering cloud IAM and 2-step authentication
- Identifying abnormal behavior and mitigating insider threats
- Controlling third-party apps
- Implementing cybersecurity protection measures
- Ensuring data loss protection
- Managing the migration of former employee Google Workspace user accounts and data.
SpinOne equips organizations with powerful, machine-learning-enabled tools that enable them to efficiently perform these crucial tasks within the Google Workspace environment.
SpinOne’s value proposition is truly remarkable when you take into account that it offers a comprehensive package encompassing data loss prevention, data leak prevention, and intelligent machine learning-enabled cybersecurity product.
The “single pane of glass” administration dashboard enables ease of use and tremendous visibility for Google Workspace administrators. SpinOne offers a range of “Swiss army knife” functions for Google Workspace administrators. This makes it easy for them to take care of important tasks each day without difficulty.
Explore our new Google Workspace Security Features!
Frequently Asked Questions
How do I make Google Workspace super admin?
You need to sign in as a Super Admin to Google Admin console. Next, go Directory > Users. You’ll see a list of users. Click on the necessary one to open their page. Scroll down to Admin roles and privileges. Click on it. You will be redirected to the Admin role page. Super Admin will be the first on the list. Toggle a switch next to it, then scroll down and click save.
What does a Google Workspace administrator do?
Google Administrators are responsible for:
- configuring Google Workspace,
- adding/removing/suspending/archiving users,
- manage user data and groups
- controlling access
- Google Workspace security.
How do I work efficiently with Google Workspace?
As a Google Workspace Admin, you will have an overwhelming amount of daily tasks around configuration and management. To make your work more efficient, we suggest automating as many tasks as possible. For example, acquiring a third-party backup solution like SpinOne will help you prevent data loss, and having a SpinOne ransomware solution will automate your ransomware incident response and decrease downtime.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

